Supporting Large or Listed businesses
Is your company large or listed?
This month's fundamental topic
August 2025
Forensic Accounting
The importance of the expert witness role continues to hold its place in the arena of law. Ultimately, our role as experts is always to assist the Court. In particular, our role is to help the Judge reach a judgement they consider fair and equitable based upon the opinion offered by an expert, or experts, where the Judge may prefer the opinion of one over the opinion of another. It all boils down to evidence, reasoned arguments, and opinion.
The expert role will typically only be required where additional information is needed by the Court. If the matter can be dealt with by reference to the law alone it will likely not be needed, perhaps for civil matters such as a tenancy dispute or a contractual wrangle. Or rather, one of the Parties might apply to the Court to argue expert evidence is needed to allow the Judge to make an appropriate and fair judgement. This will be most relevant in areas such as medicine, accountancy, architecture and similar. The expert’s role can be summarised as follows: it is to clarify and simplify potentially complex issues within their field; and to provide objective opinion that is unswayed by those instructing or paying them.
However, by the very nature of how experts are appointed, with a party approaching them with a scope of work and typically agreeing a daily rate for the work to be carried out, there may be a subliminal leaning to seek a high bar (when acting for the Claimant) or to minimise the quantum of a claim (when acting for the Defendant). It is the strong expert who will advise a party, possibly seeking a high worth claim, that there will be little to no chance of success and to save their money. This may not be the news a client wants to hear, but anything less than presenting a case from an independent perspective will not help the client, or expert’s reputation, in the long term.
One of the processes designed to assist the Court is the joint statement – whereby experts look to narrow the issues they disagree on in a single standalone report – however this can sometimes turn out to be the ground where each party simply expands on the reasons they disagree with the other expert, which is of no assistance to the Court in reaching its judgment.
Many criminal matters may require a jury to decide the fate of a defendant, without any expert input. In other cases, there may be matters such as the Lucy Letby trial where expert medical evidence forms the heart of the case and which continues to draw media speculation for the roles of the experts in determining the guilt of the defendant, raising important topics around over reliance on limited expert findings, and the adequacy of ‘common juries’ in assessing complex industry evidence.
Experts are in a unique position, whereby they can support a client throughout all stages of a case matter, from initial advisory work, where Court proceedings may never even be envisaged, through to giving evidence in Court.
There is also the possibility of providing advice in any alternative dispute resolution process, be that at mediation (where cases sometimes settle) or some of form of expert determination, where the expert will effectively preside as ‘judge’ under joint instructions from both parties with rounds of submissions provided for their review.
Did you know…If an expert gives an opinion without any substantive evidence to support it, they can become the target of criticism from a Judge in their ruling which can seriously harm their reputation. If you would like more information on our expert witness services, please visit Forensic Services, or contact Martin Chapman and Alex Houston. |
Divya Devadoss, Associate Director, Forensic Services
As the corporate landscape becomes ever more complex with more convoluted organisational structures and reporting rules, the risk related to related parties increases.
A related party is a person or organisation that has a close relationship with a reporting entity, including close family members, subsidiaries, affiliates and entities controlled by related individuals. Such individuals or entities could influence or be influenced by the financial or operational decisions of the reporting entity. Related party entities can therefore pose serious audit and fraud risks, especially when used to manipulate financial statements or conceal misconduct.
What are the risks?
In the first instance, identifying all related parties can be difficult. Management may fail to disclose all related parties, making it difficult for auditors to identify and assess the impact. This can be particularly difficult as the definition of related parties can be complex and is not always fully understood by management and related parties are often undisclosed in good faith.
Transactions with related parties are inherently risky because they often lack the independence and transparency of arm's-length dealings.
Key risks include:
- misstatement of financial results: Transactions may be recorded at inflated or deflated values to distort earnings or asset positions
- conflict of interest: Decisions influenced by personal or financial ties can undermine corporate governance
- siphoning of funds: Companies may divert resources to related entities through loans, guarantees or asset transfers with little oversight.
These risks are exacerbated when internal controls are weak or when transactions occur outside the normal course of business. Auditing standards like ISA 550 require auditors to scrutinise related party transactions for legitimacy, business rationale, and proper disclosure.
This can have serious consequences for auditors. In one high-profile case, the Financial Reporting Council (FRC) issued a fine of over £1.3 million in relation to audit failures involving undisclosed related party transactions. A key finding was the lack of professional scepticism applied to management’s assertion that a delivery company, reportedly controlled by a close relative of the CEO, was not a related party. The case underscores the importance of rigorous scrutiny and proper disclosure in related-party dealings.
How can forensic accountants help?
Forensic accountants bring a specialised skill set to uncover and mitigate fraud risks associated with related party entities. Their contributions include.
Identifying hidden relationships
- Use corporate records, tax filings, and organisational charts to uncover undisclosed related parties.
- Apply data analytics to detect patterns of collusion or circular transactions.
Analysing transactions for fraud
- Examine contracts, invoices, and payment records for inconsistencies.
- Assess whether transactions have a legitimate business purpose or are designed to manipulate financial outcomes.
Evaluating internal controls
- Review the company’s policies for approving and disclosing related party transactions.
Recommend improvements to prevent management override and ensure segregation of duties.
Supporting legal and regulatory action
- Prepare forensic reports for litigation or regulatory enquiries.
- Provide expert testimony and assist in asset tracing and recovery.
Enhancing governance and transparency
- Advise boards and audit committees on best practices for oversight.
- Help implement whistleblower programs and fraud reporting mechanisms.
Conclusion
While related party entities are a normal part of business operations, they require rigorous audit procedures and forensic scrutiny to ensure they are not misused. By combining investigative techniques with financial expertise, forensic accountants help organisations maintain integrity, comply with regulations, and protect stakeholder interests. The Crowe Forensic Team handles a substantial number of forensic cases, varying in size and complexity. We are always happy to have an initial, no-obligation discussion on any matters where we can add value and provide expert advice. For more information, please contact Alex Houston or your usual Crowe contact.
Forensic expert witnesses are often involved in determining the profits lost because of the actions of another party. This is typically termed a loss of profit claim or, if the business has been discontinued for a period, a business interruption claim.
This can be viewed from the perspective of the party that has suffered the loss (Claimant), or the party that has allegedly caused the loss (Defendant).
Quantification
Whether defending or assisting in formulating the claim, a primary aim of the expert witness is to gain a sound understanding of the business. For instance, is it a manufacturing or service business, does it serve overseas markets, is it a seasonal business, and so on. The expert witness should also gain an understanding of how the business generates its revenues and profit streams. This will lie at the heart of determining the loss suffered.
The reporting aim is to quantify the position a business would have been in but for the actions of the Defendant, often described as the ‘But For’ Position.
It is important to consider each case on its own merits and what has taken place, for example:
- Has the entire business been impacted by the actions of the Defendant?
- Is it rather the case that only a particular aspect of trade has been disrupted?
- Is the loss of profit within a defined historic period, or is it continuing?
Typically, when instructed by a Claimant, the above information will be collated and, in conjunction with discussions with company management and independent review of the financial evidence, an expert report will be disclosed to the Court to assist in the determination of damages.
When acting for the Defendant, there would typically be a schedule of loss already disclosed within proceedings. This schedule represents the main focus in assisting the Defendant to assess the claim, as a review of this can unveil fundamental flaws in the case being brought against them.
Causation
One common area for all loss of profit cases is the matter of causation, that is, whether there is an identifiable link between a certain event, allegedly caused by the defending party, and the resulting loss of profit. A Claimant will typically point to a tail off in business, with declining revenue and profit streams, arising as a direct cause of the other party’s actions.
It can be the case, however, that any dip in a business’s performance is not necessarily a direct reflection of the actions of the other party, but is instead a result of trading conditions or events that lie outside the responsibility of the Defendant.
Part of the above review might also look more granularly at a business, breaking down its fixed and variable overheads. Certain costs will vary according to the volume of business, but costs such as rent, or rates, generally will not.
Mitigation
With every loss suffered, it is the responsibility of the Claimant to mitigate their loss; that is, to undertake reasonable actions to minimise the loss that it suffers. For example, could trade have continued on a different production line, or certain work been sub-contracted out to allow it to continue in some form and so minimise losses arising.
There can also be situations where a business actually does better as a result of an incident. Take the example of certain shops during Covid experiencing a surge in online sales and profitability as they stopped incurring property costs.
Did you know…In certain cases, a poorly formulated case or providing inappropriate or misleading evidence can see a party ordered to pay the other side’s professional costs of attending trial. |
Independence
Most importantly, it must be borne in mind that, whether acting on behalf of the Claimant or the Defendant on reviewing the loss of profit claim, an expert’s duty is to the Court rather than the party paying or instructing them. They must be seen to be acting impartially, and from an independent perspective, not impacted by the wishes and motivations of the client.
If you would like more information on our expert witness services, please contact Martin Chapman, Alex Houston or your usual Crowe contact.
As an expert witness, you might need to take on various roles in your work - as a party appointed expert; a single joint expert (SJE); a shadow expert; an expert issuing an expert determination; or an expert acting in a purely advisory role.
As a party appointed expert, your instructions come from one of the two parties (or possibly multi parties) that are in dispute, you will either be instructed directly by that party or (more commonly) by the solicitors acting as agent for that party – you may be acting for the party that ‘holds the information’ (e.g. the company’s remaining majority shareholders following a minority exit) or for the party that might not have as much access to information i.e. the exiting minority shareholder) – whichever party appoints you, however, your core responsibility and overriding duty is to the court - you must remain independent and be seen to be independent - the solicitor and barrister are advocates for their client, while the expert is there to give an independent opinion on accounting matters that lie within their expertise.
As an SJE, you are jointly instructed by both parties, this can actually take place in both ‘amicable’ and ‘confrontational’ scenarios, whereby friendly parties wanting to reach a settlement may agree to equally bear the costs of one expert; and similarly, where the parties are not on amicable terms, they may actually agree that their opinions are so polarised that it makes more sense to jointly appoint just the one independent expert to opine on the matter they are arguing over – however, if either party does not wish to show any form of ‘friendly’ co-operation then they are always more likely to appoint a party appointed expert, possibly in the mistaken belief that they may favour their position.
A common scenario arising from an SJE appointment is the position whereby a ‘shadow’ expert is appointed – this will be an instruction to review the work of the SJE and, although you are not part of the formal court process, your advice will be provided on the merits of the SJE report and where any questions may be raised on specific points.
An expert determination will usually come through an institute like the ICAEW, when parties cannot reach an agreement but do not wish to revert to long and expensive litigation – two rounds of submissions will be made by each party (their original arguments followed by their comments on the other side’s argument) and the expert witness will make a determination that is intended to draw a line under the matter and provide closure for the parties. Alternatively, we can provide advice to a party making their submissions.
In an advisory role the expert might typically be giving provisional advice as to the merits of pursuing a case, advice on how to calculate quantum, or reviewing the merits of a claim that a party is facing – this information would only be made available to the instructing party and would not be admitted into court.
Did you know…In whatever expert role you undertake, you must maintain your independence and base your opinions on the evidence available rather than the entrenched position of the party instructing or paying you. |
For more information, please contact Martin Chapman or your usual Crowe contact.
The preparation of an expert witness report is a crucial process, allowing the expert to assist the court by clearly summarising findings within their area of expertise.
Below is a summary of key information regarding the layout and content of these reports.
General
An expert witness report should provide a concise statement of facts and assumptions used by the expert. It is important that the reader can easily follow the expert’s reasoning leading to the conclusions reached. Any technical matters should be explained in terms that an intelligent layperson can understand. Additionally, the expert should include a summary of the instructions they received to avoid any potential misunderstandings.
Civil Procedure Rules
The report will serve as the primary piece of evidence provided by the expert to the court. As such, the Civil Procedure Rules (CPR) clearly outline what must be included in an expert’s report. It is essential to show that the expert is presenting their own independent professional opinion. Moreover, the CPR makes it clear that the expert’s overriding duty is to the court, not to the party who appoints or compensates them.
Format
- Be consistent with font size and colour: use a readable font and standard font size. Consider using italics to quote someone, bold to abbreviate names, and underline headings and subheadings.
- Resize your images: when adding images, resize them to be clear and visible and maintain consistency in sizing and positioning throughout.
- Number your pages: a table of contents is important for navigating through the report.
- Header: the header should contain the following information on all pages: case number, date, expert’s name and organisation.
- Use the “styles” feature in Microsoft: modifying the different styles can ease the preparation of the report and aid consistency throughout.
- Proofread: review paragraph markups, align your text and edit unreasonable gaps. Ensure tables and figures are aligned consistently throughout.
- Use a template: The Academy of Experts publishes a model template of an expert’s report which has been prepared and approved by senior judges. The template includes a mandatory declaration to complies both with the CPR and best practice.
Did you know…An expert may be employed in various capacities, including, arbitration, tribunals, and litigation. |
For more information on the forensic accounting services we offer, please contact Martin Chapman.
What better way for forensic accountants to get into the spirit of the Olympics than with an article intertwined with Olympic facts. Starting with fact number one which also provides an admittedly slightly tenuous link to expert determinations.
Did you know…The Olympic motto is “Faster, Higher, Stronger – Together”, with “Together” being a recent addition in 2021, to recognise that we can only go faster, aim higher and become stronger by standing together in solidarity. |
Expert determinations can be faster, higher, and stronger than other forms of dispute resolution. For more details on expert determinations, please see our other articles on What is an Expert Determination and Top 10 tips for a successful expert determination. However, in summary, this is a binding form of dispute resolution, usually used in a matter that is technical in nature (such as accountancy). An expert is jointly appointed by disputing parties to provide their expert determination to resolve the dispute.
Faster
Expert determinations are usually much faster than disputes that adopt more traditional legal claim processes. From the point of an expert being instructed, the matter can be resolved in as little as 20 to 30 business days. A typical timetable might be that the parties have five to 10 business days to submit their position to the expert, a further five business days for the parties to respond to each other’s submissions and then 10 to 15 business days for the expert to reach their determination. This process is flexible however, as the timetable and submission process can be adapted according to the needs and complexity of the matter.
Did you know…In the 2008 Beijing Olympics Usain Bolt won the 100m in a world record time of 9.69 seconds, despite his shoelace being untied. |
Higher
Expert determinations can often result in the successful party retaining a higher amount of any award granted. This is because the process can be highly cost-effective, as the parties typically share the costs of the expert determiner. This straightforward process means that there is minimal back and forth correspondence between the parties, and no need for an expensive trial in court, should alternative dispute resolution mechanisms fail.
Did you know…In the 1976 Montreal Olympics, the gymnastics electronic scoreboard could only display three digits, which meant that when Nadia Comăneci unexpectedly scored the highest possible perfect 10.00 score, the scoreboard instead displayed a lowly 1.00. |
Stronger
As previously mentioned, expert determinations are binding on the parties, making them a strong option to reach a full and final resolution. They are not open to challenge or any appeal processes, except in very strict circumstances, where it can be proven that the determination is incorrect due to either fraud or manifest error.
Did you know…Tug of war was contested at every Olympics from 1900 to 1920, with Great Britain being the most successful nation, winning two golds, two silvers and one bronze. |
Together
Our Forensic Services team have extensive experience of being both the expert determiner as well as assisting parties in preparing their submissions to the appointed expert determiner. For more information, please contact Martin Chapman or your usual Crowe contact.
Did you know…In the 1936 Berlin Olympics two Japanese athlete, Shuhei Nishida and Sueo Ōe, cleared the same height in the pole vault, being awarded silver and bronze. Being good friends, they had their medals cut in half, and fused into two hybrid half silver and half bronze medals, which became known as “The Medals of Friendship”. |
In cases where one side is aiming to make a claim — be it for loss of profits, breach of warranty, professional negligence, or similar — it can often be the case that such a claim may be overstated or exaggerated in some way, sometimes artificially and sometimes simply through an incorrect approach to formulating the claim.
Key themes to look out for, which may indicate an inflated claim, include:
- Cause and effect: possibly one for the lawyers to argue, but forming a claim without sufficient evidence to show it was caused by the actions of another can often undermine a claimant’s case. For example, would the business interruption have happened, from the actions of another party, or might those prejudicial events have happened in any event?
- Simple errors in supporting calculations: it is staggering how often you come across simple errors in claims, which inadvertently inflate a claim by an unreasonable sum and, in doing so, undermine the robustness of the overall claim.
- Using estimates when actual data is available: a claim should preferably be based on actual data that can be supported and verified, as opposed to budgets or estimates, although in the absence of ‘live’ data, sometimes budgets, forecasts etc., are the next best option.
- Claiming for something that cannot be justified: occasionally you see a claim where the facts suggest it does not hold merit, either an event just simply could not have taken place, or the timeline of the claim just does not make sense.
- Double counting: a common error in many claims is where an amount is double counted, possibly where a claim has been made, but inadvertently included two bases of assessment, which both fundamentally refer to the same income and/or profit streams.
- Lack of accounting for any mitigating income: a common error in claims where income has been impacted in some way but has led to the business looking for alternate ways of making income, which would not have arisen but for the breach complained – such mitigating income should be considered by a claimant and netted off the claim is to ignore that new income and not deduct it from the claim.
- A lack of a ‘sense check’: the first check that should be made when either formulating, or defending, a claim is whether it passes the ‘sniff test’ i.e., does this claim stack up based on the facts and data presented i.e., has the small corner shop that has been closed for a month, which now claims it has lost millions of pounds in business as a result, really suffered such demonstrable losses?
- Implausible, and unsupported, ‘what if’ scenarios: many claims will look at ‘the next steps’, but for the breach that happened, another stage of work and income generation would have followed - examples include suspiciously long-term renewal of contracts, and generously remunerated non-executive director positions.
- Costs that would have been borne notwithstanding the alleged prejudicial actions of the defendant i.e., there may have been an inevitable impact from the COVID-19 pandemic, the exit of the UK from Europe; or global economic conditions that would have impacted the position of the claimant in any event.
- Has the claim been set out that ticks all the boxes from an accounting perspective, has it followed generally recognised rules and regulations set out under UK and International accounting standards, or has it applied incorrect accounting treatment to inflate the claim.
For more information on the services we offer, please contact Martin Chapman.
Did you know…A poorly formulated, or incorrect claim, can cost a company significant management time, as well as incurring wasted Court costs. |
As forensic accountants, our involvement in the buying and selling of companies is usually required when something has gone wrong and there is a completion accounts dispute, earn-out accounts dispute or warranty claim. Disagreements in the interpretation of share purchase agreements (SPAs) can be the root cause of the disputed matters. Below we set out some real world examples, that based upon our experience, are best avoided.
Ambiguous and / or un-defined terms
We have been involved in matters where warranties have been agreed along the lines of company forecasts being ‘carefully’ prepared, or specific clauses inserted requiring ‘appropriate’ provisions for liabilities to be made.
Ambiguous terms such as these are unhelpful, as each party will undoubtedly have different interpretations as to what ‘carefully’ or ‘appropriate’ means in practice. Leaving room for the application of judgment in accounting practices can lead to vastly different conclusions as to the consideration due under an SPA.
Unrealistic warranties
A warranty we often see proposed at the SPA drafting stage, but thankfully is usually (but not always) removed in the final SPA is that “the management accounts have been prepared in accordance with Generally Accepted Accounting Principles (GAAP)”.
GAAP in the UK is typically FRS102 or IFRS , being the principals dictating how companies produce their annual statutory financial statements. Management accounts, while often having a significant grounding in GAAP in their preparation, are produced internally by a company to assist management in running the business. Differing reported financial performance can arise, for example, when management accounts use interim estimates, instead of detailed calculations that would be required under GAAP.
Having a clause in an SPA that warrants that the management accounts have been prepared in accordance with GAAP likely leaves a seller open to a warranty claim, because management accounts are very rarely, if ever, prepared completely in accordance with GAAP.
Lack of clarity on precedence hierarchies
SPAs typically have a hierarchy set out, that dictates how completion accounts and earn-out accounts are prepared. The most common hierarchy is:
- specific clauses in an SPA take precedence over
- historical accounting treatments in a company’s statutory financial statements, which in turn take precedence over
- GAAP.
We have seen examples where the wording as to the hierarchy applicable is unclear, which can result in buyers and sellers having vastly differing opinions as to how completion accounts or earn-out accounts should be prepared and ultimately the resulting consideration due.
Incorrect internal referencing
SPAs go through numerous different versions during the drafting process. It can be very unhelpful if a clause in an SPA, refers a different clause in the same SPA, but does not reference the correct clause number, or is referencing a clause that no longer exists, owing to drafting revisions.
In worst-case scenarios, this can make clauses have completely different, unintended meanings, resulting in buyers or sellers being unfairly financially worse off in terms of the consideration ultimately paid.
Post balance sheet events
Problems can arise if SPAs are silent in respect of defining a cut-off date for the admissibility of evidence for consideration, when preparing completion or earn-out accounts.
An example where a cut-off date could have a big impact on consideration due would be the parties becoming aware, after the completion or earn out accounts date, that a key customer, owing significant monies, has gone into administration. Without a defined evidence cut-off date in the SPA, disputes could arise as to whether it is correct to write-off these amounts owed in the completion or earn out accounts.
How we can help
Our experienced Forensic Services Team can assist advising, or acting as an accounting expert witness, for buyers and sellers in respect of completion account, earn-out account and warranty disputes. We can also perform the role of expert in expert determination processes (see our Top 10 tips for a successful expert determination article from earlier in the year).
For further information on our forensics services and how we can help you, please contact Martin Chapman.
Did you know…According to the Office for National Statistics, in the twelve months to 30 September 2023, 1,134 UK companies with a value of £1 million or more were acquired, 851 being acquired by other UK companies and 283 being acquired by foreign companies. |
Let’s start with the ‘fairy-tale’ scenario (a particularly appropriate phrase in the context of this article, as will become clear) that the parties are in complete agreement with the £100 million company value concluded by the forensic accounting expert, in which one of the parties holds a 20% shareholding.
At first glance, you would think 20% of £100 million; the shareholding is worth £20 million (applying a simple pro-rata calculation), but that may not be the case. Often, a ‘minority discount’ would be applied to this £20 million, to reflect that the 20% does not give the shareholder control of the company and the decisions made with regards to, for example, its strategy, investment decisions or its use of profits.
Depending on the circumstances, minority discounts can typically wipe out up to 75% of the pro rata value and this percentage can sometimes be even higher. In the context of this £20 million example, a 75% minority discount reduces the shareholding value to £5 million, so the legal arguments put forward as to whether a minority discount is applicable can make a huge difference.
Majority of the time, for this 20% shareholding to be worth the full £20 million, a judge would have to conclude that the company is a “quasi-partnership”, but in what circumstances can this conclusion be reached…
RM & TM [2020] EWFC 41
Take, for example, the Three Little Pigs and their renowned architectural design empire. Ignoring for a second the multiple accusations of health and safety breaches in the press (apparently straw isn’t a safe building material), using case law from RM & TM [2020] EWFC 41, a judge may conclude that a “quasi-partnership” is in effect:
“These are family businesses. The family is likely to act in concert on major decisions, such as sale…Their personal relationships are strong, with no evidence of major internal disputes or quarrels…This, in my judgement, bears all of the hallmarks of a quasi-partnership and I therefore will not attribute a valuation discount.”
FRB and DCA [No 2] BV17D16308 [2020]
A judge may reach a “quasi-partnership” conclusion in respect of The Seven Dwarfs and their international network of diamond mines. Case law from FRB and DCA [No 2] BV17D16308 [2020] is particularly apt given the dwarfs’ insular operations as a reaction to havoc caused when they temporarily let a certain Ms Snow White into their tight-knit organisation several years prior:
“This is the perfect example of a quasi-partnership to which a discount will not attach. I accept that if an outsider were to buy into one of these companies, he or she would expect a discount, but it is in my judgement inconceivable that any outsider would either be permitted ownership or be interested in acquiring it.”
Clarke and Clarke [2022] EWHC 2698 (Fam)
Finally, we highlight the ‘Bag a Royal’ dating app that is taking the world by storm, the latest in a long line of apps published by the well-known behemoths of software development, Cinderella, and the Fairy Godmother. Clarke and Clarke [2022] EWHC 2698 (Fam) would likely be cited in favour of a “quasi-partnership” in respect of this business:
In his oral evidence Mr Clarke stated that he has been trading with his partner, Mr Shadforth, for many years and he would imagine that they would always take decisions jointly.”
How we can help
As forensic accountants, our fully CPR Part 35 / FDR Part 25 compliant or advisory reports set out company valuations in simple and understandable language, showing both the pro-rata and minority discounted valuation of shareholdings as required. It is the responsibility of the parties’ solicitors to make their respective legal arguments as to whether a “quasi-partnership” is in effect, although we may be asked our opinion on accounting matters that might contribute to the conclusion as to whether there is a “quasi-partnership”.
For further information on our forensics services and how we can help you, please contact Martin Chapman.
Did you know…The largest known divorce settlement in the UK is £554 million, being that ordered to be paid by Sheikh Mohammed bin Rashid Al Maktoum to Princess Haya bint al-Hussein in December 2021. |
In the role as expert witness, every case typically starts with a potential instruction either from a firm of solicitors, a corporate entity, or an individual.
A vital first stage of accepting any instruction is to ensure that you are not compromised in your position whereby you must be, and be seen to be, independent. As such, there should not be any material relationship with the parties involved in the dispute that could create a scenario, whereby it appears you have reason to favour one side or the other. A typical scenario that might exclude you from acting on a matter is where your firm act as auditors for one of the parties, or you are personally connected in some way, in either a current or previous business relationship.
The principal way of checking that you are conflict free is to contact the partners of the firm, and should there be any overseas parties involved, a check will also be extended to overseas network offices. An internal check of your own firm’s database of contacts also helps establish that no conflicts exist.
Alongside this, there are certain cases that may need high level clearance from the firm - normally authorised by a small number of partners and senior management nominated to oversee the process – this would cover cases that might be seen as having a public interest perspective, relate to individuals or countries connected with political or civil unrest and/or the level of fees or amount in dispute makes heightens the risk of accepting the appointment. In these instances, the approval committee’s role is to safeguard the reputation of the firm and consider whether the proposed assignment should be undertaken.
Instructions provided to the expert witness would usually include the scope of work being requested (i.e. the work that is to be delivered), how that will be delivered (most commonly through an expert report compliant with either Part 35 of the Civil Procedure Rules, Part 25 of the Family Procedure Rules or Part 19 of the Criminal Procedure Rules) and will typically include the background to the case and a set of guidelines for reporting experts. It may also, at that stage, set out the court timetable, specifically when the report needs to be filed by, and may additionally include the deadline for any joint meetings and statements with the expert on the other side.
In response, an expert would issue their own terms of engagement which is the contract between them and the instructing party that forms the legal basis under which they will act as expert witness. This sets out which members of the team will work on the case and what their hourly charge out rates will be – where possible, a fixed cost of carrying out the work will be provided or, if the volume of work to be conducted is unclear or subject to variation, the terms might allow for charges to be made on a time basis based on those hourly rates.
The other essential element to an expert’s instructions are the timelines - when their report needs to be filed into court, and the various stages of review along the way that are agreed with the instructing party and may be set out in the terms of engagement.
Terms of engagement will also contain the general terms and conditions of business that apply to that expert’s firm, for any of the services it undertakes as a business and form an important legal part of the overall engagement, providing a safeguard for the commercial interests of the firm. This will also include a clause around the limitation of liability that the firm accepts in respect of the engagement.
Should any dispute take place at a later date – about the nature, scope or cost of the work undertaken - it will be the firm’s engagement terms that will act as evidence and, in that respect, their importance must never be underestimated or compromised.
For further information on our forensics services, and how we can help you, please contact Martin Chapman or your usual Crowe contact for more information.
Did you know…It is always worth knowing other expert witnesses to recommend should any issues arise that prevent your firm accepting instructions to act on a case. |
When working on expert witness forensic cases relating to commercial disputes, there are typically five stages that we could see across the life of that case, as outlined below.
- Our initial instructions and work
Every case will start with a set of instructions, most commonly from a law firm, and occasionally, by a company or individual. Conflict checks are executed first to ensure our independence, money laundering checks undertaken to review the integrity of the party instructing us, and engagement terms drafted to reflect our scope of work.
A meeting will then be held to discuss the availability of financial documentation, the scope of work, and any issues we need to be aware of.
Relevant accounting evidence to support a claim can be identified and advice given on disclosure requests to be made to the other side. -
Investigation and consideration
The substance of our work will involve some form of investigation, research, or analysis, with evidence obtained by reviewing a company or individual’s’ accounting records. Incomplete records might typically require further investigation and explanation.
Information from third parties such as banks, customers and suppliers can be useful third party, independent evidence, which can be reviewed to corroborate information seen elsewhere. Further information and documentation may be sourced from the public domain. -
Expert report
An expert report flows from our substantive work, in which a reporting partner will express a formal opinion. The report must comply with the strict requirements set out in the Civil Procedure Rules (CPR) and will ultimately be disclosed, should a settlement not be reached before trial. It’s vital the report be written from an independent and non-partisan perspective, with the ultimate objective being to assist the court.
Conclusions and opinions should be robust and supported by evidence, able to withstand cross-examination and critical analysis. -
Meeting with the other side
Where an expert is appointed by each side, a meeting of experts might typically be held, and a joint statement prepared to assist the court.
This joint statement summarises areas where the two experts agree, and disagree, providing further analysis where relevant. -
Pre-trial support and attending trial
Pre-trial support might include a conference with counsel, and assistance at mediation, while a trial might see the expert supporting the litigation process at court, by giving evidence in person. A forensic accountant can recommend areas of cross-examination to their side’s barrister, on the accounting evidence and can equally be cross-examined on their own work. The expert’s fundamental responsibility is to the court, and not his instructing solicitors.
How can Crowe help?
As highlighted above, commercial disputes can be a complex process. At Crowe, we have an experienced team of forensic accountants who can provide support at every stage of the process, and provide clear, concise advice.
Did you know…There are standard paragraphs which must be included in an expert witness report and templates for these can be found on The Academy of Experts website. |
Simply put, a business interruption is a period where you cannot conduct business as usual due to an unexpected event. If this event is because of the unlawful act by a third party (e.g., due to a breach of contract) or a force majeure event (e.g., due to natural disasters or pandemics), a business may be entitled to claim for their resulting lost profits.
To explore the challenges forensic accountants, encounter when it comes to quantifying such claims, below I consider the recent plight of Livchester United, the most successful ‘fictitious’ football team in Europe.
The flood
Despite being in the north-west of England, famous for its low rainfall, three years ago Livchester’s Oldfield stadium suffered a catastrophic flood, making Oldfield uninhabitable for a year whilst repairs were made. Thankfully, the club had insurance which covered not only the cost of repair but also facilitated a business interruption claim under the Act of God clauses.
The forensic accounting expert had a straightforward claim to quantify (albeit, evidencing and justifying such claims can sometimes be a challenge) and was able to assess Livchester’s lost profit by:
- assessing the profits Livchester would have achieved, but for the flood, had they continued to play at Oldfield as normal
- subtracting the profits that Livchester achieved during the year when they were thankfully able to groundshare with their archrivals Evchester City at The Goodihad Stadium.
The breach of contract
Having begrudgingly spent a year playing at The Goodihad, Livchester were outraged to find out that their Messaldo Stand (the main spectator stand at Oldfield, named after the club legend and the undisputed greatest player of all time), would not be ready for the contracted repair completion date. Livchester had to spend a further year operating with their ground capacity at only 70% of its maximum.
Again, the forensic accountant was on hand to quantify a business interruption claim, this time against the building contractor that had failed to complete the repairs on time. Whilst conceptually, the quantification was a similar approach as prior, comparing actual profits to a ‘but for the contract breach’ scenario, there were several complex circumstances the forensic accountant had to factor into their calculations:
- the return to Oldfield coincided with when Livchester were due to renegotiate significant sponsorship deals. Livchester’s negotiating position was weakened by the lower stadium capacity, meaning that sponsorship revenues were depressed
- Livchester had taken the repairs as an opportunity to build new corporate facilities in the Messaldo Stand. It was challenging to estimate the profits that these facilities would have achieved, as they had no historical record of success.
The compulsory purchase order (CPO)
As if that was not enough, the day after the Messaldo Stand reopened, Livchester received a CPO on Oldfield, as part of the UK Governments HS10 plan to provide the public with high-speed travel to Lands’ End. They had to relocate and rebuild a new stadium fifty miles away, which was very upsetting for the club and its fanbase, with the only silver lining being that Livchester received significant compensation from the UK Government for losing Oldfield as well as being entitled to the loss of profits from the resulting business interruption.
The complexity of the forensic accountant’s work increased further, having to consider similar issues to before, but also this time factoring in ongoing losses into the future. Livchester’s new stadium had a significantly smaller capacity (losing gate and hospitality receipts) and it lost some of its fanbase due to the geographical move, both of which limited how lucrative future sponsorship contracts would be.
How can Crowe help?
As highlighted in the above scenarios, assessing the quantum in a business interruption case can involve factoring in several complex hypothetical assumptions. As forensic accountants we are used to simplifying complexity, setting out reasoned logical and evidenced opinions and conclusions in a simple and straightforward manner.
For further information on our forensics services and how we can help you, please contact Martin Chapman
Did you know…The Association of British Insurers estimated COVID-19 business interruption claims in 2020 to be circa £2 billion. |
In reviewing a set of accounts in your role as an expert witness, it is often just as illuminating to see what is disclosed in the notes, in addition to the headline numbers contained in the primary statements.
Many notes are required under accounting rules, while some may be disclosed at the discretion of the directors, although a common approach (of private companies, listed company rules are more onerous) is often to disclose less rather than more. Some of the notes that an expert will have an interest in, whether it be for the purposes of a valuation or a loss or profits calculation, include (but are not limited to) some of the following areas.
Directors’ pay
This forms a key part of valuations, with an analysis usually forming part of most experts’ reviews, with a view to assessing whether these payments have been made at market rate or may need adjusting to reflect the true cost to any purchaser of the business – total remuneration is normally disclosed along with what the highest director has been paid – bear in mind a director’s remuneration package might include not only base salary but also bonuses, medical and car benefits, and pension scheme options.
Related companies
Disclosure often needs to be made around which transactions have been conducted with parties who are related and potentially not at arms’ length (i.e. not a sum that would be paid to / received from unrelated third parties), again potentially requiring adjustment in any analysis – a common adjustment is rent payable to a related party that might be understated and not at market rate.
Bank debt
Creditors less than and more than one year, relating to bank loans, will be shown in the notes and is an important part of assessing the debt a company has to service and whether that business relies on its own resources to support its working capital requirements or is more reliant on external funding.
Group control
Normally towards the very back of the notes will be disclosure around who the ultimate parent company is that controls the company, it may be the case that this company is the sole subsidiary of a non-trading holding company, or conversely could be one of many subsidiaries held by a large trading parent company with a wide portfolio of operations.
Post balance sheet events
Accounts are drawn up at a specific point in time, such as 31 March, 31 December etc and include the transactions, and year end balances, for that period (resulting in profit or loss, net assets or net liabilities) including the company’s balance sheet which is a snapshot of its financial position at a particular point in time. However, the accounts for a business are prepared after the period has ended and therefore, between the date of the accounts and the date they are signed off, certain events may take place that need to be disclosed, either because they provide further information about something that occurred during the period, or they represent a fundamental change in the nature, assets or debt of the business that merits reporting. Such an occurrence may be something like the sale (or purchase) of a business in, say July, when the company’s year end was March.
Accounting policies
At the start of the accounting notes will be a summary of the accounting policies adopted by the company – certain accounting standards allow an option (e.g. an asset depreciated on a straight line or reducing balance method) and this can have a material impact on the profits recorded by the business, therefore a good understanding of which accounting policies are applied may help in any analysis of that business. This may be particularly relevant to items such as revenue recognition, or businesses that operate long-term contracts.
Provisions
Many companies will disclose provisions, these are typically the Directors’ assessment of future payments due that are currently quantifiable (but not yet payable), and such a provision may be made in the accounts – such items may include provision for a potential tax charge, the costs of legal action, or non-payment of a material debt – certain provisions might be classified as a ‘contingent’ liability i.e. the profit and loss account won’t be impacted for the period but the nature and/or size of the matter is of such significance that disclosure is made in the notes.
For further information on our forensics services and how we can help you, please contact Paul Burchett.
Did you know…Private companies have nine months to file their accounts following their year end (although special provisions were in place during the COVID pandemic that extended this by a further three months). |
Untangling the knots between two parties at the end of a marriage can be a painful and complicated process. The recent high-profile case, Standish v Standish, has thrown the spotlight on this issue, in the context of matrimonial and non-matrimonial assets, with the importance of the source of wealth being a key battleground between the Parties, as the matter has passed through the High Court, Court of Appeal and UK Supreme Court.
The following fictitious divorce case between Jack and Jill, highlights how different assets and arguments might result in vastly different decisions by the Court, when distributing their wealth.
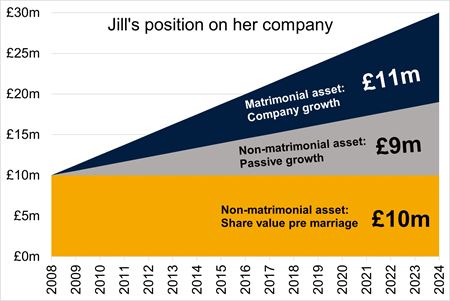
Jack, being the more eccentric of the parties, owned a 24-carat, bejewelled, solid gold crown (which ironically was once broken during an incident where he and Jill, his then fiancé, fell down a hill). It was straight forward for the Court to determine that this was a non-matrimonial asset to be retained by Jack, as he owned it before the marriage, with the crown just sitting in the attic amongst his equally flamboyant vintage waist coat collection during the course of the marriage. Jack was particularly relieved about this given that the crown had risen in value from £10 million at marriage to £30 million at divorce, thanks to the vast increase in the price of gold bullion since 2008.
Jill’s situation was more complicated however, as an asset she owned was shares in a bottled spring water company, of which she was the Managing Director (again ironically, the springs’ source is at the top of the hill that Jack and Jill took a tumble down, when the aforementioned crown was broken). Coincidently, the value of her shares in the company had also risen from £10 million at marriage to £30 million at divorce.
Jack argued that all of the growth in the company value since marriage (i.e. £20 million) should be shared equally between the parties, as Jill was only able to build up the company due to their joint, but inevitably different, efforts during their marriage. Jill thought this was incredibly unfair, particularly given the converse position with Jack’s crown where he massively benefited from the passive growth in gold bullion prices without any effort on his part.
Jill argued that some of the growth in the value of the bottled spring water company had happened passively without her efforts. She cited the trend of the increase in value of companies on the London Stock Exchange as evidence that companies are subject to passive growth, in the same way that commodities such as gold bullion are.
Jill calculated that had her company’s value grown inline with London Stock Exchange companies since the marriage, at divorce it would have been worth approximately £19 million; passive growth of £9 million since the £10 million valuation at marriage. Jill’s proposed that only £11 million of her company’s value was a matrimonial asset for sharing between the parties (£30 million company value, less £9 million passive growth, less £10 million pre marriage value).
As the below illustrations demonstrate, the contrasting positions held by the parties in respect of the bottled spring water company, could result in vastly different conclusions as to the value of the ‘matrimonial pot’ to be shared. The opinion of forensic accounting experts could be key to swaying the Court’s verdict on this.

How we can help
As well as providing the ‘usual’ forensic accounting expert witness services in respect of matrimonial matters, such as valuing shares, considering capital extraction from businesses and the corresponding tax implications, we are also comfortable dealing with niche areas that can pop up from time to time, such as passive growth, be that as a single joint expert, party expert or shadow expert.
As an expert witness, the preparation of a report is an important process to assist the Court by summarising findings within your area of expertise. Here are 10 top tips for preparing a good expert witness report.
- The report, if being disclosed in Court, must be compliant with the Civil Procedure Rules (CPR) i.e. compliant with Part 19 (Criminal), Part 25 (Family), or Part 35 (Civil) – this will include such things as including a Statement of Truth, and Declaration of Independence.
- An expert should stick to their field of expertise and not offer advice or opinion on areas outside of this – providing an unqualified opinion on something outside of your immediate expertise only serves to undermine the position of an expert.
- The report should be user friendly – remembering your audience will not necessarily be an expert in the accountancy field. There is often a lot of technical accounting jargon which a Court needs to understand, and sometimes a useful way to communicate this is to include a glossary at the start of the report.
- A good report will “signpost” early on the matters and issues which will be addressed within the report and, for more complex cases, an upfront executive summary may prove beneficial in setting out the conclusions reached, and the opinion of the writer.
- If a report is to include a large amount of tables / analysis, a common approach is to number these to allow quick and easy reference to relevant parts during expert meetings, or in Court procedures. Also consider placing discrete parts into an appendix to make the document more reader friendly.
- Any good expert report should be balanced and not overly weighted to the person instructing or paying them. The Court will give due credit for any points raised that do not necessarily support your instructing party’s case – this makes your report robust, reliable and independent in the eyes of the Court.
- A good report should be the opinion of the person signing it and they should know and understand all details within their report – if elements of the report are ‘over delegated' within the team this can make the expert’s position vulnerable when providing evidence under cross examination.
- A good report “tells the story” i.e. the issue(s) the expert has been instructed to address; the financial evidence that has been available to them; and the expert’s final opinion on the issues, based on the evidence available.
- The report should be clear on the sources of evidence relied upon e.g. company financial data; third party documentary evidence; or reported information from the management of the business – it is important to distinguish between what is the expert’s calculation / opinion, and what is information that has been provided by management.
- If an expert is in doubt as to the reliability of any evidence, they should be prepared to state this and comment that their opinion may change should such evidence turn out to be incorrect, or should further evidence be provided that might lead them to changing their opinion.
If you would like more information on our expert witness service please contact Martin Chapman.
Did you know…The Academy of Experts offers training, including a foundation course which includes report writing. Details of the courses offered can be found here. |
Intellectual property infringements are one of the instances where, as forensic accounting experts, we usually don’t get involved until after liability has already been proven. We are brought into the case knowing there is going to be some kind of award for damages, it’s just a matter of determining how much.
This article examines two of the possible routes that can be taken when quantifying losses, and has been written following a recent case in which Martin Chapman aided his client in receiving a landmark £13.4 million intellectual property infringement damage award, and £900,000 by way of costs (Geofabrics Ltd v Fiberweb Geosynthetics Ltd [2022]1).
Disclaimer: A fictitious case study is used below to demonstrate the possible proceedings following an incident of intellectual property infringement.
We address the case of Rugs Undermining Gravity Limited (“RUG”), a wholesaler of magical flying carpets, having its premier product the FlyRUG, infringed by Making Amazing Threads Limited (“MAT”).
RUG has a key decision to make, with two claim options available to pursue
- Loss of profits: Being the profits that RUG has lost as a result of MAT selling its infringing version of the FlyRUG, the SoarMAT.
- Account of profits: Being the profits that MAT has made as a result of selling the SoarMAT.
n.b. There is a third option available not covered in this article, involving the claiming of royalties.
RUG’s objective is to maximise the damages awarded to them, so what should they do?
Loss of profits
This requires RUG to estimate the additional profits they would have achieved, had the SoarMAT not been available (the “But-for Scenario”). This is where the forensic accountants will come to the fore as they will be able to quantify this, considering for example:
- whether RUG could have charged higher prices
- whether the growth in RUG’s business would have been bigger and / or faster
- how alternative non-infringing products such as the HoverBROOM, would have impacted market share differently.
While inherently complex, this approach has a key benefit for RUG, in that it is the owner of most of the information needed to compile its claim and thus is more able to influence the quantum.
Account of profits
This approach might be used where, for example, MAT is a much bigger brand than RUG and was able to achieve much higher profits than RUG would have been capable of under the but for scenario.
The forensic accountants will be helpful in quantifying these profits, as complex assumptions are involved when assessing which costs (or proportions of costs), are actually attributable to SoarMAT sales. Company overhead apportionment is often a significant battle ground here.
This option can be more straight forward as is based upon what actually happened, rather than the but-for scenario. However, RUG has the disadvantage of not being the owner of the information needed, and is thus reliant on MAT making adequate and accurate financial disclosures. RUG’s forensic accountant can assist in identifying any areas of disclosure that are lacking and critiquing the account of profits presented by MAT, offering their own opinion on quantum.
How we can help
We have a team of experienced Forensic Accounting Experts who are equally comfortable acting for claimant or defendant, providing expert reports and testimony to the Courts. If you would like more information on our services, please get in touch with Martin Chapman.
Did you know…According to an article 2 published by Wolters Kluwer, between 2000 and 2019 there were only four UK patent cases in which damages awards were made by the UK Courts, totalling about €1.6 million. This puts into context the magnitude of the recent £13.4 million award to Geofrabrics Ltd. |
1 https://www.bailii.org/ew/cases/EWHC/Patents/2022/2363.html
2Article published on the Kluwer Patent Blog, dated 13 September 2021, entitled "The Hit Parade of Patent Infringement Damages in Europe: France is Great (Again)" by Matthieu Dhenne, available at: http://patentblog.kluweriplaw.com/2021/09/13/the-hit-parade-of-patent-infringement-damages-in-europe-france-is-great-again/
As an expert witness it is important to demonstrate certain qualities, to assist the Court in making their judgment and to safeguard the reputation of both yourself and your firm. Below is by no means an exhaustive list but includes some of the more important qualities.
Knowing your duty
An expert witness’s overriding duty is to the Court and not the person instructing them or discharging their fees – independence, impartiality and integrity must be maintained notwithstanding any pressure that may come from solicitors, barristers or lay clients to influence your opinion or how the case may be presented.
Consistency
A Court will not look kindly upon any expert that changes their mind all too conveniently, or one that professes a certain approach in one case but then changes that drastically in another matter – if new evidence has arisen a Court will always accept that your opinion may have changed but someone who changes their opinion without due cause will have their credibility quickly undermined.
Fairness
A Court will give more credit to an expert that has considered the facts and evidence of the case without any bias towards his client – one method adopted by many experts is to produce a range of outcomes where the information available to them is not strictly ‘black and white’, providing alternate conclusions based on alternative assumptions. Credit will also be given where the expert accepts and amends their opinion where valid points are made.
Own your report
An expert who puts his name to a report must be mindful that the views and opinions expressed within that report are theirs, and theirs alone – a highly qualified, efficient support team may have assisted in drafting a high quality report but if the expert has not had sufficient input, or gained a detailed understanding on the matter, then their credibility could very quickly be attacked under cross examination.
A good story teller
Give the Court what they need – your accounting input set out in a fashion that sets out the key points, avoids confusing terminology or over complicated calculations, and ‘tells the story’ of what has happened, your opinion, and the key accounting points the Court needs to consider in making its judgement. A Court that doesn’t have to struggle to work out what you have written, and what your opinion is, may assist in seeing your evidence ultimately being favoured.
A good team
Behind every expert is invariably a hard-working team that supports the drafting of the report – ideally the expert will have a team that has a good blend of experience and specialist knowledge that they can draw upon to present the accounting evidence.
Quality
Underlying everything that is produced by the expert witness lies the importance of quality, both from the correct use of basic grammar all the way through to the final opinion you provide. Not only will this assist the Court and reinforce your position as a professional that can be trusted, but it will also see instructing parties refer further work to you.
Timelines
It is important that an expert witness delivers their work to the timelines set by the Court, which includes ensuring sufficient time is set aside for discussions with instructing solicitors and work is appropriately allocated to members of the expert’s team.
Global reach
If you work in a practice that has overseas offices, the option and benefit of having other colleagues from around the globe can assist on cross jurisdiction matters.
Referrals
Finally, a useful quality for any expert witness is to know other experts that cases can be referred to, should the case they have been asked to act on has a conflict to prevent them from acting, or requires a particular specialism which is more suited to another expert.
Further information
If you would like more information on our expert witness service please contact Martin Chapman.
Did you know…Expert witnesses can be subject to personal criticism in judgments made by the Court should the qualities they display fall below the standards expected. |
It is of vital importance, whenever considering making a financial claim in a legal matter, that relevant and sufficient accounting evidence is produced to support that claim.
A recent case
We have recently been involved in a case where the Claimant was seeking to recover damages from former directors of a Company that had been placed into liquidation. There were allegations that the former directors had under declared takings, and retained these personally, rather than recording them within the Company’s accounting records.
HMRC had previously investigated the Company and, at one point, its former advisers had sought to negotiate a settlement of the potential tax liability. The Claimant sought to use this correspondence as its primary evidence to prove that such under declaration of takings had taken place, and consequently the directors should be held to account for this amount of money.
We were instructed by solicitors representing two of the directors, to provide forensic advice, and undertook various exercises to assess whether there was any evidence that there had been an under declaration of takings. The records available to us, however, were very poor and broad brush assumptions had to be made.
This involved a critique of the business economics exercise HMRC had undertaken to create their original estimate of the level of under declaration. Key features included the amount of wastage in the sector and the level of customer complaints and credits/non payment of debts.
The Claimant decided not to adduce expert evidence in relation to demonstrating the alleged under declaration of takings, and proceeded to trial solely on the basis of the documentary evidence they had obtained.
At the Pre-Trial Review, the Judge expressed surprised at the lack of forensic accounting evidence, and, at the hearing, attempted to recreate his best assessment of what appeared to have taken place. It was gratifying to note that the thrust of his analysis mirrored that which we had previously prepared.
Summary
In summary, the Judge found that the Claimant had not discharged the burden of proof to establish that their allegations were properly made out, and awarded significant costs against them.
This case demonstrates the importance of assessing what evidence is required to be collated or adduced, in order to demonstrate that a claim has been properly set out, otherwise the consequences can be both costly and damaging.
Further information
If you would like more information on our expert witness service please contact Martin Chapman.
Did you know…It is often of benefit to approach a forensic accountant early in a case to identify how best to demonstrate the losses arising. |
Back in the day the expression “hired gun” was sometimes levelled at certain expert witnesses (and not just accountants) implying that they were singing to their instructing solicitor’s tune. However, moving into the 21st century and that expression has now thankfully fallen out of parlance. We as forensic accountants, in our role as an expert witness, recognise our duty and responsibilities are to the Court, and not the person instructing us or settling our fees. This can lead to tensions between us and the legal team in terms of their roles as advocates, and us as independent reporting accountants.
But ultimately, when litigation is in full swing, independence is at the heart of all the work we do and reinforces our credibility, being seen as the product of our own opinion based on the financial evidence gathered.
It does, of course, mean taking a strong stance if Counsel or instructing solicitors want you to adopt a particular approach which does not reflect your opinion. Being resilient is vital, both for your own reputation as an expert witness, and also for the legal team and their client, as independent evidence will gain more credibility from the Court than reports that are seen to be unfairly weighted towards the client. There have been several cases in recent years where we have been initially asked to discuss the merits of a claim, very sizeable in many cases, where our independence has led to advice that there is not a claim that can be properly supported, or that the claim as presented is nowhere near as large as initially considered.
Our independence is always checked at the outset through conducting conflict checks to ensure no accusation of bias, or “marking your own homework” can be levelled. For instance, if you are reviewing the accounts of a company that your firm has audited for many years, or reviewing the performance of a company one of your partners may have an interest in, or similar.
Ultimately, the Court wants an Expert Witness to assist the Court by providing a report that makes technical accounting jargon, or rules, easy to understand, provides the Judge with relevant information upon which to base their ruling, and for the report be unhindered unduly by the influence of the clients’ advocates or the parties contesting the litigation. Our duty is to assist the Court, be independent and be seen to be independent, serving as an aide to the Court rather than produce further conflict or confusion.
How we can help
We can help in relation to expert determination proceedings, and have considerable experience both as advisers to the parties, and of acting as the expert determining the dispute. If you would like more information on our expert witness service please contact Martin Chapman.
Did you know…That an Expert Witness’s duty, and responsibility, is to the Court and not the entity instructing or paying them. |
Expert determination is a procedure that involves a dispute, or difference, between two parties which are submitted to one or more experts who make a determination on the matter presented to them. The opinion reached is then binding on the parties, unless they both agree otherwise.
Top 10 tips to consider when carrying out an expert determination
- Do not enter the determination with any pre-determined views. The determination should be established based on the evidence produced and your opinion based on the facts and figures presented by the parties.
- At the outset, agree whether the determination should be ‘speaking’ or ‘non-speaking’. A ‘speaking’ report is set out in traditional format, with full details supporting your final opinion. A ‘non-speaking’ report means you show only your final opinion (i.e. ‘the shares are worth £x’), with no detail provided and no reasons given for that opinion – a ‘non-speaking’ approach can often be advantageous in bringing closure to a case for the parties without the need for protracted argument.
- Gain a good understanding of the underlying issue and the respective positions of the parties, it is also useful to know the source of information that the parties have used. For example, have they relied on management, draft or final audited accounts?
- Ensure the parties are fully briefed on the determination procedure and the process that will unwind in respect of when submissions are due. A timetable helps the parties plan and to move on with their existing businesses.
- Make sure the parties understand how many rounds of submissions will be made (normally two) and what they can, and can’t, comment upon – at some point representations must close and the parties thereafter should not be allowed to make further comment unless specifically requested by the expert.
- Allow each party to have the opportunity to make its fullest representations, ultimately a fair determination can only be reached based on full and open submissions made by the parties.
- Gaining third party evidence (to inform further on a certain industry, economic trend etc) may provide valuable additional information that either corroborates information submitted, or supplements it, and can provide valuable independent evidence.
- If required, seek additional legal advice to advise on matters such as shareholder agreement definitions, or other important legal angles.
- Determinations typically involve two rounds of submissions, and therefore a natural delay will take place, it is therefore important to schedule the work alongside other case matters, to enable work to flow smoothly and efficiently.
- Make sure the parties do not stray from the issues at hand and their submissions are focused at addressing the core argument, or dispute.
If you would like more information on our expert witness service please contact Martin Chapman.
Did you know…An expert determination is usually quicker, cheaper and less formal than arbitration or litigation. |
Forensic accountants are often instructed on professional negligence disputes.
In professional negligence cases the defendant may be a firm of solicitors, accountants, or architects that have previously provided some form of advice or work which is now alleged to have been below the standard expected, causing a financial loss.
The claimant must prove three areas:
- that a duty of care was initially owed by the defendant
- that duty of care was breached
- that breach was the cause of loss to the claimant.
The latter is a crucial part in any professional negligence claim as unless a direct correlation can be made between the negligent advice/work and any resulting loss, a Court is unlikely to find in favour of the claimant.
Our work and how we can help
There are two broad alternate aspects to any work we undertake – firstly reviewing the work undertaken by an accounting professional to identify whether it has been performed in an acceptable manner, or secondly reviewing the claim on the assumption that work was negligent but being instructed to assess any loss arising.
The test for professional negligence (e.g. an accountant) is fundamentally what you would expect a reasonably competent accountant to have done based on the accounting and auditing standards, generally accepted accounting principles, and practices that were in place at that time. It is not the case that you are giving an opinion on what you would have done at the time but rather, from your experience of conducting similar work and familiarity with other accountants’ work, whether you consider the defendant has carried out their work to a reasonable standard.
As the expert witness must have relevant contemporaneous experience, our forensic team will frequently work alongside experts from other disciplines within our firm to provide a seamless service.
In terms of any resulting award made by the Court, the defendant professional will usually carry insurance against such claims being brought against them and that insurance company will make the funding decision as to the appointment of an expert witness to prepare a report, based upon advice provided by the defendant’s solicitors. The financial consequences of a claim will depend upon the impact on the claimant’s business, but will frequently be assessed in the same manner as a loss of profit or business interruption claim.
Further information
If you would like more information on our expert witness service please contact Martin Chapman.
Did you know…Professional negligence is when a professional fails to perform their responsibilities to the required standard or breaches a duty of care, which results in financial loss, physical damage, or injury to a client / customer. |
There are various traits that are important to possess to enable you to represent your client in expert witness work. More importantly, the skillset is needed to deliver your prime responsibilities to the court, and ultimately lead to a fair assessment upon which the Court can make their judicial decision.
In years gone by, there was an overwhelming feeling - that ultimately led to reform - that experts were often regarded by those instructing them as ‘hired guns’, making the evidence fit the conclusion that would best assist their clients.
So what does it require to be an expert witness?
Our overriding duty is to the Court, and not the party instructing or paying us. Ultimately, we must maintain our independence notwithstanding any pressures exerted either from solicitors or lay clients. There have been various cases we have been instructed on where we have had to tell our solicitors – “sorry, but your case can’t be supported on the evidence available”, this is not what the solicitors or client may necessarily want to hear but to avoid such a conversation would be to undermine your own opinion and work.
At times solicitors may try and put some gentle pressure to change an opinion, or a working, but if you are clear that what you have concluded is (to your mind) correct, then your professional duty is to remain resolute.
Another quality required is consistency – a Court will not take kindly to an expert changing his mind with the wind, or worse still, expressing one opinion on a specific matter in one case, then at some point later addressing essentially the same matter but adopting a completely contradictory approach (with no good reason to do so). A Court will always accept if you have had access to new evidence which has impacted your opinion, but someone who is willing to change their opinion so easily is not a robust expert witness whose evidence will be accepted by the Judge.
Further, an element of fairness to any report, or verbal evidence given in Court, is key in supporting a crafted argument – if a report is totally weighted towards one’s own client throughout then it can bring into question the independence of the expert. One useful method adopted by many experts is the adoption of a range of conclusions, particularly when there is a monetary aspect, to give the Court an idea of what range the claim may lie within. This may be couched within terms such as if we assume ‘A’ the claim is £Y, but if we assume ‘B’ then £Z may be more appropriate.
An area in which an expert giving evidence at Court can undermine his own case is where the report may be absolutely fine, in fact it may be one of the best reports ever produced. But if that expert has overly relied on his team to prepare the report, and the understanding of its methodology and underlying assumptions is not fully understood or concluded by the expert, then the expert’s evidence will be quickly undermined under cross examination and a perfectly good report potentially made redundant.
It also helps an expert to be a good story teller – not making things up of course – but delivering a report that takes the reader (and the Judge) on a journey, where the issue is set out, and signposts set early on in the report for what is coming later. There is nothing worse for a judge than to have read a report and by the end be completely lost or confused as to what they have had actually just been told – wherever possible, the simpler and less technical the language, the better.
If you would like more information on our expert witness service please contact Martin Chapman.
Did you know…The Academy of Experts help you find a qualified expert witness to assist you on your case and also provide training courses for those who act as expert witnesses. |
One area where we often provide expert support is in the form of Expert Determinations (ED). ED is a procedure which involves a dispute, or difference, between two parties which are submitted to one or more experts who make a determination on the matter presented to it or them. The opinion reached is then binding on the parties, unless they both agree otherwise.
An ED can be beneficial to the disputing parties as it is less costly than going to Court, a faster process, is usually binding on the parties, and is subject to the opinion of an independent accountant who has no allegiance to either side.
The resulting opinion can take one of two forms – non-speaking or speaking. There are pros and cons associated with each. A non-speaking approach is exactly as it sounds, say a company valuation is being undertaken, the non-speaking opinion will state is that ‘the shares are worth £X’. There are no report details to be challenged and as such it is difficult to challenge the outcome, although one side will invariably be happier with the outcome than the other.
A speaking valuation is the opposite of a non-speaking valuation and will set out in detail how the value for those shares has been reached in a format more akin to a traditional report disclosed for Court. It has the benefit of covering the issues that may have been in debate between the parties, explaining why the conclusions have been reached. A speaking valuation may also raise matters which the parties wish to challenge that could end up protracting the process (for instance if they think something is factually incorrect). The threshold for challenging a determination on its findings is high, however, as the test is normally whether there has been manifest error.
We can be instructed either as the expert undertaking the determination or assisting one of the parties in preparing their submissions. If you would like more information on our expert witness service please contact Martin Chapman.
In simple terms, we are the numbers support service to litigious disputes, investigations or advisory work and are frequently instructed to prepare reports for Court on what can be very complex, or hotly disputed, accounting/number issues. Sometimes our work can be conducted on an urgent basis within a day, but often the work continues over many months, or even years. Although our clients will always want the best outcome for themselves, our responsibility as an expert witness is to the Court while if we acts as advisors we will present both the strong and weak points of a client’s case, possibly ahead of mediation or consideration of a legal claim. Our work can take us anywhere within the UK, and across any industry, while we also take on overseas matters due to our well established Crowe Global network of over 750 offices across 130 countries.
Our work is not supported by a portfolio of clients like it might be in audit or tax service line, each year a different set of challenges and scenarios is presented to us as we seek to assist our clients in either their dispute, investigation, or analysis. While not professing to be the ultimate experts in every field of industry, we need to be sufficiently capable of being able to quickly pick up how various businesses operate, and what are the real issues that will drive the case either at Court, mediation, or in other negotiations. While we always want to help our clients it is also important that we maintain an independent thought process which sets out the respective merits of a case, both good and bad from our client’s perspective.
The matters we work on are often diverse and regularly challenging, examples of the range of casework we have been instructed on include:
- Funding fraud alleged against a middle eastern bank and property developer.
- Major supermarket contractual disputes with suppliers.
- Defending an alleged associate of Bernie Madoff.
- Representing Premier League and Championship clubs in financial matters.
- Multi-million £/$ claims for wrongful trading.
- Valuations in partnership and shareholder disputes involving global companies.
- Reviewing the work of other accountants in professional negligence claims.
If you would like more information on our expert witness service please contact Martin Chapman.
Cybercrime
Most organisations are aware when they have been hit by a cyber attack. However, this awareness often does not extend to Advanced Persistent Threats (APTs). While your organisation's systems and networks may seem perfectly fine on the surface, hidden dangers could be lurking beneath.
APTs are sophisticated cyber attacks conducted by threat actors over an extended period, where they breach a network and maintain undetected access to information. By leveraging social engineering tactics, adaptive malware, and exploiting trusted systems, APTs can evade traditional cybersecurity measures. The longer an APT remains undetected, the greater the potential for financial, operational, and reputational damage to the organisation.
In 2024, one in four companies were the target of an APT, increasing by 74% compared to 2023. Additionally, around 50% of cyberattacks on supply chains were attributed to APT groups. Any industry can be a target of an APT, but organisations in the finance, healthcare, IT, and governmental sectors are predominantly targeted due to the sensitive information they hold.
Notable attacks by APT groups in 2024
- Lazarus breached the cryptocurrency company WazirX and stole USD 230 million.
- Salt Typhoon breached multiple telecommunication companies, including T-Mobile, AT&T, and Verizon, targeting customer call records and metadata.
- Star Blizzard conducted a widespread spear-phishing campaign targeting journalists, government officials, military personnel, and energy sector employees.
APT attack stages
Unlike most cyber attacks, APTs are not intended to cause immediate damage, but to acquire and maintain continuous access to sensitive information. APT attacks are conducted in stages.
- Reconnaissance: Attackers gather information on targeted individuals or organisations and identify network vulnerabilities.
- Infiltration: Once sufficient information has been obtained, attackers exploit the found vulnerabilities to gain initial access to the target’s network.
- Establish foothold: After initial access, attackers install backdoors and malware or use compromised user accounts to secure their access.
- Privilege escalation and lateral movement: Attackers will exploit vulnerabilities to gain higher-level permissions and move within the network to identify valuable assets while evading detection.
- Data exfiltration and cleanup: Attackers transfer the data from the targeted network and remove any digital forensic evidence of their presence.
Warning signs of an APT
While it is challenging to notice its presence within your system or network, below are some indicators of a potential APT attack.
- Increase in the prevalence of spear-phishing attacks.
- Persistent slow system/network performance despite resolution attempts.
- Suspicious network activity, large data transfers, and access to sensitive information.
- Increase in the prevalence of backdoor Trojans within your network.
Protecting your company against APTs
- Raise employee awareness through regular cyber training.
- Continuous network monitoring and vulnerability scanning.
- Protect sensitive data using access controls and encryption.
- Regularly update systems and software.
- Implement network segmentation.
- Implement endpoint security.
How we can help
Our Forensic Services team provide a range of services to help your organisation mitigate vulnerabilities and reduce the risk of attack. For more information on the services we offer, please contact Tim Robinson or your usual Crowe contact.
Did you know…Investment in APT protection is projected to reach USD 20 billion by 2027, representing a 365% increase since 2019. |
To those initially starting a business, it may seem that small start-up companies would not be an appealing target to cybercriminals. However, cybercriminals are targeting smaller companies as a gateway to larger organisations they may work and/or interact with.
Smaller companies are less likely to have considered cybercrime as a risk, and thus are less equipped when it comes to having security measures in place to detect, prevent and protect itself against potential cyber incidents. It is easier for a cybercriminal to infiltrate a smaller companies’ systems and networks, than it is with a larger organisation that will have a dedicated cyber security team, has extensive measures in place, and maintains certification to regulatory industry standards such as ISO 27001 and SOC 2.
What do start-ups need to be aware of?
The threat can be both internal and external.
The biggest internal threat is human error. While it is the intentions of some employees to inflict a cyber related incident, the majority of the time it is purely accidental. Research has found that 95% of cyber data breaches are caused by user error. Unsafe practices, and employee unawareness of cyber and information security threats, can leave an organisation – and its assets – vulnerable to cybercriminals. One of the most common examples is an employee accidentally clicking on and downloading a malicious file that then infiltrates an organisation’s internal network with malware.
In addition, external threats can put a company at risk on a regular basis, with statistics showing that 31% of businesses are targeted with a cyber attack at least once a week. Official statistics show that the most common threat vector was by far phishing attacks. Other threats include, but are not limited to ransomware, Distributed Denial of Service (DDoS) and Social engineering.
What’s at risk?
- Data – This can range from customers’ personal information, to information on employees and vendors. None of this information should be in the position to be stolen or leaked as it could destroy a newly formed company. The loss of personal and confidential data can result in losing customers, fines, and other risks listed in this section.
- Intellectual property – Intangible assets are just as valuable, and intellectual property can arguably be more valuable than personal data as it comprises so much of a business. Trade secrets can be revealed, resulting in major loss of any competitive advantage a start-up may have had.
- Company reputation – Research has found that 10% of start-ups have had to change the nature of their business following a cyber incident due to reputational damage. A cyber incident will have a substantial effect on the trust of customers/clients, partners and investors.
- The ability to operate – A cyber incident has the potential to cause significant damage to a company’s infrastructure and can hinder or halt the ability for a company to operate at all. This will also cause the company financial loss, from the cost of recovery, potential fines and business lost in the time the company’s systems were down.
What are some basic measures a start-up company should consider?
- Ensure the company complies with General Data Protection Regulation (GDPR) and the Data Protection Act (DPA).
- Cyber security and awareness training for staff.
- Multi-Factor Authentication (MFA).
- Password managers.
- Developing Information Security policies (and communicating it to staff).
- Anti-virus software.
- Internet security suite and firewalls.
- Install a VPN.
How we can help
We offer services that can help build your organisation’s cyber resilience. For more information on the services we offer, please contact Martin Chapman or a member of the Forensics team.
Did you know…That the latest Cyber Security Breaches Survey found that 82% of businesses reported cyber security as a high priority for senior management, but only 19% of businesses have a formal incident response plan. |
CaaS has allowed individuals with little to no technical expertise to carry out complex attacks, which has contributed to the significant increase in cyber incidents globally.
What is CaaS?
CaaS refers to the provision of cybercriminal tools, services, and infrastructure on a commercial basis, typically on the dark web. Just as legitimate SaaS platforms offer cloud-based software on a subscription basis, CaaS providers offer a range of products that facilitate various forms of cybercrime. These can include:
- ransomware kits: Pre-packaged tools that enable even novice hackers to launch ransomware attacks, encrypting victims’ data and demanding a ransom for its release
- phishing services: Ready-made phishing campaigns that can be customised and deployed to steal sensitive information from targeted individuals or organisations
- DDoS-for-Hire: Distributed Denial of Service (DDoS) attacks that can be rented to overwhelm a website or network, causing disruption or demanding ransom for ceasing the attack
- credential stuffing tools: Services that automate the use of stolen credentials to breach online accounts.
The impact of CaaS
The availability of CaaS has provided individuals with little to no technical expertise and the ability to carry out complex attacks, which has contributed to the significant increase in cyber incidents globally. The impact of CaaS includes the following:
- increased frequency and sophistication of attacks: With easy access to advanced tools, cybercriminals are launching more frequent and sophisticated attacks, overwhelming the defences of even well-prepared organisations
- diversification of targets: CaaS has enabled attackers to target a broader range of victims, from large corporations and critical infrastructure to small businesses and individuals
- challenges for law enforcement: The decentralised nature of CaaS, often based in regions with lax enforcement, makes it difficult for authorities to track down and prosecute the operators of these services. The anonymity provided by the dark web further complicates efforts to identify and these networks and prosecute
- economic impact: The costs associated with cybercrime are staggering. Businesses face not only direct financial losses from ransoms and fraud, but also significant expenses related to recovery, legal penalties, and reputational damage.
CaaS represents a significant evolution in the threat landscape, making cybercrime more accessible and potentially more damaging. As this model continues to grow, it is crucial for businesses, individuals, and governments to stay ahead of the curve by implementing comprehensive cyber resilience strategies to fight against cybercrime.
For more information on the Forensic services we offer at Crowe, please contact Tim Robinson.
Did you know…CaaS businesses are marketed and sold in a manner like legitimate businesses, with customer support, refund policies, user-friendly interfaces, and subscription models that allow cybercriminals to scale their operations easily. |
In recent years, the rise of cybercrime has posed significant challenges to institutions worldwide, with healthcare systems being prime targets. The recent cyber-attack on the National Health Service (NHS) is estimated to be its biggest leak of patient data in years, highlighting the escalating threat and severe implications of such breaches.
What has happened?
On Thursday 20 June 2024, Russian-speaking cyber-crime group “Qilin” uploaded 104 files containing almost 400GB of private medical data from several NHS London hospitals to the dark web. The group claimed to have stolen the data from Synnovis, a pathology laboratory which processes blood tests on behalf of the NHS.
The current statement on NHS England website details that the ransomware attack in which this data was stolen took place on Monday 3 June 2024, with the National Crime Agency and National Cyber Security centre currently working to verify the data included in the published files. Qilin had reportedly been demanding a $50m (£40m) ransom.
Since the hacking, the NHS has faced significant disruption; appointments have been cancelled, overall services interrupted and planned surgeries postponed. Hospitals and GP surgeries infected by the ransomware are estimated to only be able to carry out 30% of their usual number of blood tests. Additionally, it doesn’t appear that there will be a quick resolution, with the NHS acknowledging that “full technical restoration will take some time, and the need to re-book tests and appointments will mean some disruption from the cyber incident will be felt over coming months.”
What does this attack represent?
Cyber-attacks on healthcare systems like the NHS are particularly dangerous due to the sensitive nature and large amount of medical data they hold, and the critical services provided. When cybercriminals infiltrate these systems, they can disrupt hospital operations, delay medical procedures, and compromise patient care. Ransomware attacks, where hackers encrypt data and demand a ransom for its release, are especially disruptive. These attacks can cripple entire networks, forcing hospitals to revert to manual operations and risking patient safety. On top of this, the theft of personal and medical data can lead to identity theft and financial fraud, further endangering affected individuals. The potential for such data to be sold on the dark web only exacerbates the risks.
It is due to this potential significant and wide-reaching damage that the healthcare industry has become increasingly attractive to cybercriminals, who are eager to cause as much disruption as possible to ensure their ransom is paid. Evidence of this came last month, when the CEO of a top-10 Fortune 500 healthcare company confirmed they had paid a $22m (£17m) ransom in an attempt to protect stolen patient data.
This recent attack on the NHS highlights the growing sophistication of these types of attacks. Cyber criminals have evolved to employing business-like models that involve strategic planning, structured hierarchies, and advanced technologies. This development has enabled them to execute more large-scale and targeted attacks on vulnerable organisations like the NHS, who they see as more likely to pay the ransom. The financial motivation behind these ransomware attacks makes healthcare organisations a prime target for cybercriminals and represents a significant challenge for healthcare organisations around the globe. For more information contact Tim Robinson or your usual Crowe contact.
Did you know…Recent reports indicate that 81% of UK healthcare providers experienced ransomware attacks in 2022, a stark reminder of the vulnerabilities within the system. |
Cautionary tale as employee sends £20 million to cyber attacker impersonating boss
Modern IT systems are becoming increasingly sophisticated and inter-connected, largely due to the increase of devices connected to the Internet, also known as the Internet of Things (IoT), and the reliance upon extensive suites of software to perform essential functions for your organisation. As a result, the external attack surface in which hackers can exploit continues to grow, which can leave organisations exposed to a combination of risks, including data breaches, disruption of services, reputational damage, and potential fines from regulators. To mitigate the threats, we need to understand more about what the key vulnerabilities in external IT infrastructure are, and the potential implications if they are left unaddressed.
What are they key areas to address?
Out-of-date software - Vendors constantly release newer versions of products to ensure they fix any bugs and patch vulnerabilities. Once a piece of software becomes obsolete and the vendor stops releasing software updates, also known as end-of-life software (EOL), this can leave the organisation exposed to cyber-attacks and service failure.
Open ports - A 'Port' is a communication endpoint for software running on a computer network. Cybercriminals will scan for open ports at the early stages of a cyber-attack to identify ‘easy’ routes into the organisations. Regularly scanning for these open ports is essential.
Expired certificates - Domain certificates help ensure encryption on your website is up to date and provides end-users with reassurance that your website is safe. If the certificate has expired, major web browsers will display a security alert to visitors and may prevent them from reaching the site. If your organisation has any applications using this domain, then these will cease to function, which can lead to a disruption of your services. Not only does this introduce vulnerabilities into your external infrastructure, but it also damages consumer trust in your website.
What are the risks?
Data breaches - If hackers are successful in exploiting vulnerabilities in an organisation’s external infrastructure, this can leave your organisation vulnerable to a data breach. Hackers may seek to exfiltrate this data to sell on to other criminals for nefarious means, such as identity theft, or they may hold the data ransom in exchange for a payment. Alternatively, cybercriminals may seek to commit espionage to steal intellectual property.
Fines from regulators - If your organisation is part of a regulated industry, then a cyber-incident can result in large fines, not to mention the potential cost of investigating the incident itself. Therefore, proactively monitoring for vulnerabilities in your external infrastructure will help ensure your organisation uphold compliance with industry regulations and standards.
Disruption of services - Hackers may also seek to disrupt your organisation’s services, for example performing a distributed denial of service attack (DDoS). A DDoS attack involves a cybercriminal bombarding a website with web-traffic to temporarily, or indefinitely, suspend web services offered by your organisation, for example your website. The downtime because of this disruption to services can translate into lost productivity and revenue.
In conclusion, managing vulnerabilities in your external IT infrastructure is not just a matter of good practice, it’s imperative for business continuity, instilling consumer trust and preventing fines from regulators. Furthermore, an incident because of poor vulnerability management will undoubtedly have an impact on your organisation’s reputation. Prioritising vulnerability management is an essential part of any organisation’s cyber security strategy and will become increasingly important as the number of devices connected to the Internet continues to grow.
How can we help?
Our Forensic Services team provide a range of services to help you mitigate the vulnerabilities in not just your organisation’s external IT infrastructure, but also the infrastructure of your third-party suppliers. We can provide infrastructure scans, in addition to penetration testing and vulnerability management dashboards to help your organisation identify, manage and mitigate any threats that may arise. For more information on the services we offer, please contact Tim Robinson.
Did you know…End-of-life (EOL) software is when a product becomes aged and the vendor typically stops releasing security updates or fixes for bugs, for example old operating systems on your mobile phone. It is one of the most commonly exploited vulnerabilities by hackers. |
Cautionary tale as employee sends £20 million to cyber attacker impersonating boss
In this article we highlight the rise in the use of deepfakes to facilitate cybercrime. Public awareness of deepfakes has risen in recent years with a number of high profile examples reaching mainstream media. These deepfakes have tricked large swathes of the general public, proving just how believable the technology can seem.
Deepfakes are synthetic media created using Artificial Intelligence (AI) techniques, such as machine learning algorithms, to manipulate or replace existing audio, video, or images with highly realistic results.
Developments in AI are bringing enhancements in cyber security defences but equally posing a challenge as cyber criminals capitalise on the opportunities they present. The sophistication of attacks and speed by which cybercriminals can deploy them grows as computing power and AI advances.
Recently, there have been a number of celebrity and politically motivated deepfakes developed to create misinformation and spread a malicious agenda intent on reputational damage and harassment. Examples include voters receiving fake audio messages from Joe Biden persuading them not to vote in upcoming elections and AI-generated explicit images of Taylor Swift circulating on the internet.
The latest cautionary tale showing how cybercriminals are using deepfakes for social engineering attacks comes from an organisation based in Hong Kong. A member of the finance team in Hong Kong was tricked into sending £20 million on request of a deepfake from the CFO in the UK. The deepfake was delivered via a video conference call the employee received. He was initially suspicious of the CFO’s request to deposit 15 transactions into five local bank accounts. However, other colleagues joined the call and were supportive of the request.
The fraud was only uncovered when the employee later checked with other colleagues at their head office. Everyone the individual had talked to on the conference was completely fake and had been generated by AI learning from previously public images, video and audio footage of the colleagues. The deepfake call was also supported by additional phishing and social engineering techniques on WhatsApp and email. A particularly sophisticated and sobering insight into what cybercriminals can achieve relatively easily with the use of AI.
These examples highlight the diverse applications of deepfake technology and the importance of addressing the potential risks and ethical considerations associated with its use. As deepfake technology continues to advance, it's crucial to develop strategies for detecting and mitigating the harmful effects of manipulated media. It's essential for individuals and organisations to:
- raise awareness in your organisation about the existence and potential impact of deepfakes
- develop strategies for detecting and verifying the authenticity of media content
- implement security controls and measures to protect against social engineering attacks
- proceed with caution and verify any unusual request.
For more information on the services we offer, please contact Tim Robinson.
Did you know…Recent McAfee research states that nearly two-thirds of respondents cannot distinguish between a real voice and an AI voice. |
In the ever-evolving landscape of cyber threats, cybercriminals have increasingly turned to multi-layered attacks as a sophisticated and effective strategy to breach security measures. These attacks involve a combination of various techniques to penetrate an organisation’s defences, with the objective of causing extensive operational, financial, and reputational damage.
One common form of a multi-layered attack involves a blend of social engineering, malware deployment, and exploiting vulnerabilities in networks or systems. By using social engineering tactics like phishing emails, cybercriminals manipulate individuals into divulging sensitive information or unknowingly installing malware. This initial breach is then leveraged to plant malware that can exploit system weaknesses, gain further access or exfiltrate data.
Moreover, these attacks are not limited to a singular method or target. Cybercriminals often combine tactics such as a Distributed Denial of Services (DDoS) attacks, ransomware, and data exfiltration within the same campaign. This multifaceted approach amplifies the impact and challenges security teams to identify and mitigate the attack swiftly to resume normal business operations.
The diagram below shows how these cleverly orchestrated attacks can work in practice.
The financial impact of this form of attack can be the least of an organisation’s worries. There are often subsequent operational and reputational issues to address during, and in the aftermath, of an incident.
To combat such threats, organisations need a comprehensive cybersecurity strategy that includes robust firewalls, regular system updates and employee training on recognising social engineering attempts. This strategy should also ensure that if one line of defence is compromised, then there are additional measures in place as a backup to mitigate any threats.
How we can help
Prevention is always better than reaction regarding cyber threats. Our wide range of cyber security services that can be found here can help protect your organisation and reduce the risk of attack. For more information on the services we offer, please contact Tim Robinson.
Did you know…Only 49% of medium UK businesses have formal cyber strategies in place. |
The Online Safety Bill was introduced in the House of Commons on 17 March 2022 and is set to become law later this year. Despite controversy, its overarching aim is to make the internet a safer place (particularly for children), while maintaining freedom of speech. The Bill will achieve online safety through the implementation of safety laws; laws will criminalise fraudulent adverts and require sites to consistently reinforce its terms of service to members.
The Bill has five objectives:
- increase user online safety
- preserve and enhance freedom of speech online
- improve law enforcement’s ability to tackle illegal content online
- improve users’ ability to keep themselves safe online
- improve society’s understanding of the harm landscape.
The first of its kind, the Bill will attempt to transform the internet into a safer space by requiring tech giants to quickly remove any harmful or illegal content from their sites. The bill will impose legal requirements on the following entities:
- internet service providers allowing users to encounter content generated, uploaded, or shared by others
- Search engines enabling users to search multiple websites and databases
- internet service providers publishing or displaying adult content.
The Bill will also be imposed on providers of regulated services based outside of the UK that fall within the scope of the bill. For example, services that target the UK or have a significant number of UK users.
Those in scope will be categorised into three key categories, dependent on the amount of risk they pose. Larger/higher risk platforms will be placed into Category 1 (for example, those with a wide reach such as Facebook, YouTube, TikTok etc.), with smaller businesses being put into Category 2A or 2B. Thresholds for these categories will be set out in regulations by the Secretary of State.
The Office of Communications, more commonly known as Ofcom, has been appointed regulator of the Online Safety Bill. Ofcom will be setting out guidance and codes of practice on how companies can comply with the new legislation. Failure to comply with the legislation set out can result in the regulator imposing fines of up £18 million or 10% of the company’s worldwide revenue (whichever is the highest figure). Additionally, where applicable, criminal liability could fall on senior members of staff where reasonable steps have not been taken to prevent offences. Regardless, the penalty will be proportionate to the online service providers failures.
However, as previously mentioned, the Bill has not come without controversy and criticisms. Some of the main arguments consist of issues around data privacy and protection that will come with the need of age verification on particular platforms and the surveillance of encrypted messaging; how content will be monitored; and the fact that the bill focusses on addressing the risks after content is posted, as opposed to before.
For further information on our cyber services and how we can help you, please contact Tim Robinson.
Did you know…The Online Safety Bill initially started as the ‘Online Harms White Paper’ back in April 2019. |
At some point in your professional or personal lives, a hacker would have retrieved your login details from a data breach and attempted to access your accounts. In the corporate world, if your login credentials (or worse, admin credentials) have been stolen, this can offer an avenue into your organisation. Leaked login credentials become a particular issue if you do not update your password regularly, use a weak password, do not use multi-factor authentication, or use the same password across multiple sites.
Typically, hackers can get their hands on the credentials once an organisation has been breached. The login credentials are then either used by the hackers themselves or sold on the open / dark web as part of a bundle for as little as $10. The open web is a part of the internet which is public and viewable by everyone. The dark web is the hidden collective of internet sites only accessible by a specialised web browser. It is a subset of the deep web that is intentionally hidden and is often considered a hotbed for criminal activity. Dark web online marketplaces are used for buying and selling illicit goods, including compromised credentials.
Having your organisations compromised credentials on the dark web leaves you vulnerable to a variety of cyberattacks which could lead to identity theft and data breaches. Due to the covert nature of the dark web, many organisations are unaware that they have had their credentials compromised and are listed for sale.
Where is the breached data posted?
- Dark web
Compromised login credentials are most commonly posted on forums on the dark web. Cybercriminals will often post a ‘sample’ of the data that they’ve stolen as proof, before the payment is made. Huge data sets containing rich personal data, not just leaked login credentials, can be purchased for small sums. This data can then be used for further criminal activity, such as unauthorised access to company systems.
- Bins
Bin sites are temporary online locations where you can upload and store text. Pastebin services are often used for sharing data breaches as they support large text files, don’t require user registration, and allow for anonymous posting.
- Data Dumps
Data dumps consist of breached data pulled together from a range of online sources. This stolen data is often dumped in high quantities on various sites, including the dark web.
- Forums
Forums are often used to host discussions on potentially threatening topics across both the dark web and surface web, including sharing breached data. Examples of these forums include RaidForums and Dread.
- Social media
Social media sites including Reddit, Twitter, YouTube and Telegram are popular communication tools that are frequently used by cyber criminals to share and discuss data breaches.
What can I do to protect my organisation?
- Perform dark web credential scans every six months.
Data breaches are unfortunately a common place in everyday life, and it is essential for organisations to monitor the dark web for any potential leaked credentials. Due to the frequency of these breaches, your organisation should perform a dark web credentials scan at least every six months, or after any major data breach. - Enforce complex passwords on company systems which are updated at least quarterly, or after a breach.
The time it takes for cybercriminals to ‘crack’ passwords is significantly increased when passwords are made more complex. The methods cybercriminals use to crack passwords are becoming increasingly sophisticated, meaning they can crack even reasonably complex passwords quickly. For example, a seven-character password with letters, numbers and symbols would take seven minutes to crack in 2020 but just 31 seconds in 2022. You should use more complex passwords, for example using a ‘passphrase’ containing a string of random words, numbers or symbols. If this is too difficult to remember, then using a password manager can help. - Provide employee cyber awareness training to help prevent employees using company credentials for personal use.
You should encourage employees to refrain from using corporate emails for personal use. Employees may use the same login credentials for your company’s systems as they do for their own personal use, which could be exposed as part of a third-party data breach and be used to attack your organisation. Employees should be provided with cyber awareness training to help prevent this. -
Enable multi-factor authentication.
Enabling multi-factor authentication on your accounts adds an extra layer of security should a hacker steal your login credentials.
For further information on BYOD and our cyber services, please contact Tim Robinson.
Did you know…One of the largest data dumps to date included 2.2 billion usernames and passwords. |
Bring Your Own Device (BYOD) is a practice where employees use their personal devices, such as laptops, smartphones and tablets for work-related activities. Working remotely has been a key driver of this relaxed approach and as a concept it offers several benefits to organisations, such as flexibility and reduced costs. However, there are a number of security risks associated with BYOD that organisations need to consider if it is to be a viable solution.
Rewards of BYOD
- Flexibility and short-term wins through fast activation.
- Reduction in the organisation’s technology procurement costs.
- Reduction in technology maintenance costs.
- Convenience for employees using technology they feel comfortable with.
- Increased productivity.
Risks of BYOD
- Security risks such as unauthorised access or data breaches could arise if devices are lost, stolen or compromised.
- Personal devices may not have the same level of security and be kept up to date with the latest security patches, firewalls or antivirus software, posing a risk to attack.
- Employees could unintentionally or maliciously share sensitive information through unsecure apps or communication channels.
- BYOD can complicate data compliance considerations.
Is it still worth the risk?
Ultimately the risk-to-reward ratio of BYOD depends on the nature of the organisation, the sensitivity of its data and its ability to implement robust security measures.
To mitigate the risk from BYOD, there are a number of considerations that should be addressed.
- Establish clear policies that outline the acceptable use of personal devices.
- Secure the organisation’s network by implementing strong access controls and use a VPN to establish secure connections when accessing company resources remotely.
- Ensure that personal devices are kept up to date with the latest security updates to address vulnerabilities.
- Educate employees about the risks associated with BYOD and provide guidance on best practice.
- Put technical controls in place and segment personal and company data on devices if possible.
- If possible, implement mobile device management solutions to help manage personal devices. This allows for pushed security updates or even remote wiping of data in the event of an incident or lost device.
For further information on BYOD and our cyber services, please contact Tim Robinson.
Did you know…A study from Cisco suggests that companies that favour BYOD make a saving of $350 per employee, per year. However, what are the operational, legal and reputational issues from one successful cyber attack or data breach? |
Recent years have seen a sharp rise in ransomware, with research showing that this trend is likely to continue in 2023 as attacks become increasingly more sophisticated. Thales’ data threat report found that nearly half (47%) of IT professionals surveyed believe that security threats are increasing in volume or severity, with 48% reporting an increase in ransomware attacks.
So, what exactly is ransomware and how does it work?
Ransomware is a type of malicious software that encrypts a victim’s data (whether that’s an individual or an organisation) and demands payment in exchange for the decryption key. This makes the data inaccessible until the ransom is paid to the attacker. Ransomware attacks can be devastating for organisations, having the potential to cause financial losses, reputational damage and even legal consequences.
Ransomware works by infecting a device or network and it does this through a variety of methods, some of the most common are phishing emails, software vulnerabilities and malicious websites. Once the ransomware is installed on the victim’s system, it begins to encrypt files and folders, making them unreadable. The attacker then usually displays a message on the victim’s screen informing them that they will only receive the decryption key if a payment is made. If the sum is not paid, the attacker often releases the personal and sensitive data it has accessed.
The attacker typically demands payment in cryptocurrency, which makes it difficult to track and recover the funds if the victim makes the payment. It is widely reported that organisations should never pay ransomware attackers; those that do pay place a target on their back by demonstrating to attackers they are willing to pay.
How big is the risk?
Ransomware has become a significant problem around the world; The 2023 Global Ransomware Report found that over 80% of its surveyed cybersecurity leaders and decision-makers say they are “very” or “extremely” concerned about the threat of ransomware. Between April 2022 and March 2023, the UK was the second most attacked country in the world. The risk of ransomware around the globe remains high and this is especially true in the UK and US.
Notable recent attacks in the UK that demonstrate the severity of ransomware include the August 2022 attack on the NHS – which is the biggest employer in Europe – and the January 2023 attack on Royal Mail. The Royal Mail attackers demanded the largest known ransom sum ever: $80 million. When this was not paid the attacker then published the files stolen from the company.
Who's at risk?
As ransomware attacks become increasingly common, organisations of all sizes and within all industries are at risk. This risk, however, is considered higher for some areas:
- educational institutions. The education sector in the UK continues to be a sector that is increasingly appealing to attackers. This is credited to educational institutions often having a large number of entry points, weaker cyber defences and the large amount of personal data they store on students and staff, including financial information.
- healthcare institutions. Similar to educational institutions, the vast amount of personal and sensitive data the healthcare sector holds makes these institutions a popular target. They often also have complex IT systems with multiple entry points.
- financial institutions. Banking, credit and financial organisations are a target for obvious reasons – they hold vast amounts of personal and financial information.
- government institutions. Government agencies store sensitive information such as personal citizen data and confidential government information. They are often targeted by attackers trying to make a political statement or by foreign powers looking to spy on other governments.
How we can help
Prevention is always better than reaction regarding cyber threats. Our wide range of cyber security services that can be found here can help protect your organisation and reduce the risk of attack. For more information on the services we offer, please contact Tim Robinson.
Did you know…Between April 2022 and March 2023, the UK education sector was the target in 16% of known ransomware attacks in the UK, but only 4% in France and Germany, and 7% in the USA. |
As technology continues to advance and our use of it evolves, so does the threat of cybercrime. Criminals are constantly adapting to new methods that take advantage of our increasing dependence on technology. One report found that 85% of UK organisations suffered from a successful cyberattack in 2022, while research has found that in 2021 there were 4,783 victims of cybercrime for every one million users in the UK, more than any other developed country. Statistics not only highlight the alarming rate at which cybercrime is growing, but the adaptability of cybercriminals. In 2020, malware attacks increased 358% compared to 2019 as criminals took advantage of businesses moving to remote work environments.
The unique and evolving threats of cybercrime have resulted in traditional cybersecurity methods being unable to keep up, and increasingly there is a reliance on artificial intelligence (AI). AI, defined as intelligence demonstrated by machines, presents unique opportunities for businesses to protect, detect and respond to cybercrime. This isn’t going unnoticed by organisations, as one report found that around 79% of UK companies now favour security methods that utilise AI. To understand the range of ways AI is transforming cybersecurity, examples of how it can be successfully incorporated into cybersecurity practices are discussed below.
Examples of AI in cybersecurity
- Faster network threat identification
An AI-powered network security system presents the opportunity to monitor all outgoing and incoming calls and detect any suspicious patterns in traffic information at a much more accurate and faster rate than it would take humans. Darktrace, a platform that uses AI network security to detect and respond to threats faster than humans, is an example of this. It runs 24/7 and is continuously learning from real-time data in order to prevent insider threats, detect attacks, and identify zero-day strains of malware and ransomware. - Predicting cyber-attacks
Predictive AI in cybersecurity can help estimate when a breach will occur, predicted cost of losses, and what makes up those costs. Being able to predict and quantify the likelihood of a breach enables an organisation to implement the relevant steps to prevent it, while also using the information to help configure and enhance controls and processes to improve an organisation’s cyber resilience. - Data recovery
As the mass and value of data that organisations hold only appears to be growing, AI can assist in backing up and securing data in new, more reliable ways. AI in data management usually adopts a preventative rather than reactive approach, with the focus on identifying the issue before the data is lost and relying on AI-driven automated backups to protect the data. AI is, however, also providing solutions to complex data recovery problems, making decision making easier in the event of a disaster and assisting incident-response teams in automated accident recovery.
Is AI a one-size-fits-all solution for cybercrime?
Despite the growing use of AI in cybersecurity and the unique benefits it offers, the simple answer to above question is most definitely no. AI has not only transformed the cybersecurity industry, but has helped cybercriminals launch more sophisticated attacks and create new methods of attack. Our previous Forensic Fundamentals article titled ‘Future frauds and cybercrimes’, which can be found under the ‘Fraud’ section of this page, discusses the threats AI poses to cybersecurity and the fraud landscape in further detail, but a brief description of some of the new dangers it presents include:
- deep fakes, a type of artificial intelligence used to create convincing images, audio and video hoaxes are becoming much more widespread. These can be used to impersonate a CEO, for example, and getting company funds diverted into a criminal’s bank account
- AI being used with malicious intent, such as identifying patterns in computer systems that reveal weaknesses for cybercriminals to exploit, or to generate mass phishing emails that are often more sophisticated than human issued ones
- more advanced malware, such as using AI designed malware that is constantly changing to avoid standard cyber security detection methods.
Being overly reliant on AI in cybersecurity also comes with its own risks, such as bias and discrimination in decision-making and a lack of transparency. So, while AI can add tremendous value to cybersecurity measures, it is important to understand that it also presents its own problems. Nonetheless, AI’s growing ability to build predictive capabilities and strengthen defences offers some hope for the future of cybersecurity in keeping up with cyber criminals.
For further information on our cyber services and how we can help you, please contact Tim Robinson.
Did you know…An AI password cracker ‘PassGAN’ has the ability to guess over half of common passwords in 60 seconds. |
What is CMMC?
CMMC 2.0 is a new US Department of Defence (DoD) program that will require defence contractors to prove their cybersecurity maturity. Contractors will be excluded from forthcoming DoD contracts until they demonstrate compliance with one of three maturity levels.
The US DoD established CMMC as a baseline for measuring and implementing cybersecurity across the defence contracting community.
Features of CMMC
The CMMC 2.0 program has three main features.
- Tiered model: Defence contractors who are entrusted with national security information must implement cybersecurity standards at one of three maturity levels, depending on the type and sensitivity of the information.
- Assessment requirement: Contractors will be required to undergo an assessment to demonstrate compliance with defined cybersecurity requirements. The requirements increase in number and scope with each maturity level.
- Implementation through contracts: Contractors will be required to achieve a particular maturity level as a condition of contract award.
CMMC maturity levels
The CMMC framework is mapped to three maturity levels.
- Level 1 – Foundational: Each defence contractor must employ basic cyber-hygiene practices, such as ensuring employees change passwords regularly to protect DoD contract information.
- Level 2 – Advanced: The contractor must have an institutionalised management plan to implement CMMC’s requirements. The cyber management plan must be developed from the requirements outlined in a document known as NIST SP 800-171.
- Level 3 – Expert: The contractor must meet level 2 requirements, as well as demonstrate the capability to detect and respond to advanced persistent threats – malware that typically originates from nation states or state-sponsored groups.1
CMMC timeline
Though the Pentagon is in a rule-making stage about CMMC, there is no question that CMMC will be a requirement for defence contractors within the next couple of years.
Contractors wanting to become CMMC compliant should begin the process immediately. It takes an average of 12 to 18 months to complete the preparation process and become ‘assessment ready’.
Additionally, the time from ‘assessment ready’ to assessment is on average, six months. An independent service provider, C3PAO, audits defence contractors to verify compliance with the CMMC requirements. However, a backlog exists because there are approximately 35 CMMC assessors authorised to assess approximately 50,000 defence contractors.
Another timeline consideration is that NIST SP 800-171 (the document that outlines CMMC’s security requirements) is expected to be updated and made more rigorous within the next year or two. Once NIST SP 800-171 is updated, the ‘readiness’ process for contractors will also become more rigorous.
Once a contractor is CMMC certified, the certification is expected to be valid for three years.
CMMC preparation and assessment costs
The budget for preparation and assessment should be taken into consideration, particularly for small and medium-sized businesses. Estimates range between $75,000 to $200,000 USD (£60,000 to £160,000 GBP).
- Estimates for the assessment: $25,000 to $50,000 USD (£20,000 to £40,000 GBP) – assuming a 40-hour, five-day on-site assessment, with pricing variance due primarily to location and expertise.
- Estimates for ‘readiness’ preparation: $50,000 to $150,000 USD (£40,000 to £120,000 GBP) – achieving CMMC compliance can be arduous, and few contractors are assessment ready before preparing.
More information about CMMC
- CMMC information on the US DoD website.
- National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 revision 2 – Protecting Controlled Unclassified Information in Nonfederal Systems and Organisations.
Did you know…Companies that work with the US Department of Defence must prepare for Cybersecurity Maturity Model Certification (CMMC). |
1 https://dodcio.defense.gov/CMMC/About/
For the second year in a row, IBM’s X-Force Threat Intelligence Index lists the manufacturing sector as the most attacked industry, and by a larger margin in 2022 than in previous years. Among the top attack vectors were spear phishing and the exploitation of public-facing applications. Generally, the most common technique used during incidents was extortion, with the manufacturing sector experiencing extortion in 32% of cases.
Why is the sector being targeted?
Nature of the sector
The sector has some shocking statistics that have emerged over the last few years, and this is a result of a number of reasons. One of the overarching explanations for this is down to the nature in which the sector operates. The manufacturing sector has a low tolerance to downtime leaving these businesses in an extremely vulnerable position. What makes matters worse, is that the manufacturing process involves several stages and various entities, meaning an incident in one area can impact the entire production line.
This leaves the sector prone to ransomware in particular, as there is a significant pressure to recover systems to maintain operation for business. SOPHOS’ State of Ransomware in Manufacturing and Production report found that 55% of manufacturing businesses were hit by ransomware in 2021, which is a 52% increase on the previous year.
What’s on offer for cyber criminals
Intellectual property (IP) makes the manufacturing sector a standout target compared to other sectors. It is one of the most valuable assets to manufacturers with years of research and costs that have been dedicated to developing a product or service, meaning a cyberattack can leave devastating effects if this is stolen. In 2020, Kroll found that 82% of incidents involving IP theft were a result of cyber related incidents, mainly involving phishing campaigns and malware.
Additionally, there is sensitive information that is held by manufacturing businesses that include customer records and payment information. All of which can be stolen to go on to facilitate identity fraud, or be sold on the dark web. Cybercriminals are now prioritising Personally Identifiable Information (PII) over credit card information, for example, as personal data can be sold for higher prices on the dark web.
Limited cyber resilience
While cost can prevent some companies from investing in cyber resilience measures, research has also found other obstacles that contribute. Recent research by Blackberry, in collaboration with The Manufactures Organisation, found that 54% of manufactures have not updated their cyber security, despite investing in digital transformation. However, almost half of manufacturers continue to use and maintain legacy IT, which in many cases are incompatible with the necessary cybersecurity updates. The research also found that 38% stated that there is a lack of cyber skills within their company and 33% said that there is an issue with providing third parties access for remote monitoring and maintenance.
What can be done to protect manufacturing businesses from cybercrime?
Below is a list of measures a manufacturing business can implement to reduce the effects of potential cybercrime, this list is by no means exhaustive:
- raise employee awareness and ensure regular training is in place
- ensure daily data backups are in place
- regular scanning for vulnerabilities
- third party risk assessments and ongoing monitoring
- ensure an incident response policy and plan is in place, that is tested at least annually.
How we can help
Our forensic services team work with businesses to review its current cyber resilience measures through services such as vulnerability scanning, third party reviews, and scenario-based testing of incident response plans. We have helped many businesses from various sectors to increase cyber awareness and resilience among employees and the wider business. If you would like more information on our services, please get in touch with Tim Robinson.
Did you know…Out of those in the manufacturing sector, only 7% of businesses that paid a ransom received all of the data back. |
In comparison to 2019, research found a staggering increase in data breaches among many sectors in 2020 – however, the food and beverage industry came out on top, experiencing a 1300% increase. The trend remained consistent for 2021, with Q1 continuing to show increasing figures.
Why is this the case?
During the pandemic, many food and beverage companies made the shift to direct to consumer e-commerce. In doing so, an abundance of consumer data is now collected by companies, posing a significant risk if companies are not safeguarding the data to the extent that they need to be.
The information gathered and held by the companies will usually consist of Personally Identifiable Information (PII) in addition to customer payment details, such as debit or credit card information and/or account login details. PII data is valuable to cybercriminals as it can be sold on the dark web, and in turn can be used for fraudulent purposes. The more data there is to access, the more damage that can be caused.
Further, the supply chain within the food and beverage industry is increasingly vulnerable to cyber-attacks. As there has been minimal levels of reporting of cybercrime within this sector, little attention has been drawn to the need for tightened cyber security.
Some entities within the supply chain will not hold vast amounts of data, but as a result of their systems being so easily exploitable cybercriminals will still take the chance to hack or infect systems and networks or use it as an entry point to other entities within the supply chain. In addition to the theft of data, attacks cause other major disruptions. This includes jeopardising the security of products, impeding the movement of products, halting production, and harming the quality and safety of products for consumption.
The sector has been referred to many a time as low hanging fruit for cybercriminals, particularly with the increase in automated operations. A recent example of a cyber attack in the food industry comes from KP Snacks, who were targeted by ransomware at the end of January. The company issued letters to stores stating that the attack severely impaired its IT communications systems, meaning the company were unable to safely process orders or dispatch goods.
What can organisations do to strengthen cyber security?
- Keep security software up to date.
- Conduct table top exercises with leadership and vendors.
- Ensure an incident response plan is in place and tested regularly.
- Understand the nature of the data that your company holds, where it is kept, and how it is adequately protected. It is important to bear in mind that regulations such as GDPR require organisations to conduct data mapping exercises.
How we can help
We offer a range of services to assess your company’s vulnerability to cybercrime from both and internal and external perspective, and can provide detailed reports on your organisations third party cyber resilience procedures. If you would like to know more about the services we offer, please get in touch with Martin Chapman.
Did you know…Research has found that around 57% of all cyberattacks targeting e-commerce sites are done by bots. |
Earlier in July 2022 the National Cyber Security Centre (NCSC) and the Information Commissioner’s Office (ICO) wrote a joint letter to the Law Society reminding solicitors of their advice regarding ransomware, and if a payment should be made in the event of an attack. Both the NCSC and ICO have seen a recent rise in ransomware payments being made which coincides with the monumental growth of ransomware attacks over the last few years, positioning it as the largest online threat to the UK.
Ransomware is a type of malware (malicious software) that unlawfully encrypts files on a network, holding the business to ‘ransom’ to decrypt them and restore business operations.
The intention of the letter was to reiterate to the legal profession, whose services are usually retained for advice in the event of an attack, that payment of a ransom will not fully protect the stolen data and/or result in a lower penalty by the ICO. This message can then be shared more widely with their clients.
Why do organisations tend to pay?
- An expectation of quicker access to business-critical files and systems.
- Paying the ransom could be cheaper than starting again from scratch.
- Fear of the PR and the operating implications if a ransom is not paid by a deadline and data is leaked.
- Poor preparation to recover in the event of a ransomware attack i.e. no useable backups.
The reality of paying
- All encrypted data is rarely recovered and restored.
- Recovering the data can take significantly longer than suggested.
- The cybercriminals could retain access to your network to deliver further attacks.
- There is no guarantee the cybercriminals will still not leak or sell your data.
- You make yourself a target for further attacks in the future as you’re known to pay.
- You’re funding the cybercriminals and the wider criminal fraternity.
NCSC and ICO guidance
Ultimately, each business will have its own reasons for the tough decision it must make in the event of a ransomware attack. However, the NCSC and ICO are clear in their guidance that paying a ransom does not reduce the impact of an attack or scale or type of enforcement action.
“The ICO will recognise when organisations have taken steps to fully understand what has happened and learn from it, and, where appropriate, they have raised their incident with the NCSC and they can evidence that they have taken advice from or can demonstrate compliance with appropriate NCSC guidance and support.”
Full guidance related to ransomware from the NCSC and ICO can be found here:
• A guide to ransomware - NCSC.GOV.UK
• Ransomware and data protection compliance | ICO
Unfortunately, ransomware will continue to be an effective tool for cybercriminals to extort money from businesses as more and more pay. Organisations need to make sure they are in a position to assess, manage and mitigate the risk to help reduce the potential of being victim of it.
How we can help
We offer various services that are able to assess your company’s vulnerability to cybercrime from both an internal and external perspective, offering guidance on how to strengthen your position. We also provide training to employees on topics regarding cybercrime and security. If you would like to know more about the services we offer, please get in touch with Tim Robinson.
Did you know…In the event of a ransomware payment being made, on average only 65% of the data is recovered, with only 8% of companies managing to recover all of their data. |
Most people would say they are aware of what makes a good password. It’s been a long-accepted standard that an online password should be a minimum of eight characters including numbers, capital letters and special characters. However, most people would agree that following these golden rules and using ‘Pa$$word!’, is easily guessable and far from secure. Cyber criminals have a myriad of techniques to decipher a password, so why make it easy for them?
The more unique, complex and long passwords are, the more secure they will be. However, the trouble is that most people have multiple online accounts and remembering unique passwords for each account is hard. People fall back to using the same passwords for different accounts, which is particularly dangerous when shared with an email account login. If a criminal is aware of your login credentials for one account, they gain access to all. Gaining access to an email account opens up rich personal information, potential access to other accounts or impersonation of you to trick others.
Three random words
The National Cyber Security Centre recommends combining three random words. The thought process behind this is to try to create a password that will be strong enough to keep criminals out, but easy enough for you to remember. Therefore, removing arbitrary complexity which makes them hard to remember and can have little benefit against criminal’s search algorithms. You’ll be less likely to use the same password for multiple accounts.
Although this sounds simple, it is very effective. Just think of three completely random words (e.g. DrainpipeHaircutMountain). Repeat it a few times in your head and you’ll be unlikely to forget it.
You should avoid using words linked to personal information which could be easily found out through social media profiles, such as favourite sports teams, birthdays, names of family or pets. Also, swapping out letters for similar looking numbers or characters only provides a small amount of extra security as criminals are well aware of typical substitutions. Keeping it simple will make it easier for you to remember.
Feel you can do more? Why not make it four random words. The more random words that are used to create passwords, the more password diversity. Previous password complexity requirements could be said to be going against creating more new passwords and making the criminals job easier.
Too many unique passwords to remember?
Get yourself a password manager. Password managers can help create and store all your passwords uniquely and safely, across multiple devices and platforms.
Perhaps it’s time to rethink your password strategy?
If you would like to know more about the cybercrime services we offer, please get in touch with Martin Chapman.
Did you know…The National Cyber Security Centre is a UK government organisation dedicated to delivering cyber security support and advice to the most critical organisations in the UK, the wider public sector, industry, SMEs as well as the general public. |
Rarely a day goes by without hearing about the huge sums of money associated with top flight football clubs and the entirety of the sport as an industry. Six clubs from the Premier League are included in the top ten European teams to have spent the most on recruitment in the last ten years. More recently the Premier League clubs’ gross spend totalled £295 million in the January 2022 transfer window alone. This was over four times higher than the spend during January 2021 (£70 million), and is the second highest winter transfer window spend ever. To put this into perspective, the gross transfer spends across the other ‘Big Five’ European leagues (La Liga, Serie A, Bundesliga and Ligue 1) stood at a combined £317 million, which is only £2 million more than the Premier League and England Football League combined. Given the substantial sums involved in football, this has unsurprisingly attracted cybercriminals.
Particular focus was drawn to the cyber security of football clubs in November 2021 after Manchester United’s systems were breached. The club reported that the breach had not impacted matchday operations, and club media channels including the website and app were unaffected. However, staff were unable to access emails. While Manchester United escaped relatively unscathed, other clubs were not so lucky.
In July 2020, a Premier League club almost lost £1 million after cybercriminals compromised the email address of a Premier League club’s managing director during a transfer negotiation, and only intervention from the bank prevented the club losing the money. Other cyber incidents have included an English Football League fixture being postponed due to a ransomware attack which locked the turnstiles into the stadium and disrupted security systems.
Examples of how a cybercrime incident could affect a football club
- Physical security of football stadiums – a ransomware attack could lock the gates of a football stadium and cause a fixture cancellation.
- Theft of players’ and fans’ personal information – personal information about players and fans could be stolen, and sold for criminal purposes on the Dark Web.
- Payment redirect fraud – hackers could use a man-in-the-middle attack to imitate a football club, or agent, to direct transfer funds to their account.
How we can help
Cybercrime in the football sector is a growing enterprise for many cybercriminals. We offer various services that are able to assess an organisation’s vulnerability to cybercrime from both an internal and external perspective. If you would like to know more about the services we offer, please get in touch with Martin Chapman.
Did you know…Most people will have heard of ‘phishing’ but have you heard of ‘whaling’? ‘Whaling’ is when cybercriminals specifically target high profile or high-level executives to try and steal sensitive data. |
SQL stands for Structured Query Language – cybercriminals use this language to force servers into delivering protected information. SQL Injection is a common form of cyberattack which a surprising number of organisations are vulnerable to. A study by the Ponemon Institute, The SQL Injection Threat & Recent Retail Breaches, found that 65% of the businesses surveyed stated that they were victims of a SQL Injection-based attack.
Consequences of SQL Injections
Simple to execute, SQL Injections can have catastrophic consequences for many organisations. Attacks can often result in protected databases concerning all kinds of information being leaked, for example personal information about customers or clients. This information can then be sold on the Dark Web and used for other criminal purposes.
The attack involves adverse actors submitting malicious code into an unprotected website comment or search box. The statement, or line of code, is manipulated which can enable the actor to steal, delete or modify data, as well as gain administrative control over systems that run the affected applications. Using input validation, such as prohibiting the use of special characters, is an effective way to prevent SQL injections.
How we can help
We offer various services that are able to assess your company’s vulnerability to cybercrime from both and internal and external perspectives. If you would like to know more about the services we offer, please get in touch with Martin Chapman.
Did you know…Target, Yahoo, Zappos, Equifax, Epic Games, TalkTalk, LinkedIn, and Sony Pictures have all been hacked by cybercriminals using SQL injections. |
Following the Prime Ministers announcement earlier this week, imposing economic sanctions on five Russian banks and three Russian individuals, the National Cyber Security Centre (NCSC) has repeated its advice that UK businesses need to be prepared for possible cyber attacks.
Why is this important?
Although no sector has been specifically identified as a likely target, Ukraine has seen several Distributed Denial of Service (DDoS) attacks officially attributed to Russia on Ukrainian banks. DDoS attacks are high volumes of malicious internet traffic directed at a specific target designed to prevent the service from working or being accessible.
Why are DDoS attacks so impactive?
Flooding an internet connected financial services organisation with malicious traffic can have serious impacts on those who are legitimately trying to access them. Delayed payments for goods and services can have contractual consequences such as late payment fees or delays in the dispatching of business-critical goods, particularly affecting “just in time” supply chains.
What is the risk to UK Financial Services?
The UK is interconnected globally with many UK banks communicating with banks in Ukraine and Russia. Economic sanctions affecting high net-worth individuals who have assets in UK banking institutions are now unable to transact. This could trigger retaliatory action by Russia in the form of cyber attacks.
Is it just DDoS attacks we should be prepared for?
No. Cyber attacks can take many forms and DDoS is merely one of them that has been seen recently. In early February, the US, UK and Australian cyber security agencies issued a joint alert that we can expect to see increases in the sophistication and impact of Ransomware targeting critical national infrastructures.
In January, a number of “fake” ransomware attacks targeted Ukrainian government agencies and non profit organisations. These ransomware attacks were similar to the 2017 NotPetya attacks, as they focussed on data encryption and destruction rather than profit for those behind the attacks.
According to Microsoft, the malware lacked a recovery mechanism so any victims who chose to pay the ransom would have been unable to decrypt their data and recover their services.
Organisations and individuals considering fundraising or sending aid to Ukraine should also consider whether this is likely to make them a more active target of cyber-attacks.
What actions should we take?
It is recognised that it can be problematic for any organisation needing to implement widespread, sweeping changes quickly, in response to changes to external threats. However, the NCSC has issued guidance concerning 11 areas that organisations should review and take appropriate action. These are:
- Check your system patching
- Verify access controls
- Ensure defences are working
- Logging and monitoring
- Review your backups
- Incident plan
- Check your internet footprint
- Phishing response
- Third party access
- NCSC services
- Brief your wider organisation
Click here to access the NCSC guidelines on actions to take when the cyber threat is heightened.
How we can help
We offer various services that are able to assess your company’s vulnerability to cybercrime from both and internal and external perspective, and can help you develop on your organisations current cyber resilience policies. If you would like to know more about the services we offer, please get in touch with Martin Chapman.
Did you know…A recent study found that 82% of UK organisations who have been victims of ransomware paid the attackers. This makes the UK the most likely to pay cyber criminals against a global average of 58%. From those who paid the ransom, 4% were unable to retrieve their data. |
Cyber-attacks on supply chains are expected to increase fourfold in 2021. Many companies rely on third-party suppliers to provide services and software that are essential for the functioning of everyday operations within the business. As a consequence of this dependency, suppliers can be trusted with an abundance of confidential and sensitive customer information, making supply chains an attractive target to cybercriminals. Supply chain attacks are also low risk high reward for cybercriminals, as a single attack can lead to a series of additional networks to compromise.
How do hackers exploit third party systems?
Many hackers use malware, with 62% of attacks being carried out using this method. Malware is a blanket term for viruses, trojans, worms and other harmful software that will disrupt systems and networks. Hackers will look for unsecure networks or unprotected servers and hide malware within the services or software deployed to the supplier’s customers. The malware can also be spread through infected weblinks, email attachments or corrupted media. Once the hacker has infiltrated a supplier’s system, they can have access to confidential and sensitive customer data, which can be stolen and used for criminal purposes. Additionally, malware has the ability to not only extract information, but also delete data that is critical to both the supplier and the customer.
What can your company do?
- Identify the volume and types of information that your company shares with its suppliers
- Understand how data is shared between your company and its suppliers
- Ensure supplier contracts include cyber-specific clauses to ensure that company data is well-protected
- Review your supplier’s cyber and information security policies and procedures
- Ask your suppliers how they meet their contractual obligations, for example relevant data protection legislation
- Ensure that your company has comprehensive incident response and business continuity plans in place to effectively manage a cyber-incident at one of your suppliers.
How we can help
We offer a variety of services that can help your company review the cyber resilience of your third-party suppliers. We can also help your company develop incident response and business continuity plans in the event of a cyber-incident at one of your suppliers. If you would like to know more about how we can help your company, please contact Martin Chapman.
Did you know…Over half of organisations have experienced a data breach caused by third-parties that led to the misuse of sensitive or confidential information. |
A July 2019 Crowe report calculated that fraud is likely to cost individuals and businesses US$5.1 trillion a year, with losses rising by 56% in the past decade. To gain an understanding of where your business’ vulnerabilities lie, you must think like a cyber criminal to identify where there is opportunity to take advantage, whether it be internal or external.
At Crowe, our approach to cyber protection is to step into the shoes of an attacker. We will assess a business’s current cyber security measures through the lens of a potential attacker. External vulnerability reviews are used to look at vulnerabilities in an organisation that are visible to cybercriminals. These reveal the extent and types of vulnerabilities that help a cybercriminal to decide on whether they should spend time attacking one particular business over another. Alongside an external analysis, we also investigate with an internal vulnerability check. Similar to the initial stages of penetration testing and authorised cyber-attacks, but without exploiting the weaknesses identified inside the business.
Additionally, access to dark web markets and forums allows us to look for evidence of discussions taking place about attacking particular organisations, and for any compromised emails and passwords. For expert tips on cyber security, read Six Steps To Better Cyber Hygiene. The article has been written as part of ‘The Art of Smart’ alongside other useful insights which look at the challenges around corporate decision-making in the current uncertain environment.
It is business essential that organisations ensure their defences against cybercrime and fraud are up to the mark. Cyberattacks are ranked first among global human-caused risks, according to the World Economic Forum Global Risks Report 2020, costing businesses up to US$11.4 million every minute in 2021.
COVID-19 has seen a significant increase in cybercrime, and it’s not a question of if an organisation will be attacked but when. For an organisation to maintain an effective response, the following three points must be understood:
- Technology needs to be used to protect an organisation as well as possible. However, we also need to be prepared to manage an attack if it happens. A comprehensive approach also involves being able to recover and mitigate any damage that has been caused.
- Those carrying out attacks are essentially cybercrime businesses, operating as such and making business decisions about which organisations are the best to attack in terms of resources needed and the potential benefits that could be claimed.
- Cybercrime is not like other phenomena that we seek to manage as risks. Cybercrime is not static, it is extremely dynamic, continuously developing and evolving – similar to a medical virus. This means that organisations’ responses and protective measures must evolve to reflect the latest manifestations of the problem.
If you would like further information on the services listed in this article or advice on any other cyber protection matter, please get in touch with Martin Chapman.
Did you know…Through ‘The Art of Smart’ we share expert opinion from inside and outside of the Crowe Global network to provide vital and actionable insight to leaders, wherever they do business. |
The pension sector reported approximately two data breaches a month relating to cybercrime, between June 2018 and April 2020. Security breaches were the most commonly reported cybercrime, accounting for 63% of reports, with phishing attacks being the second most common breach, accounting for 30% of reports. Despite this, our research has found that over a quarter of pension schemes do not have an adequate cybercrime breach plan in place.
The figures listed above are prior to the influence that COVID-19 has had on cybercrime. The latest Office for National Statistics Crime Statistics for England and Wales has shown a 92% increase in cybercrime incidents between year ending in March 2020 (876,000 incidents) and year ending in September 2020 (1,679,000 incidents) suggesting that the actual number of attacks on the pension sector is higher.
What are the threats to pension schemes?
Pension schemes are an attractive target to cyber criminals due to the extensive data that are held concerning beneficiaries, in addition to the potential funds that can be accessed. The Pensions Regulator defines the cyber risked posed to pension schemes as ‘the risk of loss, disruption or damage to a scheme or its members as a result of the failure of its information technology systems and processes.’ Cyber criminals have a plethora of techniques that can be used to deceive individuals into providing confidential data, or disrupting systems to retrieve information. Techniques can range from ransomware attacks, phishing campaigns, hacking, malware, domain spoofing to rogue employees.
Failing to prevent cybercrime or data breaches can result in a pension scheme suffering reputational damage, financial loss, public embarrassment as well as a fine from the ICO.
Responsibility of the Trustee
Trustees are accountable for ensuring a pension scheme is running efficiently for the benefit of its members’ interests, and as such must identify, assess and manage risks. Therefore, it is the Trustees responsibility to ensure that the schemes’ regulatory and legislative requirements are fulfilled. Trustees must also ensure that third parties, including the sponsor company/employer have the required cybercrime and data protection arrangements in place as many will also hold or have access to confidential information.
The Pensions Administration Standards Association (PASA) states that Trustees should always prepared for when a cyber attack will happen, as opposed to if. A cyber security policy should be in place, outlining the administrator’s approach to cyber security, and its ongoing plans to monitor and update procedures if and when necessary.
In addition, preventive measures must be implemented, that may include, but are not limited to:
- Regulating who has authority to access confidential information;
- Correctly configuring firewalls;
- Protecting networks with relevant security arrangements; and
- Using awareness campaigns to make sure employees are aware of the nature and scale of the threat.
How we can help
We offer many services to help pension schemes with cyber protection. Some of these services are listed online. Our Pension Funds Cyber Vulnerability Survey, and our report on The Nature a Extent of Pensions Fraud are also valuable resources. If you would like further information on how our Forensic Services can help your pension scheme, please get in touch with Martin Chapman.
Did you know…Only 40% of pension schemes have an Incident Response plan. We recommend having an incident response plan that has been tested to supplement other cyber security measures that are in place. Doing so will identify areas of weakness that need to be remedied. |
Research undertaken in 2019 found that 61% of UK Independent Schools have been targeted for cyber attacks in the last five years. This figure is likely to be higher now, due to the 92% increase in cybercrime incidents since April 2020 and the shift to online educational provision. The sudden adoption of online learning for students and remote working for teachers and staff may have introduced new vulnerabilities for cybercriminals to exploit. Failing to address the additional risks and implement effective measures would leave a school in a vulnerable position. The shift to online learning and remote access requires a proactive approach to monitor and prevent vulnerabilities being exploited.
Independent Schools are responsible for holding special category data and other sensitive information on students, their families, and teachers. Such information can include ethnicity, religious beliefs, health information, addresses, financial information, among others identifying factors. If this data is stolen, it can both be used against individuals and to facilitate additional crime such as extortion, identity theft and fraud.
The consequences of a cyber-attack can result in financial loss, file encryption or deletion, reputational damage, in addition to potentially damaging a student and their families.
What are the biggest cyber threats to Independent Schools?
Ransomware
Ransomware is a type of malware (malicious software) that infiltrates a network. It is usually disguised as an attachment or download. Once this is opened, access to files critical for the operation of the school’s systems can be encrypted and rendered unusable. The cybercriminal will often threaten the establishment if the ransom is not met. Such threats can include making the attack public (to damage the school’s reputation) or selling the stolen data on the Dark Web.
Phishing
Phishing consists of tailored, malicious emails sent to individuals that appear to come from a trusted sender. Attackers will often ‘spoof’ their emails, meaning the email will look extremely similar to how it would appear when sent from a reputable individual or company. The content of the emails will usually contain either a malicious attachment, or a malicious link to a website.
Phishing Emails can purport to come from a member of staff and be sent to parents requesting sensitive information, or to request that fee payments are made to a bank account not known to the school.
Man in the middle (MITM) attack
A man in the middle attack is where a cybercriminal has interjected themselves into the communication process. The attacker can either be a passive listener, by stealing information sent between others, or an active participant, altering messages or impersonating an individual in correspondence.
A MITM attack can be carried out in several ways, it can be by:
- Poisoning the Address Resolution Protocol (ARP) Cache
- Poisoning the Domain Name System (DNS) Cache
- Connecting to a public or unsecured Wi-Fi network
- Session hijacking (by stealing a session cookie)
- Hypertext Transfer Protocol Secure (HTTPS) spoofing
If you would like to find out more on how to address the most common cyber vulnerabilities, download our full report on Fraud and Cybercrime Vulnerabilities in Independent schools.
Did you know…Over half of ransomware victims do not recover their files after an attack. This is because the attacker either fails to deliver the promised decryption keys, or have poorly implemented the encryption/decryption algorithms. We are aware of one firm who paid the ransom five times, each time in the vain hope that their data would be decrypted. |
In 2019, 88% of organisations globally, experienced a phishing attempt. Phishing is continuously used by cybercriminals as it accounts for 90% of successful cyberattacks. Over recent years, phishing attacks have become much more sophisticated, with adaptations of the traditional form of email phishing being created.
So what is phishing, and why is it more successful than other forms of cybercrime?
Phishing is an attack vector, consisting of tailored, malicious emails sent to individuals that appear to be from a trusted sender. Attackers will often ‘spoof’ their emails, in order to make it look like it has been sent from a reputable individual or company. Spoofing emails consists of falsifying company information from an official company website to ensure the email looks believable. The content of the emails will usually contain either a malicious attachment, or a malicious link to a website.
Why should organisations be concerned?
Regardless of how aware an organisation may be in terms of cybersecurity, it will only be as strong as its weakest link. If a phishing email does get through the cybersecurity measures in place, the only defence left is the employee that has received the phishing email. CybSafe carried out an analysis on data from the UK’s Information Commissioners Office (ICO), revealing that human error was the cause of 90% of cyber data breaches in 2019, with phishing being the main cause. Phishing accounted for almost half of all reports to the ICO in 2019. The research also found that there had been a significant increase in end user mistakes from the two years prior, rising from 61%, to 87% to now 90%.
Variations of phishing attacks
Below are variations of the traditional phishing attack:
| Variation | Definition |
| Spear phishing | Spear phishing is a targeted campaign, when an attacker is looking for something specific or a specific individual. A targeted attack may use employee information in attempt to seem persuasive and realistic to the recipient. |
| Whaling | Whaling is a form of spear phishing that targets senior employees or celebrities. Attacking high profile individuals is much more worthwhile for a cybercriminal business as it provides a greater level of access to greater rewards. |
| Smishing | Smishing is the same concept as a phishing email, but uses text messaging services. A message will be sent to the victims’ mobile containing a malicious link or a phone number to call. |
| Vishing |
Vishing is carried out through voice call. Social engineering is an important component to vishing as the attacker will usually instil fear in the victim in attempt to gain sensitive information over the phone. The sound of a human voice has the tendency to gain victims’ trust more so than other variations. |
Tips to prevent falling victim to a phishing scam
- Inspect URL’s by hovering over the link before clicking on it.
- Inspect the senders’ email. Legitimate companies will have domain emails that include the company name, as opposed to using an email provider such as Gmail or Outlook, for example.
- Inspect language and grammar used in message content. It is likely there will be spelling or other errors.
- Call colleagues/suppliers to verify emails requesting sensitive information or urgent requests. Attackers will often put time pressure on the victim to instil panic and ensure a task is carried out promptly.
- Remain up to date on the latest phishing trends.
If you would like more information on how Crowe can help your organisation and its employees fight against phishing scams, please contact a member of the Forensic Services team.
Did you know…According to Google, cybercriminals have been sending over 18 million COVID-19 related emails to Gmail accounts every day since the pandemic began. |
Cybercrime is rapidly evolving, and businesses need to ensure they keep up with new and emerging threats. Businesses can improve their cybersecurity by performing regular penetration tests to help identify vulnerabilities in their systems. A penetration test, also known as a pen test, is a form of ethical hacking which is performed by an authorised cyber-attacker to evaluate the security of a system.
Why is penetration testing important?
Penetration testing is essential for identifying potential or actual vulnerabilities to malicious cyber-attacks launched across a computer network that could threaten the confidentiality, availability and integrity of the information being stored and processed. The results of the assessment help businesses to close the issues in a planned manner and improve the security of their systems. Penetration tests should be performed at least once a year to ensure any new threats that have emerged since the previous test are tackled promptly.
It is recommended that penetration testing is conducted across the entire network. However, if your business is particularly concerned about the security status of certain aspects of the network, such as the internal or external infrastructure, these can be tested independently. An internal penetration test helps identify what an insider attack could achieve, which can be perpetrated by anyone who has access to the inside of your network.
Perimeter systems
External penetration testing helps identify vulnerabilities in the internet-facing infrastructure of your business’s network, also known as the perimeter systems. These systems are directly reachable from the Internet, and are often the part of your network that is most regularly attacked by external hackers. In addition to internal and external tests, penetration testing can be performed on web applications to identify security vulnerabilities resulting from the design or coding of your business’s browser-based application.
How can Crowe help?
Crowe offer a range of penetration testing services to help businesses protect themselves against cybercrime.
According to the FBI, domain spoofing scams have cost over $26 billion (approx. £19 billion) in the last six years.
What is domain spoofing?
Domain spoofing is when a cybercriminal impersonates a company or one of its employees by creating a website link or email address similar to that of the legitimate company domain. The website or email will be altered slightly by changing only a few characters, so that the link or email will still read and appear to be the same as the original. Visuals and information from company websites are used to ensure the illegitimate domain is convincing. The content of a spoofed website or email, will use company branding and formatting, enticing its victims to follow instructions presented to them.
Email spoofing
Email spoofing deceives the email recipient by posing as a trusted source. Email spoofing is commonly used in phishing and spam campaigns as recipients is unlikely to open emails from unknown senders.
Website spoofing
Website spoofing is when a fake website is created, impersonating a legitimate website. Website spoofing can be an increasingly sophisticated attack as the spoofed website will capture sensitive information, such as login details or even banking credentials.
How can Crowe help?
Crowe offer a service that checks whether an organisation’s emails can be spoofed and whether spoofed emails can be received by the organisation. We also offer a service that monitors the web for spoofed websites, and can help to have spoofed websites removed. For more information or visit our cybercrime services page.
The threat of the Dark Web is real, and it is growing.
A recent study carried out by Dr. Mike McGuire at the University of Surrey revealed that there has been a 20% increase since 2016 in the number of dark net listings that have the potential to directly harm an enterprise, with four in 10 dark net vendors selling targeted hacking services aimed at Fortune 500 and FTSE 100 businesses.
What is it and how does it work?
The Dark Web is a component of the internet that cannot be reached through search engines, as it exists on an overlay of proxy servers. Proxy servers are a gateway between a user and the internet, and act as an intermediary directing online traffic to the requested address. These servers also allow the IP address of a user to remain unidentifiable and untraceable when accessing websites. An IP address is a digital address for your device, however it is subject to change depending on your location. To access the Dark Web, a specific piece of software called Tor is required, which conceals the users IP address and allows access to webpages which cannot be accessed through regular browsers, such as Google Chrome.
Why is the Dark Web a threat?
The Dark Web has become a marketplace for illegal goods and confidential information. Crowe’s Dark Web: Bad for Business report, in collaboration with the University of Portsmouth, found tools and services designed to defraud or perpetuate cybercrime against 21 of the top 50 UK brands (as identified in the 2017 brand directory league table). The research team found template bank statements, utility bills and passports; bank account numbers and sort codes; advice on phishing and fraud packs containing guidance on how to carry out various forms of fraud.
The true size of the Dark Web is unknown, but it is thought to form around 5% of the deep web. All content that cannot be found through a search engine is classified as the deep web, which forms part of the World Wide Web. The Dark Web has given way for a plethora of fraud, corruption and cybercrime to occur effecting both organisations and individuals.
Policing criminal activity on the Dark Web is a particularly difficult challenge as a result of Tor’s complex data encryption, anonymity and hidden services/applications. The Dark Web has become a method favoured by criminals to target organisations, so it is vital that businesses understand the Dark Web, and the threat it poses.
Crowe offers a low-cost subscription services for organisations interested in monitoring the Dark Web for emerging threats. It can be deployed quickly and provides a regular report of any discussions relevant to the organisation. For more information on how Crowe can help your organisation, please contact Martin Chapman.
Fraud
In an era dominated by digital transactions and virtual interactions, the fight against online fraud continues to intensify. Recognising the gravity of this challenge, the UK government and industry leaders have collaborated to introduce the new Online Fraud Charter – a comprehensive initiative to protect UK consumers from online scams, false adverts, and romance frauds.
The charter - a collaborative effort between governmental bodies, cybersecurity experts, and tech industry leaders - seeks to address the evolving tactics employed by cybercriminals in defrauding individuals and organisations. It encompasses a multifaceted approach to enhance cybersecurity measures, promote public awareness, and streamline legal frameworks to bring perpetrators to justice.
Key aspects
- Improving cybersecurity infrastructure is one key aspect of the charter. With the proliferation of online transactions which include sensitive data it has become imperative to invest in advanced technologies to fortify digital systems. The charter encourages businesses to adopt cutting-edge encryption methods, multi-factor authentication, and real-time monitoring to detect and prevent fraudulent activities.
- Public awareness is another critical element addressed by the charter. Education campaigns will be launched to inform users about the various forms of online fraud, common tactics employed by cybercriminals, and precautionary measures to safeguard personal information. By improving public knowledge and awareness, the charter aims to empower individuals to navigate the online landscape securely.
- Legal frameworks are also set to undergo enhancements, ensuring that the consequences for engaging in online fraud are severe and enforceable. The charter advocates for international cooperation to extradite and prosecute cybercriminals, aiming to enable a unified global response that is not hindered by geographical distance or differing laws. By establishing a robust legal deterrent, the charter aims to dissuade potential offenders and create a safer digital environment.
Which companies have signed this charter?
Some of the world's biggest tech companies - Amazon, eBay, Facebook, Google, Instagram, LinkedIn, Match Group, Microsoft, Snapchat, TikTok, X (formerly known as Twitter) and YouTube - have signed the charter to work with the UK government. By doing so, these firms are recognising the risk of fraud and financial exploitation their platforms present to the UK public, while also demonstrating a commitment to tackling it. Signing means they agree to adopt the measures set out in the charter within six months.
The Online Fraud Charter places collaboration at its core - as the UK government, private enterprises, and individual users are encouraged to actively participate in the ongoing dialogue and contribute to the evolving strategies to combat online fraud. However, while the charter represents a step forward, its success ultimately depends on the collective commitment of stakeholders. As technology continues to advance, it is imperative that efforts to safeguard individuals’ online advances at the same pace.
If you would like more information on our forensics services, please contact Tim Robinson.
Did you know…Data from industry body UK Finance shows that almost 80% of all authorised push payment fraud originates online. |
New Authorised Push Payment (APP) reimbursement rules introduced on 7 October 2024 by the Payments Systems Regulator are a positive step in reducing a victim’s losses, to a point. The new rules mean that victims of APP fraud of up to £85,000 must be reimbursed by their Payment Service Provider (PSP) within five business days, with limited grounds for refusal. Those who have lost more than £85,000 may be able to escalate their complaint to the Financial Ombudsman.
Overall, the changes have been welcomed as a positive step, although much focus must remain on preventing this activity from happening in the first place. The psychological damage to victims can be significant and the banks will be on the hook for reimbursing losses. Therefore, the money is still making its way into the hands of organised crime groups and having a damaging impact on society.
What do the rules cover?
All types of APP fraud are covered by the new rules. Most of these frauds involve social engineering tactics to trick victims into making payments. The techniques used by fraudsters can be highly sophisticated, often researching victims and deploying tried and tested tactics to elicit a payment. Examples include but are not limited to.
- Impersonation: fraudsters pretend to be someone the victim trusts, such as a bank representative or a family member in distress.
- Investment scams: victims are convinced to transfer money for fake investment opportunities.
- Romance scams: fraudsters build a relationship with the victim and then request money under false pretences.
The balance has shifted to support the victim
The new rules are a welcome move to mitigate concerns over the protection of victims. Individuals not only face significant financial losses by being tricked by these types of scams but can also be affected by shame and emotional damage stretching far beyond the financial burden. The shame also leads many to keep the issue secret, and it therefore goes unreported. The new process will now put victims first and not pass judgment on their actions.
Are fraudsters already exploiting the new rules?
Commentators have suggested the new rules could increase APP fraud due to potential victims being less concerned about the consequences and making rash decisions to make payments. To mitigate this risk, the new rules include several safeguards:
- cost sharing: the cost of reimbursement is split 50/50 between the sending and receiving PSPs, incentivising both parties to prevent fraud
- exceptions: reimbursement is not required if the customer has acted with gross negligence. The coming months will tell as to what PSPs classify as gross negligence, but they will also need to factor in the potential negative reputational impact if they make an incorrect decision which then goes viral on social media
- prompt reporting: victims must report the fraud promptly, and PSPs must act quickly to investigate and reimburse.
Nevertheless, as quickly as new processes are introduced fraudsters are scheming to exploit the scenario for their gain. Awareness must continue to be raised about the size of fraud losses in the UK, the tactics used by criminals and prevention must be at the core of our response.
Did you know…Crowe’s research suggests as much as £219 billion could be lost to fraud each year in the UK. Read the latest Annual Fraud Indicator to find out more. |
For more information contact Tim Robinson or your usual Crowe contact.
Processes and controls may already exist to limit potential opportunities and inherently we trust colleagues to always hold the best interest of the organisation at heart. However, new factors, such as the increase in remote working, the pace of technology outstripping controls and a lack of financial growth can contribute to opportunity, and temptation sadly creeping in for many ordinarily honest individuals.
As history has shown during previous economic downturns, the current cost of living crisis will put pressure on many to pursue fraudulent activities to better their position. Examples of internal fraud can include but are not limited to, invoice fraud and diversion of payments, false/inflated expense claims, theft of data/PI or payroll fraud.
There are several contributing factors at play, but broadly speaking these can be attributed to any of the following core reasons:
- financial pressure – when employees may be ‘making less’ in real-world terms, than what they previously did, or struggling to make ends meet, then they may be more motivated to engage in fraudulent activities to alleviate financial stress
- increased temptation – higher living expenses may tempt them to exploit weaknesses in internal processes and controls
- low employee morale – a reduction in employee morale and job satisfaction could lead to disgruntled employees who act on that frustration
- rationalisation – employees may convince themselves they deserve the extra income and rationalise the decision to act dishonestly
- lack of detection – in some cases, resources may be removed from detection and prevention of fraud for cost-saving reasons. Policies, processes, and controls may also become ineffective with new working practices
- high turnover of staff – temporary and short-term staff may be brought in without due diligence during recruitment and they may not be fully on board with the culture of the organisation.
How can you reduce the risk of internal fraud?
- Foster a strong anti-fraud culture – promote a culture of honesty, integrity, and ethical behaviour from the top down. Establish a whistleblower mechanism so employees can report suspected fraud without fear of repercussions and thus mobilise the honest majority.
- Internal controls – reassess and design new processes and controls where necessary, with a strong emphasis on segregation of duties to minimise opportunities to navigate old existing processes for fraud.
- Educate – provide ongoing training to colleagues so they are aware of the latest manifestations of fraud and what to look out for.
- Access control – limit access to sensitive information to only those who really need it.
- Recruitment – conduct thorough background checks on potential employees, especially those who will have access to financial or sensitive data.
- Investigate and respond quickly – investigate any suspicions, engaging with external professionals where necessary, as recovery of losses may be an option. This also sets a clear tone that disciplinary action will be taken.
Although not foolproof, a combination of the above measures will significantly reduce the risk of internal fraud. Prevention is always the best method to reduce costs and create a safer more ethical working environment.
If you do suspect fraud to have taken place, remember to follow our simple do’s and don'ts to begin with.
If you would like more information on our forensics services, please contact Tim Robinson.
Did you know…Crowe’s recent research with the University of Portsmouth’s Centre for Cybercrime and Economic Crime and Peters & Peters LLP has measured fraud to cost the UK £219 billion per year. Read the latest Annual Fraud Indicator to find out more. |
One of the biggest factors that makes fraud a complex crime is its adaptability. Aided by technological advancements and an ever-increasing globalised world, the opportunities for fraudsters to advance their methods and reach more victims continue to grow.
Increasing global awareness of the scale of the fraud problem has resulted in governments and law enforcement improving their responses to the problem. However, the opportunistic nature of fraud means staying up to date with the latest fraud trends is one of the best ways individuals and organisations can protect themselves.
Below are three fraud trends that have recently grown in size or sophistication. We discuss the typical methodology of these scams and how you can spot them to prevent falling victim.
- ‘Hi mum/Hi dad…’ message fraud.
The ‘Hi mum’ or ‘Hi dad’ message scam typically begins with a text message or social media message from an unknown number or account claiming to be a child. The messages usually begin with reassurance, something like ‘hi mum, this is my new number’. The messages then progress to a dire situation such as ‘I lost my phone’ or ‘I’ve broken my laptop’. Eventually, the fraudster convinces the parent to hand money over to bail the ‘child’ out of whatever predicament they claim to be facing.
It is an evolution of the ‘friend in need’ scam that’s been circulating for well over a decade now. The ‘Hi mum/Hi dad’ fraud is sophisticated in its nature, with fraudsters often using information from the victim’s social media to make it more convincing. It’s a scam that has caused significant harm recently; The latest statistics from the National Fraud Intelligence Bureau and Action Fraud showed there were 414 reports of this scam in the first five months of 2023, costing victims £467,208.
To protect yourself from this scam, individuals should never send any personal information or money to anyone without verifying the identify first. For example, calling your child to speak to them directly. Ensuring you do not make mistakes that compromise your privacy on social media can provide additional protection. - ‘Crash for cash’ moped fraud.
‘Crash for cash’ is a term used to describe a fraudulent insurance claim for a motor collision. Unlike traditional ‘crash for cash’ braking scams, moped fraudsters are driving directly into oncoming cars. Often hiding out of sight in a side road, they then drive into the victim and feign injury. The more sophisticated fraudsters will have an accomplice to act as a witness or to block the victim’s view.
This type of fraud is a growing problem around the country, with the Insurance Fraud Bureau stating the problem has reached “epidemic” levels in London. Reports indicate that within the last two years nearly every UK insurer has received bogus claims related to the fraud - collectively valued at £27million - with more than 2,200 victims in London alone.
To avoid such scams, drivers are encouraged to be cautious when pulling out of a side road, look ahead to spot suspicious drivers and keep a good distance. - Courier fraud.
Courier fraud, which has grown in prevalence in recent months, disproportionately targets older people in the UK. It is a sophisticated scam where perpetrators prey on the trust and vulnerability of their victims. There are various methodologies for courier fraud, but it usually begins with a phone call where the fraudster poses as an authoritative figure, often a police officer or bank official. Once trust is established, they then convince the individual into complying with their demands. These demands often include withdrawing large sums of money from the bank or revealing sensitive banking details such as their PIN of security question answers. A courier is then sent to their address to collect the money or bank card.
Statistics from the National Fraud Intelligence Bureau show that people in their 70s or older lost more than £12.6million to courier fraud last year. Individuals should remind vulnerable or elderly people in their family that the bank or police will never call them and ask for sensitive information or send a courier to their home to collect cash, valuables, or bank cards. Staying sceptical is vital in protecting yourself from courier fraud.
If you would like more information on our forensics services, please get in touch with Tim Robinson.
Did you know…Victims have reportedly lost £1.7million since the beginning of 2022 to the ‘Hi mum/Hi dad’ message fraud. |
Green energy scams – what are they and why are they rising?
There has been a vast increase in green energy scams across the UK in recent years, with Citizens Advice finding more than 19 million adults targeted in 2021. Research by the National Trading Standards (NTS) found that for one in four adults, losing just £100 to a scam would tip them into a serious financial crisis and leave them unable to pay bills or buy other essentials.
The demand for greener energy alternatives has risen. The NTS found that 64% of UK adults are either currently making their home more energy efficient or considering doing so. Efforts to make homes greener include installing effective loft insulation, setting up solar panels, or putting in energy saving devices at home such as smart meters. As people seek to reduce their carbon footprint by making their homes greener, fraudsters are trying to take advantage of these strives to help save our planet.
The increase in green energy scams is a result of both people wanting to do their bit to reduce their carbon footprint and the issues caused by the ongoing energy crisis, which has presented an opportunity for fraudsters. NTS report that energy scam phone calls saw a staggering 85% increase from August to September in 2022, with fraudsters offering grants for solar panels, loft insulation, spray foam, double or triple glazing and boiler replacements.
Examples of green energy scams
The UK government ‘Green Homes Grant’ scheme, which was launched in September 2020 and is now closed to new applicants, saw some homeowners and landlords in England get vouchers worth up to £10,000 to help carry out renovations to make their homes more energy-efficient. However, fraudsters across the UK immediately began targeting homeowners with scam calls, emails and texts following its announcement. Scams that were reported include companies pretending to be part of the new scheme and offering home owners insulation for their attics, and phone calls informing home owners that they were eligible for the Green Homes Grant and asking for personal information.
One case in Berkshire saw leaflets about the grant being dropped through people’s doors. This resulted in one homeowner enquiring further who was then told they needed to pay a large amount in cash to start the work. They agreed to go to the bank to withdraw the funds, but were luckily informed there that it was a scam. This isn’t the first time that government schemes have been targeted - the ‘Green Deal Scheme’ in 2013 saw multiple prosecutions for unfair consumer practices. Fraudsters will continue to exploit new trends and investments so it is crucial that people stay alert and aware.
Other recently reported green energy scams include calls pretending to be an energy supplier enquiring about switching to a smart meter. People were then asked to send a picture of their current meter and to send it to a fraudulent email address, where the scammers can take details of the meter and sell the information on or use it ‘as broker’ to change their energy supplier without the resident’s knowledge.
Five tips on how to stay protected from green energy scams
- Be suspicious. Fraudsters are quick to take advantage of opportunities and can be very smart in their methods. Take your time to think about every offer you receive, ensuring to ask questions and not rush into anything.
- Research. Before you buy or invest in anything, it is crucial to do your research on the company. Read reviews on different websites, ask for references and always read the small print
- Look for the signs. Typical signs that something is a scam is being contacted out of the blue with a deal that seems to good to be true, or being asked for personal and payment details immediately.
- Check certified schemes. If someone claims to be working on behalf of a government scheme, look to verify this. For example, to carry out work for the governments Green Homes Grant scheme companies must be registered as a certified installer with Trustmark.
- Get a written contract. Before any work begins ensure you have a written and signed contract, as this can help to protect your money should something go wrong.
How we can help
If you are worried about green energy frauds, our Forensic Services team of accredited counter fraud specialists can help. If you would like more information, get in touch with Tim Robinson.
Did you know…The Telegraph recently obtained data from Action Fraud that showed there had been a staggering 50% increase in bogus energy rebates/cases where fraudsters had referred to solar panels or other forms of renewable energy between 2022 and 2021. |
New data from Trading Standards has highlighted a significant rise in the volume of counterfeit goods being seized, with the number trebling since last year. The cause of this increase is credited to the ongoing cost of living crisis, which is pushing more people to try and save as much money as they can. Unfortunately, rogue traders and fraudsters are exploiting these efforts. Trading Standards research found that three quarters of UK adults are feeling more vulnerable due to the cost-of-living crisis and nearly half have seen a rise in scams.
What are counterfeit goods?
Counterfeit goods refer to any type of fake goods being sold as authentic and include but are not limited to designer clothes, accessories, electricals or cosmetics. The production, transportation and sale of counterfeit goods is a global, multi-billion-pound problem, with some estimating the counterfeit goods market is worth a staggering £499 billion per year. Counterfeit goods are sold around the world in various ways such as online, at markets, or door-to-door. Due to its scale and value, organised crime groups are heavily involved in the counterfeit business and it is considered one of the primary way criminal groups make and move money around.
What are the dangers of counterfeit goods?
The counterfeit goods market is deep-rooted, with over two thirds of UK consumers reporting they have received a counterfeit item when they thought what they were buying was genuine. Although the size of the problem makes it difficult to determine its true impact, there are number of clear dangers counterfeit goods pose to the public.
- Financial cost: The financial impact of receiving a counterfeit good is worsened in today’s cost of living crisis, as people try to make every pound count. Whether its because of poor product quality, products that don’t work or products that are dangerous, there is financial burden of receiving a counterfeit good.
- Health risk: Counterfeit goods also pose a significant threat to individuals health due to not being made to the specifications of the original manufacturer. Examples of the health impact include counterfeit batteries exploding, counterfeit cosmetics causing skin reactions and counterfeit helmets breaking.
- Damage to brands value: Research has found that when a consumer knowingly or unknowingly buys a counterfeit good, they think less of the brand associated with the counterfeit. This can have a significant negative impact on brands and consumers shopping habits.
How to stay protected and spot the signs
The increase of counterfeit goods diluting the global market mean it is more important than ever to be vigilant of counterfeit goods. To do this, buyers should:
- Check label and quality. Spelling mistakes and poorer quality materials on labels are often a sign the item is fake.
- Think about the cost. If the cost seems too good to be true, it often is. Compare the price you are being offered with other sellers or the recommended retail price.
- Research the website. If buying online, it can be difficult to tell if what you are buying is real or fake. Take extra precautions when buying from a website you haven’t bought from before by checking reviews and verifying the domain.
Did you know…Greater Manchester Police are currently undergoing ‘Operation Vulcan’, an attempt to rid Cheetham Hill and Strangeways in Manchester of counterfeit goods. This area has been deemed the UK capital for counterfeits, as it is believed to be linked to almost 50% of all counterfeit trading in the UK. |
Not everyone knows this, but we are in the midst of the fourth industrial revolution (4IR). This term was coined by Klaus Schwab from the World Economic Forum, to cover the significant advances that are occurring in areas such as below.
- Artificial intelligence and big data.
- Autonomous vehicles, robotics and drones.
- 3D printing.
- Blockchain.
- Synthetic biology.
Much of the discussion relating to these changes focuses upon the benefits to society, but we must also remember that each industrial revolution has led to new waves of crime. The 4IR, like all those before, will lead to new and innovative ways for criminals to exploit - many of whom are already doing so. Some of the prominent future frauds/cybercrimes are highlighted below.
Artificial intelligence and big data
Much is rightly made of the benefits of these tools for preventing fraud, but imagine what these same tools could be used for in the hands of criminals. First, the algorithms could be hacked creating flaws that could be exploited. Second, the technology could be turned to identify the weakest organisations/persons/systems most vulnerable to fraud. Third, bots are already being created to undertake many tasks relating to a scam. Consider a superbot of the future, that has been created to act like a real human: It could create its own digital presence and apply for financial products and services fraudulently without human intervention, other than to hand over the loot to their human ‘master’. Indeed, the Swiss police recently ‘arrested’ a robot that was buying illegal drugs online.1
Robotics, autonomous vehicles and drones
Drones are already well established as tools for criminals in the smuggling and surveillance of potential targets. However, the use of such systems for transportation of goods and the provision of security also creates opportunities for them to be hacked to divert goods and undermine the effectiveness of those security systems. This could lead to valuable parcels being diverted through hacks.
Deep fakes
Advances in the computing power/apps that are available will make deep fakes much more widespread. There has already been a case of a Director’s voice being cloned that enabled a $35 million fraud take place.2 Such technology is likely to become much more commonplace and utilised to impersonate persons to enable frauds to take place. Is it your boss you are talking to on Zoom or a deep fake? This might soon become a more common question.
3D printing
The advances in home printing has already enabled many high-quality identity documents to be produced to very high standards. However, more daring scams have already involved their use to build card skimmers that fit perfectly across ATM machines to enable card frauds to take place.3 3D printers are already producing human organs too, so how long before fingers, faces and retinas are produced to circumvent identification verification systems?
The future
The above are a simple snapshot and crime has always been an ‘arms race’. Many technologies of 4IR will benefit organisations in dealing with fraud, crime and other problems. But we also need to be on our guard, because these same new technologies will also unleash new and innovative forms of crime that we need to do our best to predict and be prepared for.
Professor Mark Button
Co-Director, Centre for Cybercrime and Economic Crime, University of Portsmouth.
Did you know…The artificial intelligence-based cybersecurity market share is expected to increase by USD $18.94 billion (£15.51 billion) from 2020 to 2025. |
1https://www.theguardian.com/world/2015/apr/22/swiss-police-release-robot-random-darknet-shopper-ecstasy-deep-web
2https://www.forbes.com/sites/thomasbrewster/2021/10/14/huge-bank-fraud-uses-deep-fake-voice-tech-to-steal-millions/
3https://venturebeat.com/offbeat/bad-guys-use-3d-printed-credit-card-skimmers-to-steal-100k/#:~:text=The%20latest%20in%20the%20latter,criminals%20steal%20an%20estimated%20%24100%2C000
The Association of Certified Fraud Examiners (ACFE) latest report on occupational fraud found that organisations are estimated to lose 5% of revenue to fraud each year. ACFE also report that a typical organisational fraud case causes a loss of around £7,100 per month and lasts 12 months before detection. Fraud is the most common crime in the UK, so it is crucial that every organisation in each sector recognises the risk. The impact of fraud on an organisation can range from minimal business disruption all the way to corporate collapse, as seen with the recent Wirecard scandal where corrupt practices and fraudulent financial reporting led to its insolvency.
How can organisations stop fraud?
Prevention is critical. Despite the high risk of fraud, many organisations still think that fraud won’t happen to them and fail to take the necessary steps to protect their revenue. Of the 2,100 cases ACFE looked into, nearly half occurred due to a lack of internal controls or an override of existing controls. Most organisations only have a process to react after a fraudulent act has taken place, but this approach fails to recognise the nature of fraud and puts them at increased risk. Below are three steps that organisations can take to lower the fraud risk and strengthen their preventative measures.
- Periodic assessment of fraud risk: In order to implement an efficient counter fraud strategy, an organisation needs to accurately measure the level of fraud it is exposed to. A fraud risk assessment aims to identify vulnerabilities within your organisation that make you more susceptible to fraud. This typically involves identifying risk areas through an assessment of current operations and processes before quantifying them to understand the level of risk. Once a risk has been identified and quantified, proportionate and relevant procedures can be implemented to mitigate the risk. It is crucial that these assessments are ongoing and not a one-off, as new fraud risks can appear. Ensuring you stay on top of the fraud risk through monitoring and reviewing is vital in protecting your organisation.
- Strong internal controls: A strong system of internal controls is widely considered the most crucial fraud prevention device. Strong controls reduce the opportunities to commit fraud by making it harder for dishonest people to steal assets, engage in corrupt business practices, or manipulate your organisation’s financial statements. There are variety of ways you can strengthen your internal controls, including delivering fraud training to all staff, segregating employee duties and surprise audits. Strong internal controls boost transparency and accountability and therefore reduces the likelihood of your organisation falling victim to fraud and increases the chances of detection.
- Strong detection methods: Ensuring your organisation has effective fraud detection methods is a critical part of a strong internal control system. ACFE found that fraud losses were twice as high at organisations without hotlines, so maintaining a hotline or reporting mechanism increases the chances of earlier fraud detection and reduces losses. Other detection methods include data analysis techniques and dedicated fraud departments. Accepting that your organisation is at risk to fraud is the first step in effective fraud prevention measures, as it enables you to treat it like any other cost that needs to be managed and reduced.
How we can help
We offer a wide range of services to help protect organisations, including specialised services for countering fraud that involves a Fraud Resilience Review and Fraud Loss Measurement exercises. We can also help your organisation through delivering Forensic and Counter Fraud Training and Mentoring and setting up a Whistleblowing service. If you would like more information please contact Martin Chapman.
Did you know…We have delivered projects that have resulted in reductions of up to 40% within a 12 month period, with around a 12-to-1 return on the cost of the work. |
Fraudsters are using social media and fake websites to sell bogus tickets. It has been reported that cases of ticket scams have increased by 603% this year already, with victims losing an average of £251. This surge was largely driven by fraudsters taking advantage of consumer demand to attend live events after COVID-19 restrictions were eased.
Criminals will target the biggest events which are already sold out, for example football cup finals. In May 2022, there was chaos at the Champions League Final football match between Liverpool and Real Madrid as thousands of fans were left stranded outside the stadium due to fake tickets. With the FIFA World Cup, one of the biggest sporting events in the world, coming up in November, this will undoubtedly attract fraudsters from across the globe.
How the fraud is conducted
Fraudsters utilise social media platforms, such as Twitter and Facebook, to market fake tickets to sought-after events across the entertainment industry. Fraudsters will often attempt to trick victims by uploading bogus pictures of the ticket(s), or posting a fictitious story about why they cannot attend the event.
The fraudster will then demand payment via bank transfer, which offers no consumer protection. Once the transfer has been made, the fraudster either deletes their own profile or deletes / blocks the victim.
Fraudsters are also spoofing legitimate domains to trick consumers into entering their bank account details. Domain spoofing is when a fraudster creates a fake domain purporting to be that of a legitimate domain, for example they may change a single letter which is difficult to notice. The website will take the payment for the tickets and / or steal the user’s bank details.
Signs to be aware of
- Ambiguous seller profile – be diligent around the appearance of the seller’s profile. Is there a lack of photos of themselves or others? Do they have few followers, or follow few people? Does their feed only consist, or largely consist of, spam-like messages?
- Selling tickets that have not yet been released – fraudsters will commonly claim to have exclusive early access to tickets, however if the tickets are not on sale through official channels, this means the fraudster doesn’t own those tickets yet.
- Websites with a slightly different domain – spoofed domains will look very similar to the legitimate domain, but may be spelt slightly differently, for example go0gle.co.uk rather than google.co.uk.
How can I protect myself?
- Using a debit or credit card will give you extra protection – consumers who pay by credit card are be protected by Section 75 of the Consumer Credit Act, and Chargeback rules. Under Section 75, you may be eligible for compensation from your credit card provider if the goods / services you purchased aren’t advertised. Similarly, under Chargeback rules, your card provider can get your money back from the bank the money was transferred to if you don’t receive the goods / services.
- Avoid purchasing tickets on social media – where possible only buy tickets from official channels, such as reputable ticket exchange sites.
- Use secure payment sites – never transfer money directly to a seller’s bank account, use a secure payment site such as PayPal.
Did you know…Between January and June 2022, cases of ticket fraud relating to football climbed by more than two-thirds. |
Our report ‘The Nature and Extent of Pensions Fraud’, in conjunction with the University of Portsmouth Centre for Counter Fraud Studies, estimates the cost of fraud to the UK pensions sector to be upwards of £6 billion per year. While there is a vast honest majority in this sector, there is also a small dishonest minority can cause serious damage. That dishonest minority can operate in many sectors, often placing themselves in positions with access to sensitive data. Pension scheme administrators are therefore an attractive prospect to fraudsters, particularly due to the volume and sensitivity of data that they handle.
How are pension scheme administrators being targeted?
From our experience, having conducted several investigations into fraud in the pensions sector, we have identified three common ways by which scheme administrators are being defrauded.
- Identity fraud: One of the most common approaches fraudsters employ is using fake identity documentation. Fraudulent government documentation such as passports and driver’s licences can easily be purchased on the Dark Web for a small fee. Coupled with fake utility bills, this is enough to steal the identity of a pension scheme beneficiary. Typically, the fraudsters will reach out to pension scheme administrators, for example, requesting a bank account change and / or address change to a property to which they have access to. Once the fraudsters pass the identity checks, they will then often request lump sum payments to their chosen account, where the money is then laundered from that account to various other - often overseas - accounts. The quality of identity documentation can vary, but they can also be very convincing, particularly if the employee scrutinising them at the other end has not been sufficiently trained, or are inexperienced, in dealing with fraudulent documentation.
- Internal fraud: It can be surprising to learn which roles within an organisation have access to large volumes of sensitive information. Criminal enterprises sometimes place individual(s) within an organisation in positions that have access to sensitive information in order to facilitate their crimes. For example, placing individuals in a position where they can alter bank details to direct payments to their own account, or individuals who have access to large databases with beneficiary data and used for other criminal purposes.
- Cybercrime: Finally, cybercrime is a growing issue that stretches across all industries. Criminals can target pension scheme administrators in several ways, whether that is a direct attempt to hack and steal data, by delivering ransomware attacks to stop operations or by compromising email accounts using phishing emails. Once the account is compromised, the fraudsters can monitor the email traffic and ‘place’ themselves in conversations to direct pension payments. If the criminals gain access to data, they can steal the information and sell it on the Dark Web for other criminal purposes.
How we can help
Our Forensic Services team are accredited counter fraud specialists, and are leaders in the pensions sector when it comes to fraud and cybercrime resilience. If you would like more information on how to implement counter fraud or cybercrime measures in your organisation, please contact Martin Chapman.
Did you know…We have produced a ‘Cyber Risk Made Simple’ guide, in partnership with PLSA and Aon, to help pension schemes to improve their cyber resilience. |
The 11th Annual Counter Fraud and Forensic Accounting conference, held by the University of Portsmouth took place on 14 June 2022, covering the latest research findings within the sector.
Below is a summary of some of the most recent research and the key takeaways following our attendance.
Interactions between fraudsters and victims online
Dr Elisabeth Carter, Criminologist and Forensic Linguist, and Paul Maskall, Fraud and Cybercrime Prevention Manager at DCPCU, discussed interactions between fraudsters and victims and the importance of recognising safety and risks online. The research highlighted how our relationship with technology is complex and provides an emotional feedback loop, a source of reassurance and inclusivity. The overarching issue with this, is that it can normalise other behaviours that leaves users exposed and vulnerable to grooming and isolation.
External factors and the risks post COVID-19
Claire Jenkins, Forensic Accountant at Companies House, discussed external fraud factors and risks in a post-COVID world. This research found that a reliance is put on accounts to make decisions and the assumption that they are correct is not always true. This reliance is by people without counter fraud training. Claire’s advice includes using a critical eye, comparison with prior year accounts, knowing your audit reports and to check accountants/auditors via registers available.
Data analytics to counter fraud
Barry Robinson, Head of Forensic Services at BDO Ireland, discussed the effectiveness of using data analytics to prevent and detect fraud. The research aims to explore the effectiveness of fraud prevention and detection techniques by using data analytics, machine learning and data mining. The findings suggest that while data analytics is widely used by businesses in Ireland, there is an under-utilisation of data analytics as an effective tool to fight against fraud.
Additionally, Emmanuel Pascal, Director Governance and Risk Management at Iriguard, spoke about how to efficiently use Data Analytics to counter fraud. Emmanuel presented the testing strategies used to successfully identify fraud schemes hidden in volumes of transactions using different processes. For example, this technique can be applied to sales, inventories, productions and payroll.
How we can help
We offer a range of specialised services for countering fraud that includes our Fraud Resilience Review and Fraud Loss Measurement exercises. If you would like further insight into the latest Financial Cost of Fraud figures, you can access our full report here. If you have any other questions, or would like to enquire about our services, please contact Martin Chapman.
Did you know…The first Counter Fraud and Forensic Accounting conference took place in 2010, where there were only 45 attendees. This year, 120 people attended in person and over 400 people joined online. |
The Lasting Power of Attorney (LPA), introduced in 2007, is a legal document that grants the named individual the power to manage the affairs of another in the event of them becoming incapacitated for any reason.
Matters that can be undertaken using an LPA include access to bank accounts, investments and savings, even the sale of property. Effectively, the person named in the LPA assumes control of the affairs of another. LPA’s are checked against a national database to confirm that the document is authentic before banks and other entities act upon them. There are approximately 3 million LPA’s registered currently and it costs less than £100 to file for one.
LPA’s are arguably the most powerful document in a person’s financial life.
Use of the LPA has increased over the last decade and sadly, fraudsters have taken advantage of this.
There are a few checks required to validate an LPA application and a recent investigation by a consumer watchdog found the counter fraud controls to be ineffective.
What are the consequences?
In the case investigated by the watchdog, a fraudster obtained an LPA by submitting falsified names and addresses and the victim’s signature forged. This was then used to attempt to sell the victim’s house from underneath them. The fraud was only uncovered when solicitors dealing with the conveyancing queried the LPA and requested a doctor’s certificate to certify the victim’s alleged incapacity.
In this case, it was good due diligence by the conveyancing solicitors that prevented a catastrophic fraud that would have caused the victim severe hardship and deprived their family of their inheritance. However, the actions of the solicitor are not standard procedure and this effectively creates a postcode lottery of whether LPA fraud is likely to be successful or not.
The annual report of the Office of the Public Guardian for 2020-21 warned of the risk that the “weakness in the current process allows the registration of a fraudulent [lasting power of attorney].” It said less than 0.1% of registrations are suspected to be fraudulent. There were more than 680,000 successful LPA applications in 2020-21.
However, the lack of effective fraud controls means that this 0.1% figure – representing 3000 potentially affected individuals of the 3 million registered LPA’s – is likely to be much higher.
How we can help
Our forensic services team are accredited counter fraud specialists, have access to the right tools to collate and analyse vast amounts of data and other material, and are able to present their findings to both the criminal and civil standards. If you would like more information on how to implement counter fraud measures in your organisation, please contact Martin Chapman.
Did you know…Fraudulent LPA’s can be submitted by strangers or indeed, people known to the victim. The National Fraud Intelligence Bureau recorded 3418 reports of Fraud by Abuse of Position with estimated losses of £67.5 million in 2021, demonstrating that those deemed to be trustworthy are still capable of fraud and the need for robust checks that are regularly reviewed. |
Scarcity of commodities increases opportunities for fraudsters to exploit long, complicated supply chains to maximise profits through fraud.
The global pandemic during 2020 was unprecedented and for many, unforeseen. Multiple sectors were forced into hurriedly placing their workforce into unplanned remote working conditions and some, particularly in the manufacturing sector were placed on furlough, with their production lines being stopped altogether.
As we emerge from these restrictions, the impact upon the global supply chains is beginning to become evident. Manufacturers are desperate to secure parts as the absence of just one piece is enough to prevent an entire product line from being shipped. For example, the IT and mobile phone manufacturers in particular have experienced high demand due to people seeking ways of staying in touch during lockdowns. But the scarcity of semi-conductors has created a perfect storm of demand exceeding supply. Lead times on new cars have increased and also numerous other products that contain semi-conductors that are now difficult to obtain.
The scarcity-effect inevitably pushes up the value of those products making them more appealing to criminal networks who either fraudulently obtain genuine components and sell on at massive mark ups, or they substitute genuine parts for counterfeit or substandard ones.
Supply chains are complicated with many touch points along the way. From the warehouses that store the parts, the courier companies that deliver them and to the production lines. Each of these touch points are susceptible to criminal efforts to interfere with.
What are the consequences?
Fraud committed against organisations engaged in supply chain activities can have severe consequences, particularly those who are contracted to provide parts “just in time” at specific points along the production line. If the parts are simply not where they’re supposed to be because they’ve been redirected by fraud, production lines can stop and service level financial penalties are incurred. In instances of supply chain contamination where genuine parts have been fraudulently substituted for reused, substandard or at worst counterfeits, negative reputational impacts are felt by the organisation that can take years to recover from.
Example case
In September 2021, Japanese electronics manufacturer Jenesis were unable to source microcontrollers from their usual supplier. Forced to seek alternative suppliers, Jenesis placed an order through an e-commerce site. When the microcontrollers arrived, they failed to turn on. An expert who examined the microcontrollers concluded that the specifications completely differed from what Jenesis had ordered, despite the packaging appearing to be genuine.
Detecting fraud at any of these touch points can be difficult to investigate and can be further complicated by vicarious liability risk. The best way to manage this risk is to proactively assure these supply chain touch points utilising specialist investigation techniques.
How we can help
Our forensic services team are accredited counter fraud specialists, have access to the right tools to collate and analyse vast amounts of data and other material, and are able to present their findings to both the criminal and civil standards. If you would like more information on how to implement counter fraud measures in your organisation, please contact Martin Chapman.
Did you know…Taiwan Semiconductor Manufacturing Co., the world's leading semiconductor maker, forecasts that the chip shortage will continue until around 2023. With that scenario looking increasingly likely, chip-hungry electronics makers have little choice but to remain vigilant. |
We examine some of the advantages and disadvantages of the various options that are open to an organisation when a potential fraud is uncovered.
For most clients there are two objectives that they want to achieve:
- To recover what has been lost; and
- To dismiss the culprit.
But what if the fraud is much larger than first perceived? And what if there are more people involved, both in the company and outside it? Would a criminal prosecution be best – both to hold to account those responsible and to send out a message of deterrence? Keeping all options available from the outset is vital.
Private investigator or a DIY investigation?
Let’s start with the option of, a private investigator or a DIY investigation? Reporting a fraud to the police can be seen as being ‘the right thing’ to do. A law enforcement investigation will allow special police powers to be deployed, such as the searching of premises owned or controlled by the suspect, and the use of production orders requiring banks to release account details, allowing the money trail to be followed. A criminal conviction is certainly a deterrent and a compensation order may be made at court, although this will only be for the amount that the defendant has been charged with and for offences that are ‘taken into consideration’ at the time of sentencing. This might not reflect the true extent of the loss. In a police investigation, the victim is handing control to the police and so is unable to make decisions about what happens. Even after a lengthy investigation, the Crown Prosecution Service may decide that there is insufficient evidence to justify a prosecution and no further action is taken. All of this also has to be taken into the context that the fraud has to be first reported to Action Fraud, with no guarantee that there will even be a police investigation, and that the criminal courts are open to press reporting.
A common misconception is that criminal action has to take precedence over civil action – there is nothing in law that prevents criminal, civil and disciplinary action from running in parallel, although good case management is required.
Law firms and counter fraud specialists
The final options include the involvement of a specialist law firm or a qualified counter fraud specialist. Both of these will leave control of what happens within the hands of the client – he or she will be the final decision maker. Very often both disciplines will work together, with the counter fraud specialist gathering evidence and interviewing witnesses and the lawyer advising on next steps to bring the matter to the best outcome for the client. Within the civil law arena, it is possible to obtain court orders that will produce the same effect as police powers – the ability to search, to obtain bank details and to require documents to be produced, even from third parties. Early involvement of a law firm will allow the protection of legal privilege to be applied to the investigation; the use of a qualified counter fraud specialist will allow the best evidence to be obtained from witnesses and from hard copy and digital sources in ways that will ensure admissibility in later proceedings. The evidence will be gathered to the criminal standard, so enabling the client, if desired and the evidence supports it, to launch a private prosecution in the criminal courts.
How we can help
Our Forensic Services team is made up of qualified counter fraud specialists, data analysts and forensic accountants. We work with specialist law firms that are expert in dealing with financial crime, with the aim of achieving the best, cost-effective outcomes for clients around the world. If you would like to know more on how to be prepared to tackle fraud in your organisation, get in touch with Martin Chapman to discuss what options are available.
Did you know…There were 4.6 million fraud offences in 20/21, a rise of 24% on the year before. For the same period, there were 5,576 criminal convictions. |
Recruitment fraud has the potential to infiltrate all industries and levels of employment, with 80% of CV’s containing discrepancies. Recruitment fraud is when someone lies about their experience, qualifications, employment history or previous integrity to gain employment. It denies genuine candidates’ job roles, denies employers’ staff that successfully carry out their responsibilities and allows fraudsters into an organisation where they can undertake wider fraud and theft. Subsequently, recruitment fraud represents a significant cost, which undermines the financial health of those organisations which are affected.
Recruitment fraud is a worldwide threat. There have been countless incidents of individuals claiming to have experience or qualifications that they do not have. From a serial fraudster using a fraudulent application to become a pilot; to a salesman that managed to run six schools into the ground after lying on his CV. Considering the importance and trust placed in some of these individuals, it is alarming how negligent due diligence can be on such job roles.
How is recruitment fraud damaging?
Establishing the true cost of recruitment fraud is a difficult phenomenon to quantify. However, we have carried out research that discovered the impact on the UK economy. In 2019, our ‘The real cost of recruitment fraud’ report found that recruitment fraud costs the UK economy approximately £23.9 billion. The same methodology was applied to the potential global cost of recruitment fraud, which costs approximately £559 billion.
The consequences of recruitment fraud can be significant. It does not only damage an organisations reputation and credibility, but it can have a catastrophic impact on customers, clients and/or patients. An example that illustrates the potential impact it can have comes from the NHS. A former NHS boss was given a two-year suspended jail sentence for lying about his university degree. Peter Knight, the former Chief Information and Digital Officer on a £130,000 salary, lied on his CV about having a Classics degree. Knight was only identified after an anonymous tip, and resigned from his role after two years. Failings in basic security checks of a senior official, who would have otherwise gone undetected, demonstrates how dangerously easy it is to falsify your way to the top. It was fortunate that Knight did not have a clinical role, nor had direct contact with patients. If the NHS is failing to check basic facts about a senior figure, it may be of concern as to what other areas the NHS are failing to check. For example, the academic background of a doctor, potentially resulting in incorrect treatment being provided, or worse, unintentionally facilitating a death of a patient. This case highlights that even the NHS, one of the largest national institutions in the world, fell victim to a simple case of recruitment fraud.
What can you do to avoid hiring a fraud?
- Qualification checks.
- Double check the legitimacy of certificates and documents provided.
- Ask for references and phone them.
- General background check (including personal addresses, previous convictions, social media profiles, past employers’ history).
Deterring individuals from carrying out recruitment fraud is not complex or difficult. Effective pre-employment checks are relatively low cost and easy to commission, however, you should always consult with an expert before you act.
How we can help
If you would be interested in strengthening your fraud resilience, or require background checks on individuals or companies, please contact Martin Chapman.
Did you know…The most common type of recruitment fraud that organisations experience is applicants claiming to have qualifications and/or status they do not possess. |
Local communities in which mines are situated benefit from the mining industry as they provide a steady source of income to those they employ and develop the local businesses which supply goods and services. As these communities are often in remote and poverty-stricken areas, some seek to exploit the opportunities the mine provides through corrupt behaviour, resulting in both the community and the mine itself suffering the consequences.
What are the most common types of corruption in mines?
Nepotism and cronyism
Nepotism and cronyism are terms used for when family members or those known to an individual receive preferential treatment, and are awarded jobs and other benefits as a result of favouritism. Nepotism and cronyism are completely unethical; however, both are often embedded within the cultures of local mining communities, and considered the norm.
In the mining industry, nepotism and cronyism is often evident within the recruitment process. Unfair advantages are provided to individuals who may not be able to carry out a job role efficiently. This hinders the growth of the mining business in several ways:
- It deters genuine candidates from applying for job roles as the recruitment process is not based on prior knowledge or experience;
- It demotivates other employees as there is no merit-based system in place;
- It is unsustainable for the development of the mine; and
- It denies the mine people with the best skills.
Procurement fraud
The UK National Fraud Authority defines procurement fraud as “A deliberate deception intended to influence any stage of the procure-to-pay lifecycle in order to make a financial gain or cause a loss.” Procurement fraud can be carried out by those external or internal to the organisation.
From our experience, it can be an internal employee from a mine who creates bid rigging schemes and/or creates ‘ghost’ suppliers. Procurement fraud can arise as a result of many factors, including little or no enforcement of the organisation’s procurement policies, falsification of documents, and collusion by an internal employee with an external supplier. The consequences of this behaviour are:
- Unnecessary financial loss;
- Undelivered goods or services; and
- Failure to achieve the organisations operational objectives.
Bribery
Bribery is the offering, giving or receiving of any item or service that is of value to an individual in exchange for an unfair advantage or favour. In the mining sector, it is often an external source that bribes an internal employee to gain employment, contracts or financial gain. The damaging impacts on a mine include:
- The forming of a culture of corruption, with the mine gaining a reputation for bribery;
- Increased business costs, without any added value; and
- A weakening of the trust between honest employees and contractors, and the local community.
How we can help
If you would like to find out more on how fraud impacts the mining sector, click here to download our report on countering fraud for competitive advantage in the mining and energy sector. Or, if you would like information on how we can help you reduce the chances of fraud and corruption within your organisation.
Did you know…Crowe UK’s Forensic Services Team have undertaken work for natural resources companies in Central and South East Asia, East and West Africa, Australia, Canada and the United States. |
The National Audit Office (NAO) has estimated that the UK Government will spend more than £210 billion on its response to the COVID-19 pandemic. This money has rightly been spent on supporting organisations and individuals across the country in this time of unprecedented economic stress and the vast majority of the money has been legitimately applied for and correctly received.
However, there is always a dishonest minority and on Wednesday 7 October 2020 the NAO published its report, ‘Investigation into the Bounce Back Loan Scheme’, which has taken a closer look at how the Bounce Back Loan Scheme (BBLS) has been distributed.
How it works
The report notes that the HM Treasury, British Business Bank (the Bank) and Department of Business, Energy and Industrial Strategy (BEIS) developed BBLS provides registered and unregistered businesses with loans of up to £50,000 or a maximum of 25% of their annual turnover. This loan should help to maintain their financial health during the pandemic. The scheme launched on Monday 4 May 2020 and will remain open until Monday 30 November 2020, with the government retaining the right to extend the Scheme.
The loans are provided by commercial lenders (for example, banks, building societies and peer to peer lenders) directly to businesses, who are expected to repay the debt in full. Failure to do so may have a negative impact on their credit score and may affect their ability to borrow in the future. The government provides lenders a 100% guarantee against the loans (both capital and interest). This means if the borrower does not repay the loan, it will step in and repay the lender. HM Treasury data shows that as of Sunday 6 September 2020, the Scheme delivered more than 1.2 million loans to businesses, totalling £36.9 billion. BEIS and the Bank expect BBLS to have lent between £38 billion to £48 billion by Wednesday 4 November 2020, substantially more than it initially expected.
The opportunity for fraud
The government recognises that the decision to provide funds quickly leaves taxpayers exposed to a significant risk of fraud, including fraud caused by self-certification; multiple applications; lack of legitimate business; impersonation; and organised crime.
BEIS’s 2019-20 annual report and accounts highlights likely total credit and fraud losses of between 35% and 60%, based on historic losses observed in prior programmes which most closely resemble the Scheme. Assuming the Scheme lends £43 billion, this would imply a potential cost to the government and taxpayers of £15 billion to £26 billion – an enormous sum.
The nature of the losses are likely to be on a spectrum from high volume, low value opportunistic fraud through multiple fraudulent BBLS applications from fake companies through to high value, low volume fraud by organised crime groups. The number of companies registered each week after the government announced the scheme rose by 285% to a record 21,616 by the end of June 2020.
What can be done?
So, what is to be done? For many years, police resources focussed on fraud have diminished and it is now very hard to persuade them to take on a case of fraud. BEIS and the Bank do not have the counter fraud resources to investigate this scale of fraud. Perhaps it is time for private sector forensic and legal specialists to help tackle this threat – and to ensure that there are clear and visible consequences for the dishonest minority. The government did the right thing in supporting UK business – could specialists from UK business now support the government in identifying and investigating the fraudsters and recovering the losses?
Fraud can take on many shapes and forms with far reaching impact. It costs the NHS £1.29 billion a year (with independent academic estimates actually putting this figure between £3-£5 billion) and is a good example of how it can touch everyone’s life in the UK in one way or another. That’s enough to pay for over 40,000 staff nurses or purchase 5,000 ambulances. Due to the scale and complexity of the NHS it is affected by lots of types of fraud, one of which is the phenomenon of ‘ghost patients’. Ghost patients are people registered with General Practices who do not actually use the practice because they have moved to a different neighbourhood or have died.
NHS Digital records showed that in 2018 there were 3.6 million more patients registered with the NHS in England than there were people in England, and a 2018 investigation revealed the imbalance was the result of ‘ghost patients’. NHS General Practitioners (GPs) receive £150 a year for each patient registered with their practice, and with an average of 1,700 registered patients each the payment is a significant proportion of a GP’s income. The investigation revealed £550 million was wrongly allocated to GP’s who, either intentionally or mistakenly, kept ghost patients on their books.
Ghost patients, and the additional payments associated with them, could be the result of poor record keeping rather than intentional dishonesty. Irrespective of the cause the result is similar, less funding available for the NHS to spend on the good work to keep the public healthy and save lives.
Any organisation thinking about where it may be losing money to fraud should always consult an expert before taking action. For more information on tackling fraud and to discuss measures to strengthen your organisation’s security.
A fraud investigation often reveals a lot more than was originally suspected. Where fraud does take place, it is rarely an isolated incident and so an investigation into its full extent is very important. Investigations - using various techniques - can provide the opportunity to determine who is involved and the fraudsters’ modus operandi, and to identify the process and systems weaknesses which may have allowed the fraud to take place.
A thorough investigation is the only way to resolve a suspicion of fraud. Following the findings of an investigation, a strategy to devise a proactive approach to reduce the nature and extent of fraud can be adopted, resulting in a long term beneficial impact on businesses’ approaches, company cultures and employees’ and suppliers’ outlooks.
How is an investigation carried out?
An investigation can be carried out using a number of different techniques and these are tailored to each specific investigation. Open source information resources are a common tool to gain insight and background knowledge concerning individuals, businesses, associated persons and assets. Additional methods can include examining (with permission) emails and other data, interviewing employees, and analysing relevant documents. When the relevant data has been identified, it can then be prepared for the most appropriate form of analysis in order to draw conclusions.
Recent COVID-19 lockdown conditions have limited some face to face aspects of fraud investigations. Nevertheless, Crowe has the capacity to undertake remote investigations using its proprietary technology to remotely image computers and interview witnesses and suspects. This is highly effective.
Where do you start?
The first stages of a fraud investigation can be the most important to get right and we recommend to always seek specialist advice if you suspect a fraud to have taken place. We have compiled a list of ‘dos and don’ts’ if you find yourself in this position.
A thorough investigation is very important. It doesn’t have to be a lengthy process but the thoroughness is crucial. Not to resolve a suspicion of fraud can be very damaging both to the organisation concerned and to those who are suspected. There is no substitute to a professional, legally compliant investigation in order to do this.
Bribery and corruption
Due diligence is the first step in preventing fraud or corruption when entering commercial engagements, such as dealing with third-party suppliers or during a merger and acquisition transaction. A blog from the Foreign Corrupt Practices Act (FCPA) stated that around 90% of all enforcement actions involved third party intermediaries, yet over 50% of procurement professionals stated that they do not believe that their existing suppliers had been vetted properly.
What is due diligence?
Due diligence is part of compliance procedures, used when a business is looking to work with any external company. Due diligence goes beyond a “tick box” method – it consists of data collection and analysis. In any commercial relationship, a detailed due diligence process will avoid unnecessary risks and will provide the grounds to make informed decisions.
This can be done through the following:
- Assessing an organisations financial position.
- Background checks on the individual’s involved.
- Identifying cyber risks and vulnerabilities.
Why is due diligence important?
Regardless of whether you are a large organisation or an individual, it is your company’s responsibility to ensure your company as well as its suppliers follow regulatory requirements, such as the UK Bribery Act. Due diligence is especially important if your company carries out business globally, as some countries will have anti-corruption laws in place but do not have the means to enforce them. Therefore, having a knowledge on what your suppliers (and where possible your suppliers’ suppliers) activity is vital.
Failure to carry out adequate due diligence can impact your business by resulting in:
- Contracts that are prone to collapse.
- Reduced asset value and returns.
- Negative media attention.
- Financial penalties.
- Trade restrictions.
- Loss of trust from shareholders.
Below are a handful of examples of when we have recently supported clients on a range of matters related to due diligence and corporate intelligence:
- Work for a UK organisation searching relevant information sources across the UK, Europe, Singapore and China to reveal the background and senior officers of two companies bidding for a contract. We uncovered the real owners of the companies and identified corporate misbehaviour which would have caused reputational damage to the client if they had have proceeded with the deal.
- Work for a FTSE250 company who feared that a senior officer in their finance department was collaborating with competitors to sabotage deals. We looked in to their background, associates, lifestyle and other links which confirmed the client’s suspicions and action was taken.
- Work for a UK SME which identified the links between their former finance director and organised criminals. This explained a pattern of behaviour involving money laundering and fraud and lead to successful litigation.
- Work for several pension schemes checking the bona fides of people claiming to be pension beneficiaries (this is a common type of fraud) in different countries including the US, Germany and Holland.
Investing in adequate due diligence prior to third party engagements will prevent more significant losses from occurring in the future. Crowe offer Corporate Intelligence services that carry out financial, integrity and cyber due diligence to overcome the possibility of carrying out business with untrustworthy entities.
If you would like more information on how we can help your organisation, please contact a member of the Forensic Services team.
Did you know…Fraud and error losses in any organisation should currently be expected to be at least 3%, probably almost 6.5% and possibly more than 10%. Find out more in our latest Financial Cost of Fraud report. |
In 2019, the National Crime Agency (NCA) stated that money laundering cost the UK over £100 billion a year. The UK has been used to launder money and hide assets of corrupt elites for many years, and has received criticism regarding its leniency toward Russian oligarchs and kleptocrats. The UK has been a hot spot for money laundering as a result of its thriving financial and professional sectors, in addition to the limited restrictions when establishing a business. Once a seemingly legitimate company is established, criminals will then use the company to launder illicit funds.
Money laundering risks the UK’s national security, its reputation, and jeopardises international confidence in the UK. With this in mind, the Government set out to tackle the issue in its July 2019 Economic Crime Plan. The plan spans from 2019-2022 and encompasses the work carried out in both the public and private sector. In immediate response to Russia’s invasion on Ukraine, the Economic Crime (Transparency and Enforcement) Act 2022 was fast tracked. One element of this act came into force this week.
Earlier this week (1 August 2022), The Register of Overseas Entities was introduced. The register seeks to identify corrupt oligarchs and elites that are trying to conceal ‘ill-gotten gains’ through UK property. The register requires anonymous foreign companies owning or seeking to buy UK land to reveal their true beneficial owners so that criminals cannot hide behind a chain of shell companies. Foreign companies will need to provide verified information of its beneficial owner to Companies House before any application is made to the UK’s land registry. Failure to register is a criminal offence and prevents entities from being able to buy and/or sell UK property in the future. A transfer of land by overseas entities in breach of the registration requirement is also a criminal offence committed by the entity and each responsible officer of it.
The register applies to property purchased since January 1999 in England and Wales, and since December 2014 for Scotland. There is a six-month transitional period to register.
How we can help
If you suspect there may be corruption in your organisation or would like more information on how to protect your business from risk of corruption, please get in touch with Martin Chapman. It is important that organisations fully understand the background of companies and individuals they are considering doing business with and we can undertake detailed checks globally.
Did you know…The UK has the second-highest amount of money laundered each year. The United States ranks number one with the highest amount (£216.5 billion). |
A few weeks ago, we looked at Deferred Prosecution Agreements (DPAs); what they are, why they were introduced, and when they are offered to companies. An aspect we touched upon was Section 7 of the Bribery Act 2010, which allows organisations to provide a statutory defence being it has adequate procedures in place to prevent anyone associated with the business, whether it be sub-contractors or employees, from committing bribery. This article outlines what procedures that companies should have in place to ensure good practice, encourage an anti-corruption culture, and avoid harsher prosecution.
What is Section 7 of the Bribery Act?
Section 7 of the Bribery Act is titled ‘Failure to Prevent Bribery’ and was established to encourage companies to take liability for corrupt behaviour. Under Section 7, any person associated with the company that bribes another person with intent of obtaining business or business advantage for the company will be found guilty of an offence under section 7. Unless the company can rely on the defence that it has adequate procedures to prevent bribery from occurring, it will be found guilty under Section 7.
What is meant by ‘adequate procedures’?
The UK Government has produced guidelines as to what constitutes ‘adequate procedures’, the guidelines have six principles to follow. We have summarised these below:
- Proportionate measures
Proportionate measures relate to the size, nature, and complexity of the business as these factors will play into how at risk a company is to bribery. Measures include clear and practical documented policies and procedures that the company have implemented and maintained to achieve an anti-bribery culture. To ensure the company has effective policies and procedures in place, it must first identify each area risk can present itself. It is advised that bribery prevention procedures remain separate from any other wider guidance the company has. Policies and procedures should state the commitment the company has taken to prevent bribery, its general approach to mitigate specific risks, and how the company implements its policies. - Top-level commitment
Top-level commitment refers to the management of a company being dedicated to preventing bribery, this can be the owner of the company, or the board of directors, for example. An executive that has adopted a zero tolerance towards bribery promotes an anti-bribery culture within the company. Management should seek to regularly communicate its anti-bribery stance to its employees, and take an active role in the development of bribery prevention procedures. - Risk assessment
A company should assess its internal and external risk to bribery. The purpose of risk assessment is to promote risk procedures that are proportionate to the nature and scale of the company, and location that business is carried out in. Risk assessment procedures should seek to accurately identify and prioritise potential risks within the company’s activities, markets and customers. - Due diligence
Due diligence checks should be carried out on persons who perform or will perform services for or on behalf of the company to identify any bribery risk before engaging in business activity with said persons. Due diligence relating to bribery can also form part of the company’s wider due diligence processes. Due diligence should be proportionate to the identified risk, and can either be done internally or by external consultants. - Communication
To ensure bribery prevention policies and procedures are embedded within the company and are understood fully, internal and external communication is essential. This can be done through regular announcements and updates of latest risks and prevention measures, training, and promotion of code of conducts. Doing so will create an awareness for employees and can act as a way of monitoring and evaluation for management. - Monitoring and review
Anti-bribery procedures that are in place must be monitored and reviewed on a regular basis, with improvements made where necessary. Monitoring is essential as risks of bribery may change over time. The effectiveness of bribery prevention procedures should be reviewed by management on a periodic basis, as well as by its employees through staff surveys and/or questionnaires to gauge how measures can be improved.
How we can help
Our Forensic Services team is experienced in advising companies on how to adopt an anti-bribery culture. The team also undertake due diligence reviews on individuals and organisations. If you would like to know more on how your company can implement the measures listed in this article, please get in touch with Martin Chapman.
Did you know…That only two companies have been prosecuted and convicted under Section 7 of the Bribery Act. The first conviction took place in 2015 against Sweett Group plc, and the first contested prosecution took place in 2018 against Skansen Interiors Ltd. |
What are Deferred Prosecution Agreements and are they effective?
Deferred Prosecution Agreements (DPA’s) are a relatively new procedure that are becoming increasingly popular across jurisdictions. They were introduced in the UK in 2014, under the Crime and Courts Act 2013. Their purpose is to encourage large corporate entities to take liability for economic crime, including cases of fraud, bribery and/or money laundering. Since DPA’s were introduced in the UK, a total of 12 have been agreed by the Serious Fraud Office (SFO) with large corporations. In the last month, the SFO has invited three companies to enter DPA’s. As of 1 July 2021, the SFO invited its 10th company, Amec Foster Wheeler Energy, a company that provides engineering and technical services to enter a DPA to settle a case involving historic corruption allegations through the use of middlemen. As of 19 July 2021, the 11th and 12th companies, that have not been named for legal reasons, have been invited to enter a DPA following bribery offences relating to multi-million-pound UK contracts.
However, inviting a company to enter into a DPA has been subject to mixed reviews, as part of the agreement is to avoid harsh prosecution inflicted on corporate entities. Regardless, the Chief Executive at the SFO recently defended the deferred prosecution regime, stating that it is indeed necessary to tackle white collar crime and ensure the executives of companies do not distance themselves from the actions of their companies.
How do DPA’s work and why were they introduced?
DPA’s are used to encourage companies to take liability for economic crime that their employees have committed. It is an agreement that has been reached between the prosecutor and the party that could be prosecuted, under the supervision of a judge. An organisation will only be invited to enter into a DPA if they agree to fully cooperate with the SFO’s investigations and fulfil any other additional terms set out. These may consist of paying compensation, paying a financial penalty, continuing to cooperate in any future prosecutions of individuals and implementation of a compliance program. Once an organisation has been invited to enter a DPA, the proceedings for the criminal offence that was charged are automatically suspended.
The attributes of a DPA are set out to:
- Avoid lengthy, costly and complicated trials.
- Encourage companies to self-report.
- Avoid hinderance in business and reputation of companies.
- Provide the opportunity to minimise damage to third parties (employees, shareholders and victims).
- Ensure the process is public and transparent.
Even if a DPA has been entered into, individuals involved in the illegal activity can still be prosecuted.
Why is there uncertainty around DPA’s?
There is some controversy that revolves around DPA’s as they enable companies to avoid convictions by paying a financial penalty. On top of a financial penalty, additional fees can also include a compensation order, disgorgement of profits, reparations or donation to charities that support victims of the criminal activity, and a payment to the prosecutors’ costs. It is therefore argued that as a result, DPA’s may be seen as just an additional cost to carry out business, making it an ineffective deterrent.
A discretionary tool
A DPA is a discretionary tool that is open to the prosecutor to apply – it is not guaranteed to be offered in every case. The circumstances of the case will dictate whether the prosecutor considers that a DPA will be appropriate and, importantly, in the public interest. Factors such as self-reporting, cooperation with the investigation and that fact that positive action had been taken by the company to prevent wrongdoing, will all aid the prosecutor to consider a DPA. The last factor will mirror the actions a company should be taking to support the statutory defence under s.7 of the Bribery Act 2010 and will include things such as training, organisational culture and effective management.
How we can help
If you would like further information on best practice measures to ensure your company is doing all it can to prevent economic crime, please contact Martin Chapman.
Did you know…To date, a total of approximately £1,130,739,000 has been, or will be paid in financial penalties by companies that have entered into DPA’s, with the sums being paid to the UK Treasury. *In some cases, organisations will have had to pay additional costs to jurisdictions outside of the UK. *A breakdown of the financial penalties for the two most recent DPA’s have not yet been disclosed. Between the two companies a total of £2,510,065 will be paid for the disgorgement of profits and financial penalties. |
Corruption is a form of dishonest behaviour carried out by an individual in a position of authority that abuses their power for illicit gain. Bribery is one of the most common types of corruption. Bribery is the act of providing someone with money, services or even valuable items in return of a favour. Acts of bribery are typically disguised as donations, inflated prices, expenses, commissions or ‘facilitation’ fees. Bribery is difficult to spot and can often go unobserved by organisations and law enforcement.
Bribery has a negative impact on the businesses involved and other stakeholders. It can result in individuals involved becoming vulnerable to blackmail and extortion, and also leave an organisation vulnerable to local and international anti-bribery legislation. Bribery often compromises an organisation’s ‘social licence’ to operate, and could even result in an organisation being debarred from operating in sectors and jurisdictions.
Bribery Act 2010
The UK Bribery Act (2010) has extra-territorial reach, meaning that foreign companies that have a presence in the UK, and UK companies that have a presence overseas can be prosecuted if there is failure to comply with the Act. The Act includes four main offences:
- To bribe another person
- To be bribed
- To bribe a foreign public official
- Failure by an organisation to prevent bribery.
The Act introduced corporate liability for bribery. The legislation requires that companies implement adequate controls to prevent persons from participating in acts of bribery. If an employee of a company is found to have given or accepted a bribe, having adequate measures in place can be used as a defence by the business affected.
What can businesses do?
Recent research found that almost a quarter of UK businesses experienced acts of bribery between 2016 and 2018. In Crowe’s experience, there are several ways an organisation can adopt a proactive approach to tackling bribery and corruption, and emphasis should be placed on risk perception and foreseeability of where and when bribery may arise. Ways to reduce the risk of corruption include, but are not limited to the following:
- Due diligence on third parties, individuals and organisations
- Having a whistle blower hotline
- Staff training
- Regularly updated anti-bribery and anti-corruption policies.
If you would like more information on how to protect your business from risk of corruption and bribery, please get in contact with a member of our Forensics team.
Case studies
The pension scheme that approached Crowe UK’s forensic Services team in 2021 has over 200,000 members and wanted the team to assist with its cyber resilience. Pension schemes in the UK generally follow the same structure, with the scheme being legally independent from its sponsoring employer, yet still relying on its IT infrastructure. For example, Crowe UK Pension Scheme may share the same name and IT infrastructure as Crowe UK, however it is a separate legal entity and must prove to The Pensions Regulator that it has appropriately addressed cyber risks – Crowe UK Pension Scheme cannot rely solely on its sponsoring employer for everything cyber-related.
Crowe UK was engaged to assess the cyber maturity of the scheme, produce policies that were effective in practice, and develop a method to manage the technical vulnerabilities of its eco-system. To comply with The Pensions Regulator, UK pension schemes must “take steps to reduce the risk of incidents occurring, and appropriately manage any incidents that arise”. As part of this, schemes must have effective cyber resilience and incident response policies in place and ensure that they have taken appropriate action to address cyber risks.
To establish the cyber maturity of the scheme, the Forensic Services team had to perform a cyber resilience assessment of the Scheme, its sponsoring employer, and its third-party suppliers. This assessment is performed annually to ensure that the scheme’s eco-system is continuing to maintain its resilience to cybercrime, and to identify any areas that may need improvement. An additional exercise, a cyber resilience review of data flows, was performed to identify exactly what data is shared by the scheme with third party suppliers, and whether it was protected in transit. In the event of a cyber-incident, this exercise is valuable, and the Scheme will be able to quickly identify what data has been potentially compromised, and who needs to be contacted. It is also beneficial for understanding where the risk lies with each supplier and how improvements can be made to security around that risk. Using a risk matrix, this exercise helps identify which suppliers are high, medium, or low risks using a traffic light system.
The next phase of the project involved creating cyber resilience and incident response policies. These policies helped the scheme to clearly identify what to do in an incident, roles, and responsibilities, and how to communicate internally and externally. The team then delivered an incident response training session to evaluate this plan in practice, which proved to be highly beneficial to the scheme, highlighting positive aspects of what they were doing, and also any learnings to take forward.
On the back of the success of the governance aspect of the project, the work snowballed to produce further deliverables concerning the technical aspects of third-party suppliers, which we refer to as the Quarterly Supplier Cybercrime Vulnerability Dashboard. The Dashboard, developed internally, is designed to examine vulnerability management by third party suppliers from a technical perspective. The dashboard is run quarterly and examines the external infrastructure of each supplier, whether they have compromised emails on the dark web, and if they have reported any cyber-related breaches to the Information Commissioners Office. We can then track what percentage of vulnerabilities have been mitigated by the suppliers since the previous quarters, attribute an overall vulnerability management status, and provide an update on their vulnerability management progress.
This two-pronged approach, examining not just the technical aspect of cyber security but also the governance aspect, means the scheme was provided with a comprehensive review of their eco-system and means they can now provide sufficient assurance to their members, and the regulator, that they’re doing all they can to protect their member’s data and pension. Aspects of the project are recurring and have continued ever since, solidifying the relationship between the team and our client.
For further information on our cyber services and how we can help you, please contact Tim Robinson.
Why is it important?
Most litigation and arbitration cases are international in nature, whether involving a cross-border transaction gone wrong or a breach of contract between two international parties. Typically, these disputes, though cross-border, only require specialist services without specific local expertise related to the international element. However, there are occasions where having a specialist firm with the reach of an international network is invaluable.
In this insight, we explore relevant case studies where access to an international network has been particularly beneficial to our clients. We also examine future trends that will continue to underscore the importance of having access to an international network for resolving future disputes.
Example one: Local knowledge
In an expert advisor case, we were tasked with supporting a security for costs application. The law firm involved had instructed an international intelligence team to locate specific international financial statements. By liaising with our network and local individuals with accounting knowledge, we were able to visit the companies' house registrar and obtain copies of the financial statements.
The value of obtaining these financial statements was significant in securing the application and was only possible due to the local relationships we had in place.
Example two: International specialisation
In one High Court case, support was required to assess the economy of an African country, specifically to determine whether businesses there were highly reliant on cash or sophisticated enough to use modern payment methods. Access to an international network allowed us to support a local specialist—an auditor experienced in auditing a variety of firms—in providing their opinion.
This breadth of international specialisation enabled us to assist in UK proceedings while ensuring the opinions were relevant and robust.
Example three: Cross-functional collaboration
While not always international in nature, the reach of an international accounting firm allows us to leverage the specific expertise of colleagues, including auditors and tax advisors for professional negligence claims, sustainability teams for Environmental, Social, and Governance (ESG) and climate-related disputes, and insolvency and restructuring teams.
For instance, we work closely with our audit partners on professional negligence claims. In one case, it was alleged that the audit standards had fallen below expectations, failing to identify and report significant fraud to the Directors.
We collaborate closely with our specialists to support them throughout the dispute process, enabling us to assist our clients with a wide range of disputes.
Advantages of accessing an international network
Access to an international network and specialist services is crucial in several key areas for resolving future disputes.
- International mergers and acquisition (M&A): The volatility of interest rates and inflation motivates cross-border deals. Favourable foreign exchange (FX) rates and built-up demand are likely to drive significant activity, some of which may not go as planned.
- ESG and climate disputes: The rise in ESG and climate-related disputes will require specialist input from climate experts familiar with various global regulations and frameworks.
- New Arbitration Bill: Introduced in late 2023, the updated Arbitration Bill aims to solidify England's reputation as a world-leading centre for resolving disputes, ensuring London continues to arbitrate many international cases.
How Crowe can help
While not required for all types of disputes, access to an international accountancy network that works collaboratively can be both a necessity and a way to add real value. The examples above illustrate how international network firms can collaborate to provide the support needed to assist our clients. Moreover, key market changes are likely to be international in nature, necessitating some level of international collaboration.
For more information contact Alex Houston or your usual Crowe contact.
Our National Forensic Team (NFT) has been working 1,000 miles north of Vancouver, at 3,000 feet above sea level in Canada at a gold and copper mine. It is quite a hostile environment that requires a four hour flight in a small plane and there is then only one road up to the glacial plateau where the mine is based. The work involved a Fraud Resilience Review (fraud resilience is a measure of how well an organisation is protected against fraud and corruption) and related training at this mine.
This follows work that the team has undertaken at mines in Zambia, Cote d’Ivoire, Cameroon, and Mali as well as different sites in Indonesia and Kazakstan. The Fraud Resilience review involves assessing the level of protection against fraud and corruption against the 29 factors which impact most on the extent and cost of these problems, then rating the organisation concerned in accordance with a scale of 0 to 50 – 50 being as good as it gets.
The NFT has a long standing partnership with the Centre for Counter Fraud Studies at University of Portsmouth and jointly manages two databases – one concerning 25 years worth of data concerning the measured total cost of fraud (not just what is detected) and a second which contains the fraud resilience data of more than 1,000 organisations. The higher the fraud resilience rating (i.e. the better protected an organisation is), the lower the cost and extent of fraud and corruption.
The temperature was in low single digits, and the weather grey and rainy with occasional bright spells. To make up for it, the food – as is usual at a mine – was plentiful and it would have been very easy to put on weight, as the mine’s General Manager warned us. The mine was in Tahltan territory and it was good to see how our client had partnered with the first nation to help them develop sustainable companies and to invest in the community
How we can help
We offer a range of specialised services for countering fraud that includes our Fraud Resilience Review and Fraud Loss Measurement exercises. If you have any questions, or would like to enquire about our services, please contact Martin Chapman.
Did you know…Previous similar work by Crowe has included the cost of procurement fraud being cut by more than 50% at a large copper mine in East Africa. |
Background
A global non profit approached us after experiencing a case of invoice fraud as a result of a hack. In total, over £163,000 was transferred to a fraudster’s bank account after a hacker intercepted email communications between the company and its supplier. Our forensic specialists responded quickly by attending the site that same day, determining that the company had been compromised by a phishing email.
We initiated steps to address the hack and commenced an investigation, which involved the following:
- an investigation into the circumstances surrounding the invoice fraud affecting the company and a company member
- a cybercrime vulnerability review to report any weaknesses in cyber resilience and to make relevant recommendations
- penetration testing of the company’s Wi-Fi and guest network
- cyber security training for the employees.
The investigation found the email account of a former office manager had been compromised by a phishing email for over a year. Phishing is the fraudulent practice of sending emails purporting to be from reputable companies in order to induce individuals to reveal personal information. Phishing scams include URL links to malicious sites or attachments that contain malware, and when clicked on by the recipient, can infect their device. The hacker compromised the former manager’s account and manipulated communication between the company and their supplier, resulting in a payment being sent from the supplier to a bank account held by the fraudster.
How we helped the non profit
We undertook a review of the information held on the account to establish what other data the hacker potentially had access to, which included over 80,000 emails and identified 291 effected individuals. The types of personal data ranged from bank accounts and sort codes, to national insurance numbers and passports.
To help prevent a similar scenario happening again, we conducted a cybercrime vulnerability review, in addition to providing cyber security training for the employees. In addition to the review, we also performed an internal and external penetration test of the company’s network. A penetration test is an authorised simulated cyberattack on a computer system intended to evaluate the security of the system. Several vulnerabilities were identified, such outdated software, which were reported back to the company to be patched.
Given the nature and extent of the personal information that the compromised email account contained, the hack was deemed as a data protection issue and was reported to the Information Commissioners Office (ICO). Due to the quality of our findings, the ICO responded saying no further action was required as they were satisfied with the swiftness and quality of the response to the hack. This not only saved the company significant costs from a potential fine, but also prevented the pain of a full-scale investigation from the ICO.
Further information
You should always consult with an expert before you take action. If you would like further information on how we can help you strengthen your organisation against fraud and cybercrime please contact our Forensics team.
Did you know…Phishing can also be perpetrated through SMS messages, also known as ‘smishing’. Fraudsters can make the fraudulent message appear in the same thread as a legitimate chain of messages from your bank, for example. |
Forensic Accounting in Football: The Big Match
Acting on behalf of a sleeping giant of football, we were involved in a litigation case against an established European giant of football.
The case revolved around the footballing giant breaching confidentiality agreements to trigger a release clause to enable the transfer of a key player that belonged to our footballing client. As a result of the player being unavailable to our client for the remainder of their contract, the losses incurred as a consequence, needed to be quantified. The end figure forecasted, known as the quantum, was hotly contested. Before becoming involved, a strike out application had been made as to whether it was actually possible to quantify any loss. A strike out application is used when the applicant wishes to demonstrate that a case does not have reasonable grounds for bringing it in in the first place.
The case went to the Court of Appeal where concern was expressed as to how difficult it was to quantify the claim, but that this should not stop the case proceeding. The concept of a machine that had eleven working parts which were all working well was introduced - if one of those parts was removed, this would likely result in some sort of impact on the performance of that machine which could, theoretically, be measured – it was at this point we were approached when a robust approach was required to support the Club’s position.
The key question was whether the removal of that player had any impact on team performance and, if so, what was the best way of assessing quantum in that respect. We limited our period of review to 12 months. The issues of foreseeability and remoteness were addressed. Foreseeability and remoteness are the reasonable anticipation of the possible results of an action, and the causation of the loss as a result of a breach of contract or duty. These two factors, and the link with the player’s market value at various dates (as provided by another expert) was pivotal to our approach.
Every area that our client may have incurred losses was categorised. The legal term for categorising the damages incurred is referred to as ‘heads of loss’. The heads of loss we quantified included:
- Loss of match day attendance (analysis of season ticket sales; match day sales);
- Loss of add on sales both match day and non-match day;
- Impact on performance of the Club and potential ‘but for’ financial returns;
- Consequential impact on revenue streams, notably tv money;
- Salary/bonus impacts;
- Mitigation issues, such as other player purchases.
Where relevant, the principles of the “loss of a chance” were used. For example, on the balance of probability, in how many games would the player have been fit to play, or selected, if they had not left. One key aspect of our report was to forensically analyse the season in which the player represented the Club, ahead of their enforced move. It was clear from the players’ appearances, and the team’s results, that there was a correlation between this players contribution and the success of the team, notwithstanding of course the many other factors that contribute towards a team’s performance.
Ultimately, further to intense discussion in experts’ meetings (following forensic accounting reports disclosed by ourselves and the other side), the case was settled on the steps of the Court and a pleasingly satisfactory financial outcome for our Client.
Procurement fraud in a mine
A major mining company in Africa approached Crowe in May 2018 about a suspected invoice fraud of in excess of US$300,000. Crowe’s investigation identified a corrupt network involving suppliers, procurement and human resources and the recovery of over $1,000,000 from the supplier involved.
The mine is located in a remote part of Africa so, rather than send a person to site, Crowe used specialised technology to obtain forensic images of several computers and other electronic data. A forensic image is a direct copy of all the files on a storage device, such as a hard drive. A forensic image will typically include all files saved on a machine, included deleted documents. The technology used by Crowe significantly reduces the upfront costs of starting an investigation and enables remote and covert data collection.
Through the analysis of almost a million files and ten interviews with past and current employees, the investigation revealed the fraud was perpetrated by one employee from the mine and several employees from a supplier. The mine was defrauded through the submission and processing of false invoices. Payments for other goods and services were also concealed, for example the costs of hiring a vehicle were concealed within catering recharges to the mine. The procurement processes were easy to exploit, with a reliance on proof of shipping information rather than proof that the goods were received. In some cases the mine was charged for goods that were never delivered or even ordered in the first place. The individuals involved also committed fraud to obtain goods for their own personal use, including vehicles and expensive food and alcohol.
The investigation also revealed multiple vulnerabilities in the organisation’s procurement processes, and a lack of any verification on the quantity and quality of goods and services provided by suppliers. In addition to rooting out the corrupt network, the investigation findings were used by the mine to renegotiate several supplier contracts and save significant sums of money.
Before engaging Crowe the mine had conducted its own internal investigation that quickly hit a dead-end. By applying its expertise Crowe quickly and thoroughly established the truth of what happened and help the mine to put things right.
You should always consult with an expert before you take action. Get in touch with the Forensics team if you require further information or to discuss our services.
Insights and news

Webinars
Fraud and cybercrime
An introduction to cyber security
Diagnosing the organisation’s vulnerabilities
Strengthening resilience
Incident response
Fraud and international trade
Cybercrime: effective protection for SMEs
COVID-19 and fraud
COVID-19 and cybercrime
Cybercrime: fix the most common vulnerabilities
Fraud and cybercrime
An introduction to cyber security
Diagnosing the organisation’s vulnerabilities
Strengthening resilience
Incident response
Fraud and international trade
Cybercrime: effective protection for SMEs
COVID-19 and fraud
COVID-19 and cybercrime
Cybercrime: fix the most common vulnerabilities
Meet the team
Pragmatic advice, tailored service
We care about your business. Close working relationships are at the heart of our service delivery which sees our clients stay with us year after year, trusting us for our specialist advice and open dialogue.
We understand the forensic landscape. Our expertise, market knowledge and access to professionals across our global network means we are well placed to offer insight and pragmatic advice to your businesses at each stage of its lifecycle.
We help you to make smart decisions that have lasting value. Working with you, we will help you to successfully adapt and overcome challenges you may face, both today and in the future.
Contact us

















