Albania
Andorra
Armenia
Austria
Azerbaijan
Belgium
Bulgaria
Croatia
Cyprus
Czech Republic
Denmark
Estonia
Finland
France
Georgia
Germany
Greece
Hungary
Ireland
Italy
Kazakhstan
Kosovo
Latvia
Lithuania
Luxembourg
Malta
Moldova
Netherlands
Norway
Poland
Portugal
Romania
Serbia
Slovakia
Slovenia
Spain
Sweden
Switzerland
Tajikistan
Turkey
Ukraine
United Kingdom
Uzbekistan

Cyber Security
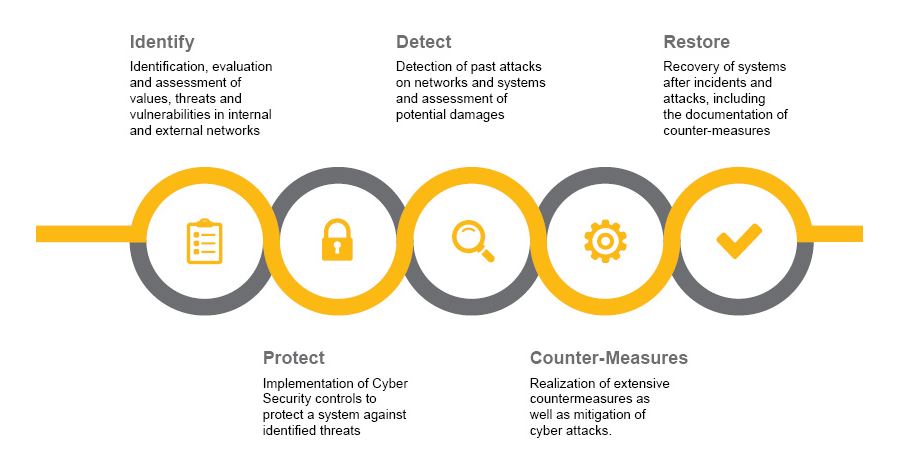
Reliance on technology is ever increasing and as a result, the constant threat of attacks is making companies more vulnerable. The effects of such attacks can severely damage a company’s’ business and even pose a threat to its very existence.
To overcome these threats, it is essential to know potential attack vectors in order to be able to protect IT systems accordingly. Defining counter measures to be taken during an ongoing attack is as important as adapting the com-pany’s’ entire IT security strategy to these new threats.
- We perform qualified cyber security checks and derive count-er-measures for any identified weaknesses
- We analyze your information and data protection processes to identify possible areas of improvement.
- We support you in implementing information security management systems (ISMS) that are based on well-established standards such as ISO 2700x, ISIS12, German BSI and NIST.
- We accompany you in the compliance of measures aimed at preserving your digital identity.
Our Experts
