National news coverage on data breaches tend to happen in case of what is referred in Cyber security as a Catastrophic or Mega Breach i.e. more than 100,000 compromised records. Unfortunately, data breaches do not only happen in big corporations but in all type of organizations, with often disastrous consequences.
In their yearly data breach report, Ponemon Institute/IBM surveyed over 500 organizations having experienced a data breach between February 2019 and April 2020, in 17 countries, including 26 organizations in Canada.
While the Canadian sample is somewhat limited, the report and associated data points give interesting perspectives on data breaches, their costs, contributing factors, and mitigating elements.
The study uses activity base costing to estimate the total cost of a data breach by accounting for all internal time spent in dealing with the data breach, external expenditures, and lost business opportunities.
Canadian data breaches by the numbers
In 2020, data breaches in Canada cost on average $6.3 million, an increase of 6.5% from the year before.
Their cost versus income disproportionally impacted smaller organizations with an average cost of $3.87 million for organizations with less than 500 employees versus over $7 million for organizations with more than 5,000 employees.
Malicious attacks were the root cause in 42% of the cases, system glitches in 35%, and human error in 23%.
Customer Personally Identifiable Information (PII) were breached in 80% of cases.
Lost business represented 39% of the total cost; detection, escalation, notification 35%, and ex-post response 26%.
The not-so-bad news: The human factor
The human factor remains one of the main cause of data breaches with 44% of cases being impacted.
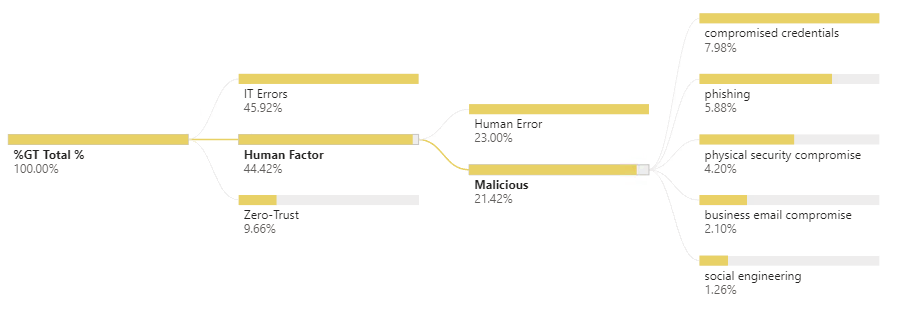
Half of them relate to the exploitation of employees’ behaviour by malicious actors: e.g. phishing, business email compromise, sign-in password compromise, and physical compromise (tail-gating). The other half categorized as pure human error e.g. leaving a laptop unattended or copying data to an unsecured location.
Organizations that have implemented employee training programs had, in average, reduced the cost of a data breach by more than $300,000. -making employee training potentially the easiest and most valuable quick win.
The concerning news: IT errors
IT related errors represent 46% of all root causes, being the exploitation of a miss-configured cloud environment (8%) to the more general category of system glitches (35%).
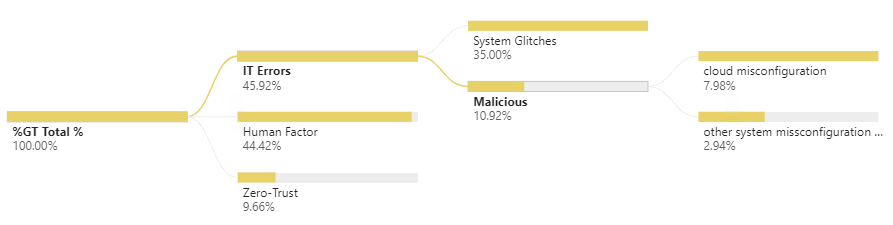
Addressing these root causes requires a higher investment and the drafting of a comprehensive cyber security strategy, it may also require an important aspect of change management to modify IT business practices, including the automation of security management.
To achieve a proactive versus reactive stance towards emerging cyber security risks, organizations can benefit by moving towards a zero-thrust, defensive architecture design. Implementing these types of changes can deliver higher resilience and lower running costs.
Zero – Trust: The remaining cases
Data shows that 7% of all Data Breaches happened through a vulnerability in a Third-Party software and another 3% from a malicious insider.
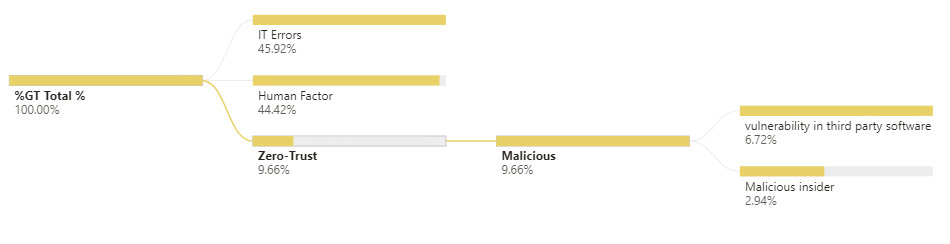
The later is probably one of the most difficult to protect against, identify, and contain. However, the reliance on a zero-trust design where no one person can extract a full data set is one of the potentially only ways to mitigate the risk.
Unfortunately, the increase in cloud based third-party vendor software has the potential to increase an organization's exposure to data breaches originating from elements not within their control. A careful third-party software vetting process, contracting clauses, and insurance requirements need to be put in place to limit and mitigate these remaining risks.
Summary:
While often not reported by news outlets, data breaches happen in small-medium enterprises, with a disproportionate cost versus income in smaller organizations.
Risks and impacts can be efficiently mitigated through the use of an adequate strategy revolving around employee training, cyber security strategy, and third-party risk management.
Cloud migration and remote staff do result in an expected increase in data breaches.
Careful considerations and the definition of a tailored security and authentication framework should be conducted before moving an organization to the cloud and allowing employees to work remotely.
Where we can help:
Crowe MacKay has the expertise and experience in reviewing an organization's cyber security risk profile, proposing strengthening action and auditing the resulting environment.
Our team has also developed an innovative retro-fitting methodology to strengthen less secure applications and systems without requiring expensive changes.

