Cyber Security while your team works remotely
The novel coronavirus has disrupted the way we operate, and the implementation of social distancing has resulted in a larger number of employees working from home. With the increased amount of remote work comes an increased risk in incidents related to cyber security.
Below we have listed key considerations for managing your cyber-security risk with a working-from-home team.
Using personal computers or non-hardened company computers
If your team is using their personal computers to work from home, or a laptop you provide to them, but that has not been “hardened” by stringent security policies, the following elements have to be considered:
Where do you save data?
Are your team members saving the files they work on directly on their computers, or do they only access them via a secure portal? Saving data on someone’s personal computer can have significant data privacy and cyber security implications since your company does not control the data anymore. Loss can occur through your team members’ human actions.
Is your data encrypted?
Are you encrypting the data saved on the computer? Is the password to decrypt the data only known by you or also by someone else in the company?
How do you access your emails?
Are you forwarding your company emails to your personal address? Are you accessing your company’s email address via an application on your computer (i.e. Outlook)? In both cases, this increases your risk since data is no longer stored within the company controlled email accounts, but directly on your local or personal data repository. Company data loss can occur if your personal account or computer is hacked.
What else runs on your computer?
What other software is running on your computer? Do you use your computer for personal browsing, sharing memes, or video streaming? All of these items have a higher risk of containing viruses and malwares, increasing the risk of exposure to your company.
What type of antivirus runs on your computer?
Is your antivirus software up to date? Are you using a reputable antivirus provider or relying on a “free” version. Selecting a proper antivirus software and scheduling frequent antivirus scans are primordial to reducing your infection risk.
How is your data backed-up?
In the event you are using personal computers for work, how do you back up the data back to the company? Do you have a mechanism to retrieve files in case of a hardware failure or a Ransomware attack? It is important to provide team members with the tools and mechanisms to ensure the files they use for work are backed up from their personal computers to your company data repository (cloud or on premise).
Network and communications when using your company provided laptop or your personal computer
Is your home WiFi network really secure?
Is your home network really secure? Have you modified the admin password of your WiFi router? Have you created a strong password for your personal WiFi? Have you changed the name of your WiFi from the one provided originally? All these items are important to reduce the risk of someone entering your home network to access your personal and company data.
Do you use a Virtual Private Network to connect to your company applications?
Virtual Private Networks (VPNs) are implemented by installing a VPN software on your computer to access a remote server. The power of a VPN is that all data leaving your computer will be encrypted until it reaches the server, significantly reducing the risks related to cyberattacks. However, when choosing a VPN, careful considerations need to be made in respect of the provider’s reputation, the price (i.e. “free” may be dangerous), and the provider’s country of incorporation.
Use of cloud based applications
Your company may be relying on cloud-based applications for its operations (i.e. Office 365, Google Suite). Such infrastructure provides great flexibility and collaboration. However, if you have only implemented them for the sole purpose of providing an easier remote working environment to your team, the following questions need to be considered:
Do you know in which country your data is saved?
Do you really know where your data is being stored for both the live and the back-up data? Some information cannot be stored in a foreign country data center without your clients (and staff) being made aware, and additional controls need to be put in place.
How do you know if a critical file is shared with an external party?
With cloud applications, it becomes easy to give access to a file/folder to someone else. Do you have a monitoring mechanism in place to detect when a critical file or folder in your cloud environment has been shared with a third party? Or whether you have removed an ex-employee from the access list?
Who controls the security?
Have you assigned someone to be in charge of reviewing file accesses?
Privacy is key - protect your personal information
Working remotely might mean that you are using your personal devices and logging into both work-related sites as well as personal sites. This makes you more vulnerable to a cyberattack because you are a target with both valuable corporate information, as well as personal information. Be very careful. Your personal information is a highly sought after asset. We are seeing increasing occurrences of cyberattacks targeting individuals working from home. Here are some ways to minimize your risk exposure:
Only perform transactions on a secure, password-protected network.
We discussed the importance of using a VPN earlier. You can add the additional layer of security by never carrying out transactions over the internet using a public, or shared network. If you do not have any other choice, then ensure you are using a reliable VPN.
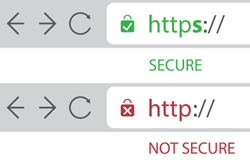
Only access and work on websites that use encrypted connections.
Data transferred between your browser and the website can be encrypted using SSL encryption, ensuring that the data in transit cannot be read. This is fundamental for any activity you carry out on the internet.
See below images to identify the difference between a secured and an unsecured network.
Do not use the same password for work and personal accounts
Cybercriminals monitor the activities of their targets to gather information of sensitive information to take advantage of (including bank accounts, social media accounts, government account activity). The first thing a hacker will do once they obtain one of your passwords, is to try and use it for the rest of your accounts. Prevent this by using unique passwords for everything.
Use chat apps with strong encryption.
Apps like Whatsapp and Signal have increased security that prevent people from spying in on your conversations.
Log off when you’re done.
Always log out of every online account when you have finished using them.
Revise your social media privacy settings.
You’ll be surprised how much information a cybercriminal can gather from your social media accounts such as Facebook and LinkedIn. As an example, your public profile picture that you innocently posted from your home can be linked to an IP address allowing your location to be exposed.
How we can help:
Cyber security and data privacy are not a one-size-fits-all. Numerous considerations need to be taken to identify the most cost-efficient approach to reduce your cyber security and privacy risks, while having your team work efficiently from remote locations.
Crowe MacKay experts on our Risk Advisory and Technology Consulting teams can assess your particular situation and provide you with an assessment and recommendations to protect your company from serious data loss and reputational damage.





